Overview
Type: Trojan
Destruction Level: Moderate
Prevalence: Moderate
Malware Names
- Trojan.Win32.Mornhya (Padvish)
- Powershell/Kriptik(Eset)
- Trojan.Bat.Alien(Microsoft)
What is Trojan?
Trojan is a type of malware that disguises itself as clean and legitimate software and behaves totally like a useful and functional software, but when executed, it causes a lot of damage to the computer system. There are different ways in which trojans could enter the system, some are: Entering through a software downloaded from the Internet, embedding in HTML text, attaching to an email, etc.
What is Mornhya malware?
Mornhya is a obscured batch file (typically with a .cmd extension) that, upon execution and after disambiguation, executes a miner file. The malware employs various techniques to evade detection and monitoring by security tools. In observed cases, samples of this malware have been downloaded from the following addresses, often disguised as software cracks:
hxxp[:]//89[.]23[.]97[.]199[:]1444
hxxps[:]//89[.]23[.]97[.]199
Technical Review
Indicators of Compromise (IoC)
Presence of a .cmd file in the `%programdata%\Microsoft%` path, with names seen in different malware samples such as:
WinDriver.cmd
Anonmy.cmd
Project88.cmd
High CPU usage by the `explorer.exe` process or `xmrig.exe` program process.
System processes internet connection to the following mining domain (e.g., `powershell.exe`, `explorer.exe`, or `xmrig.exe`)
pool[.]hashvault[.]pro
Performance Description
Mornhya malware is a batch file that ultimately executes a miner on the victim’s system. This file is obfuscated and disambiguated in several stages. Initially, the malware runs a command-line command, creates a subprocess `powershell.exe` to execute an obscured code fragment:
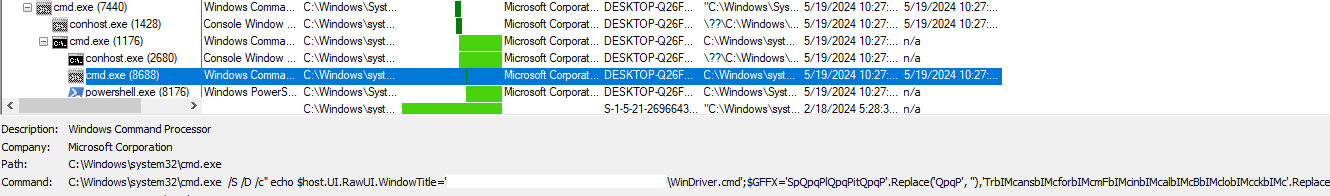
After disambiguation, the PowerShell code snippet is as follows. The malware first reads the pseudocode in the original file, decrypts it using the AES algorithm, and then decompresses it from GZip. By executing this code, two malicious PE files are obtained and loaded directly into the `powershell.exe` memory process.
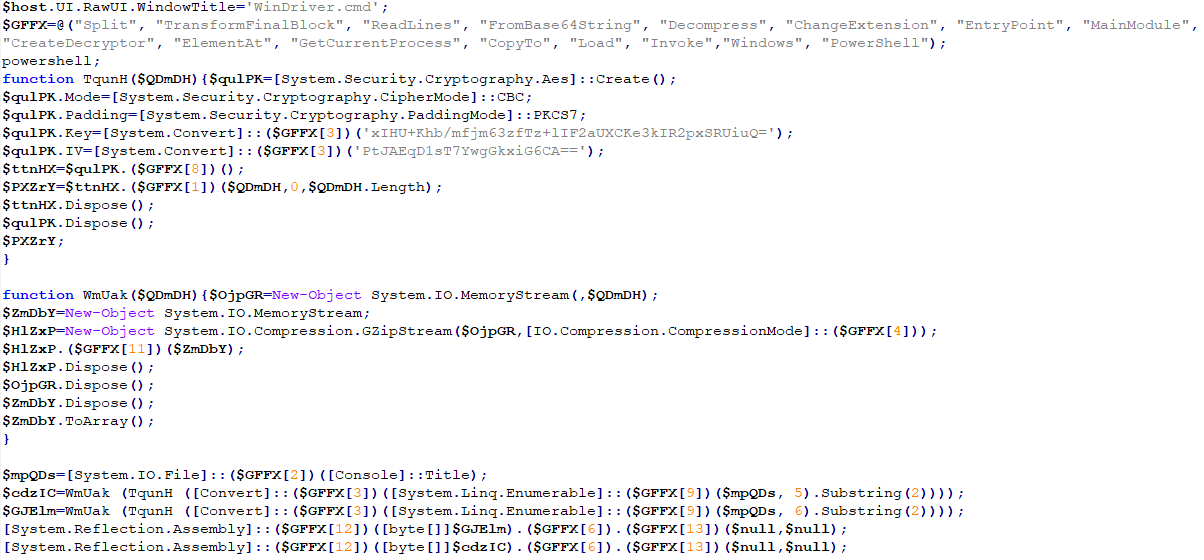
The first file (referred to as AMSIPatcher) employs various techniques to bypass antivirus and other security tools. Once the first file is executed, the second file is loaded and executed within the `powershell.exe` memory to run the `xmrig.exe` miner.
?The First File: AMSIPatcher
Mornhya malware, in AMSIPatcher.exe file, uses the following techniques to bypass antivirus and monitoring tools. The following figure presents a code sample of AMSIPatcher:

- Upload clean Versions of kernel32.dll and ntdll.dll Files: The malware locates `ntdll.dll` and `kernel32.dll` modules among the uploaded modules of the `powershell.exe` process. It also loads clean versions of these files into the malware process memory, then it changes the start address of the code in these modules to the start address of the clean versions it has uploaded. This allows the malware to bypass hooks that may have been applied to the functions of these two modules during the creation of the `powershell.exe` process.
- AMSIScanBuffer Function Code Modification: The AMSIScanBuffer function from the `amsi.dll` library, is used to scan buffer contents in the memory. The malware modifies the initial bytes of this function to prevent its execution, so the function returns without running the original code. For example, in 64-bit Windows, the malware rewrites the initial bytes with [184, 87, 0, 7, 128, 194, 24, 0] bites, whose assembly equivalent command is shown below.”

- EtwEventWrite Function Code change: To avoid logging its own process events, the malware changes the initial bytes of this function in the `ntdll.dll` module to [194, 20, 0] in 32-bit Windows and [195] in 64-bit Windows. This is equivalent to the “”ret”” command in assembly language, making the function return immediately without executing its code
?The Second File: Miner
The miner file varies in different malware samples , but ultimately executes the `xmrig.exe` mining tool on the victim’s system, typically using the following address as a mining pool:
pool[.]hashvault[.]pro
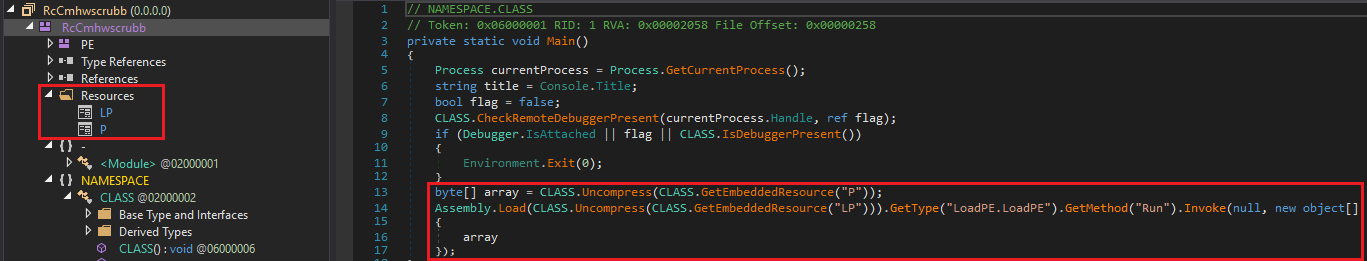
For instance, in one malware sample, the malware miner file is based on the .NET framework and contains two malicious resources similar to the following figure. The first resource, LP resource in the following figure, is a malicious library file named `LoadPE.dll` that executes the second resource, P. Resource P is a malware that, upon execution, creates a subprocess with a clean Windows file `explorer.exe`, and injects the `xmrig.exe` miner file into it.
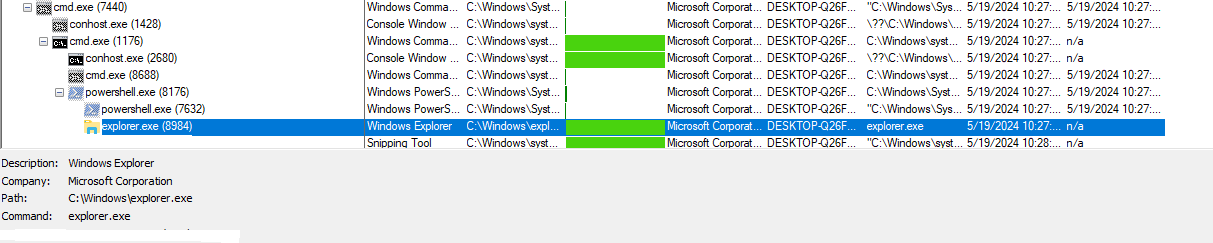
The following figure illustrates the malware execution:
How to deal with and clean the system?
Padvish Antivirus detects and removes this malware from the system. It is recommended to:
✅ Always keep your OS and antivirus up to date.
✅ Download files only from reliable sources.