Overview
Type: Hacktool
Destruction Level: High
Prevalence: Low
Malware name(s)
- HackTool.Win32.ASPXSpy (Padvish)
- HackTool.Win32.ASPXSpy (Eset)
- Backdoor:MSIL/AspxSpy.A (Microsoft)
What is a hackTool?
Hacktools are tools designed to facilitate intrusion. These tools can be used by an intruder to recieve data from the victim organization’s network. These tools are commonly used to retrieve the credentials of sensitive victim servers. For example, an intruder can use hacktools to guess passwords based on Brute Force attacks. In some cases, to escalate access levels and exploit existing vulnerabilities, HackTools are used. In general, hack tools can crash the computer and network security barriers and provide various capabilities to infiltrate systems.
What is ASPXSpy malware?
ASPXSpy is a web-based hack tool written in the ASPX programming language. It has been developed and is accessible as open-source on the Internet. Once installed on the victim’s servers, this tool enables the attacker to retrieve the victim’s server specifications, conduct port scanning operations, manipulate the victim’s file system, registry, and database, and execute command-line CMD as desired by the attacker.
Technical review
Indicators of Compromise (IoC)
The signs of infection (or IoCs) can vary based on the commands received from the attacker.
Performance description
This tool initially receives the password from the attacker through the following login form and subsequently grants attacker, access to the implemented functionalities. In the provided examples, the password is the string “admin”.
 ? The image below presents an example of the features of this tool
? The image below presents an example of the features of this tool
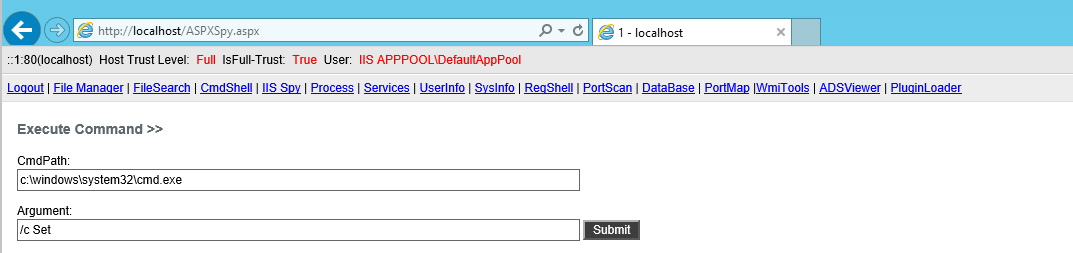
?As shown in the image above, the ASPXSpy penetration tool provides various features and capabilities to the attacker, which are described in the table below:
| Feature | Description |
| File Manager | Provides the ability to manage the file system of the victim’s server, including deleting, creating, editing, renaming, copying, changing file timestamps, and downloading/uploading files. |
| File Search | Enables searching and modifying the content of any file on the victim’s server. |
| CmdShell | Allows execution of command-line cmds specified by the attacker using cmd.exe, with the output sent back to the attacker. |
| IIS Spy | Displays the web server details, including usernames and passwords, extracting items such as the web server name, domain name, IP address, and port number assigned to the web server. |
| Process | Displays the list of the system’s current processes, including the process name, ID, number of threads, execution priority, and the ability to terminate them. |
| Services | Displays the list of services registered in the system, including the name, corresponding process ID, path of the executable file, current state of the service, and its start state |
| UserInfo | Displays system users and their details. |
| SysInfo | Displays system information, including OS information, hardware specifications, information about installed drivers, and MAC address(es). |
| RegShell | Allows access to the victim server’s registry, enabling the viewing, deletion, creation, and editing of registry keys. |
| PortScan | Enables scanning of desired ports on the current server or external servers. |
| DataBase | Provides the ability to connect and execute queries for MSSQL and OleDb databases. |
| PortMap | Facilitates Port Forwarding operations, mapping remote connections to IP addresses and local ports. |
| WmiTools | Allows connection to the namespaces of the victim server and execution of WMI queries. |
| PluginLoader | Uploads a file into the current processor memory. |
| ADSViewer | Enables viewing of the active directory of the victim server along with their features and subdirectories. |
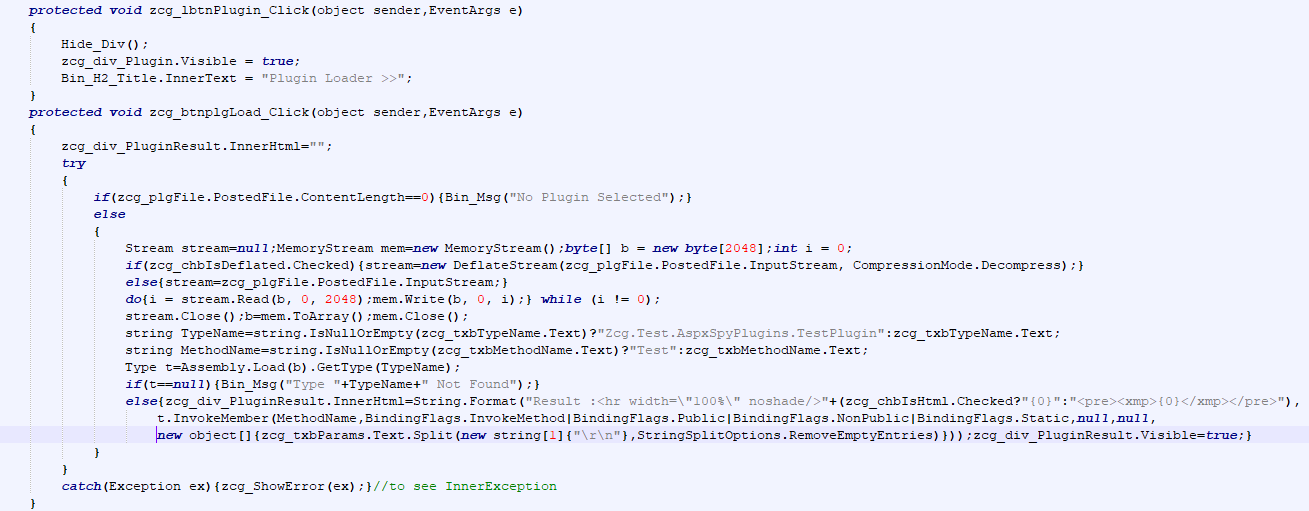
?In the image below, the code related to the PluginLoader feature is presented in a sample of this malware.
How to deal with and clean the system?
Padvish antivirus can detect this malware and remove it from the system. It is also recommended to regularly update your operating system and antivirus software.