Overview
Type: Trojan
Destruction Level: Moderate
Prevalence: High
Malware names
• Trojan.Win32.Andromeda
• Downloader.Win32.Andromeda
What is a Trojan?
Trojans are malware types that introduce themselves as healthy and legal software and act similarly to practical and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching it to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is Andromeda trojan?
Andromeda malware has the nature of the bot that by connecting to the network and injecting code into the victim’s healthy processes, it can download and execute other malicious files, as well as it can steal information from the victim’s system and send it to specific servers. This malware is a bot instance of the Gamarue malware suite.
Technical information
Signs of infection
Symptoms of infection with this malware include the following:
- Injecting a malicious code in one of the following running processes and there is no Parent for these processes:
- msiexec.exe
- svchost.exe
- wuauclt.exe
- Existence of malware with random and volumetric names over 70 Mb, which is hidden in the following paths:
%SystemDrive% \ ProgramData
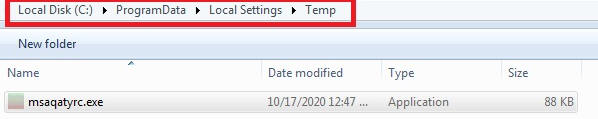
%AppData% \ Roaming - Existence of a file with ‘ms’ letters that starts its operation in the following path:
“%SystemDrive%\ProgramData\Local Settings\Temp\ms**...**.exe” - The malware creates a copy of itself winlogonr.exewhich is placed in the following path:
“%AppData%\Roaming\winlogonr\winlogonr.exe"
Describing Performance
In this section we will analyze two old and new versions of this malware:
-
Performance_1
This malware is a http_based bot that after infecting the system, it connects to the bot network. This bot is modular and if necessary, it downloads the module from its server and updates them.
The malware file size is large and varies from sample to sample. The malware appears to have the ability to modify the contents of its files and 70MB of it is useless content (according to the reviews during the analysis, it seems that the volume of the main content is only 5KB approximately) This prevents it from being detected by antiviruses. On the other hand, due to its high volume, the malware cannot be detected and checked on analytics sites.
The authors of the malware have made every effort to provide examples of this malware from packers and decoders and used different methods to make it difficult for antivirus to detect.
Initially, the malware disables the “Windows error notifications”. It then checks the languages installed on the victim system. Below is a list of countries that Gamarure does not intend to run on their systems.
-
Ukrainian
-
Belarusian
-
Kazakh
-
Russian
Installed languages on the system will be checked in different parts of the program to prevent some malicious activities in Russian, Ukrainian, Belarusian, or Kazakhistanian. Malware uses Network Time Protocol (NTP) to get the current time. To do this, it’s going to the NTP domains and receives the time, so, it starts from the first domain mentioned below and if it fails, it will continue its efforts with other domains.
• north-america.pool.ntp.org
• south-america.pool.ntp.org
• asia.pool.ntp.org
• oceania.pool.ntp.org
• africa.pool.ntp.org
• north-america.pool.ntp.org
• pool.ntp.org
-
Performance_2
You can view the Andromeda process in the following image. This malware injects malicious codes inside the svchost.exe or wuauclt.exe processes.
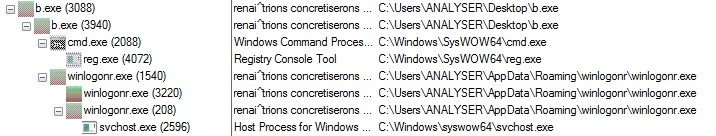
Also, it can contain the following extensions:

In some paths, it also copies itself with a name containing ‘ms’ letters:
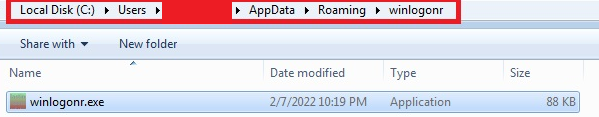
"AppData%\Roaming\winlogonr\winlogonr.exe%"
Registry changes:
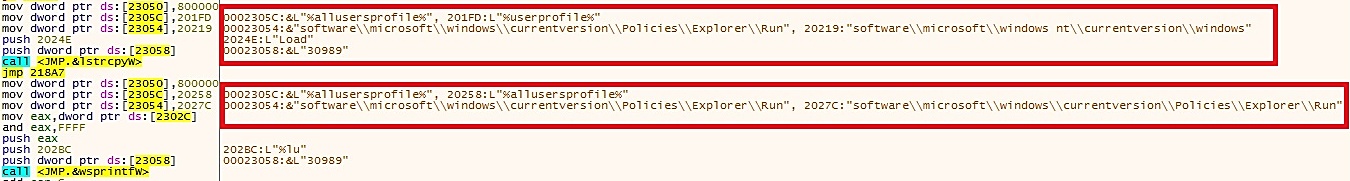
This malware performs changes in the registry to remain on the system so it can automatically operate after each OS boot.
HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\windows
Value Name: Load
Value Data : %userprofile%\Local Settings\Temp\ms<%s>.<%s>
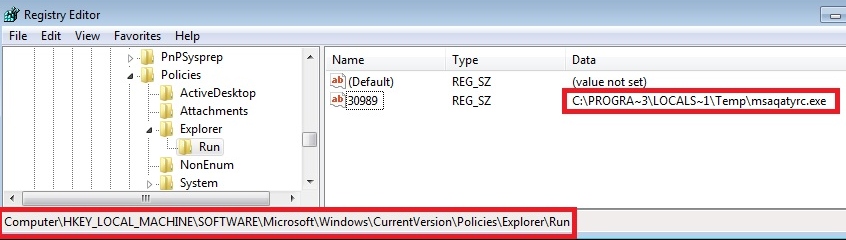
HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\Policies\Explorer\Run
Value Name: <%lu>
Value Data :%allusersprofile%\Local Settings\Temp\ms<%s>.<%s>
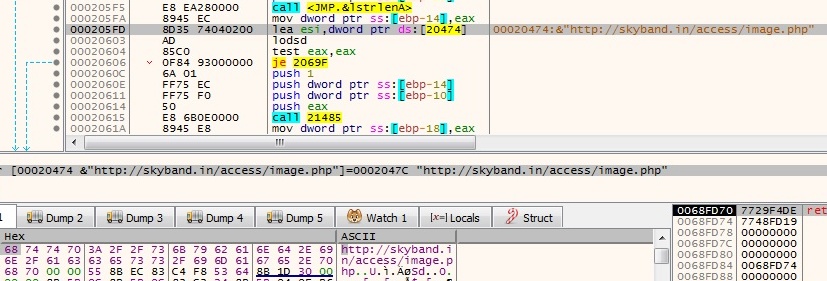
Network connection:
This malware tries to connect with its C&C which you can view its address in the following image:
The Andromeda transacted packets with its C&C is as follows:
- first format:
- “id:%lu|bid:%lu|bv:%lu|sv:%lu|pa:%lu|la:%lu|ar:%lu”
- Id: produced data from system file
- bid: defined constant value inside the bot
- bv: defined constant value inside the bot
- sv: the victim’s OS version
- pa: to assign if the OS is 32 or 64 bits
- la: produced value based on www.update.microsoft.com IP address
- ar: determines whether the bot is executed with admin privilege

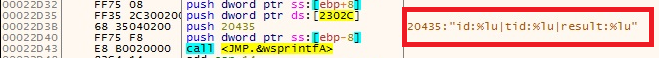
- Second format
- id:%lu|tid:%lu|result:%lu
How to deal with it and disinfect the system
Padvish Antivirus detects this malware and removes it from the system. Padvish Intrusion Prevention System (IPS) prevents network attacks by this malware and its connection to your server. It also detects files downloaded by this malware. Therefore, to prevent infection with this malware, it is recommended to prevent malware from entering your system by installing Padvish.