Overview
Type: Hacktool
Destruction Level: High
Prevalence: Low
What is Hacktool?
Hacktools are tools designed to facilitate intrusion. These tools can be used by a hacker to siphon data from the victim organization’s network. These tools are commonly used to retrieve the validation information of sensitive victim servers. For example, a hacker can use tools to guess passwords using Hacktool based on Brute Force attacks. In some cases, to increase access levels and exploit existing vulnerabilities, HackTools are used. In general, hacking tools can crash the computer and network security barriers and provide various capabilities to infiltrate systems.
What is Xwo malware?
Xwo Is a Python-based robot that utilizes default web services and scans passwords in the ftp ،mysql ،postgresql ،mongodb ،redis ،memcached ،Tomcat ،phpMyAdmin ،VNC And RSYNC forms. The name of this tool is derived from the name of its main module. Xbash and MongoLock malware use this Hacktool as a tool to extract information. After finding the desired passwords, the malware sends them to its Commands and Control Server.
Technical Explanation
MongoLock ransomware attacks MongoDB servers and extorts users to retrieve the data. Xwo And MongoLock Both use the same Python-based code and overlap in C2 infrastructure. Unlike MongoLock, the Xwo tool has no ransomware capability but sends the stolen information to its C2 server.
Signs of infection
Signs of infection include network connections. The malware is trying to connect to the following addresses:
• s [.] propub3r6espa33w [.] tk
• s [.] Blockchainbdgpzk [.] Tk
• s [.] Pcrisk [.] Xyz
• s [.] Rapid7 [.] Xyz
Description
This tool first scans the network range provided by the command and control server. It then begins to gather information. First, it requests an HTTP POST with a User-Agent from a random list of coded options. This scanner uses encrypted code to obtain a list of command and control servers:
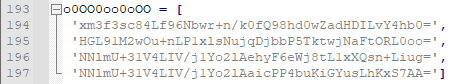
Xwo aimed to check default passwords in MySQL ،PostgreSQL ،MongoDB ،Redis and Memcached databases. As shown in the image below, the code of this tool contains a dictionary of weak and known passwords so that if the user’s password matches one of them, it will send it to the server.
If it finds an Apache Tomcat scanner in the system, it uses a module to check for improper configuration and default passwords. Additional information such as default routes SVN ،Git and backups are also collected.
Example of validation test modules for tomcat:

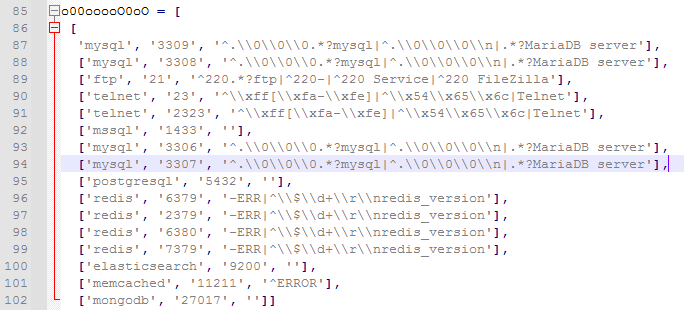
List of ports used for targeted malware:
How to deal with it and disinfect the system
Padvish Antivirus detects this malware and removes it from the system. Also, some policy implementations can prevent these attacks to the maximum. The most critical security measures to be taken in any network are as follows:
- Update antivirus and review intrusion reports regularly
- One of the ways this malware infiltrates is to take advantage of non-compliance with the necessary security policies regarding databases. Therefore, it is recommended to take the following measures seriously:
- Change the default username and password immediately after installing the databases
- Lock accounts that are not in use. Remove them if you are sure you will never use them again.
- Use strong passwords
- Delete unused accounts as well as delete public access from all accounts
