Overview
Type: Trojan
Destruction Level: Moderate
Prevalence: Moderate
What is a Trojan?
Trojans are malware types that introduce themselves as healthy and legal software and act similarly to practical and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching it to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is the Fakeapp malware family?
This family usually, introduces itself as legit and useful applications. This family mostly aims to earn through displaying ads, redirecting users to install other apps, registering users in application subscribing services, sending and receiving value-add SMS service, and downloading and employing other apps on the user’s phone. This app does not act as they claim, for example, an app from this family that introduces itself as an antivirus will detect all other antiviruses as malware.
In the following, we will examine two members of this family: FakeMinerAd and FakeMinerPay
Technical explanation
The “Bitfunds” is a FakeMinerPay and the “Bit Plus” is a FakeMinerAd.
Bitfunds
The package name of this malware is com.task.cryptocloudpro. It claims to mine cryptocurrencies. It pretends it can mine Bitcoin, Bitcoin Cash, and Ethereum and it convinces the user that it’s a legit app by simulating a mining environment. Also, it forces the user to subscribe in order to enhance mining capacity. The user will not mine any cryptocurrency but has to pay for a subscription without earning or mining any currency. Lately, Google removed this app from its list but it’s still downloadable from third-party stores.
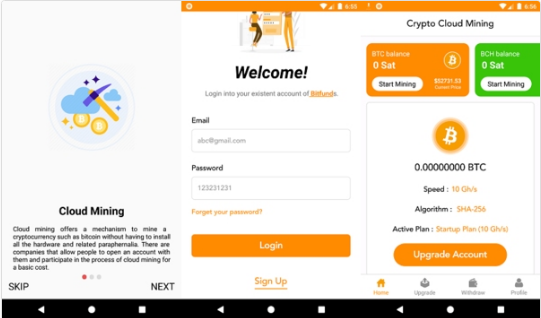
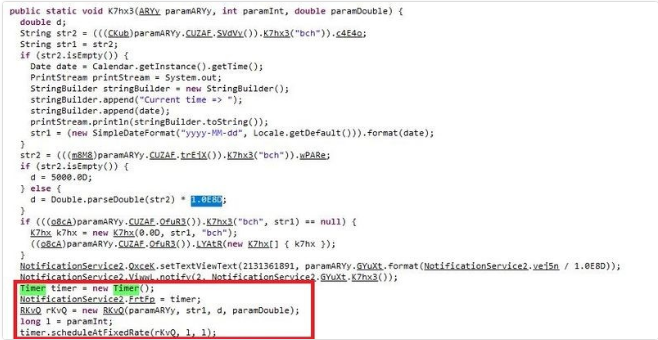
The main activity, first recalls the ‘howitworks’ activity which gives a brief explanation of how the app works. Then, it recalls ‘MainActivity’ to mine 3 main currencies along with LoginActivity to log the user into the app. If the user already registered, he/she will receive login information through email otherwise, the user will enter the SingUpActivity by clicking on the ‘SignUp’ button. After launching the app, it will check the network connection. When the user clicks on the “start mining” button, the “miner counter” will be displayed with 3 seconds delay which is a simulation of the mining procedure, but the app must be connected to a mining pool to mine any cryptocurrency.
Activities
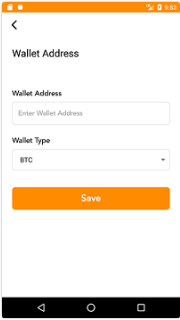
AddWalletAddressActivity
This activity is to add the wallet address for withdrawing mined currencies. Initially, the user clicks on the “withdraw” button, and according to the following image, the app requests for the wallet ID and type. This app does not validate the wallet except for not being empty, but the wallet address is unique with a specific length based on its type. This app does not let the user change the entered address. Legit apps normally, add restrictions on the address field such as minimum and maximum entered characters, defining specific limits of characters, and so on; also the user can change the wallet address. Lack of validation and inability to change the address can be a potential reason for being a validated app and its inability to mine cryptocurrencies.
PaymentCodeActivity
This app will introduce multiple plans to increase the mining speed and decrease the withdrawal limits with different prices. In this activity, instead of redirecting the user into the payment gateway according to the type of currency, it demands the user to enter the wallet address and scan the QR code so the user transfers the plan fee to the developer’s wallet. Because this app cannot mine any currency, the user has to pay for a non-existent service, and then it demands the user to send the screenshot of the payment with the user’s email and the registered ID to the developer’s email which is provided inside the app.

FirebaseMessagingService
The firebase package is for storing data, authentication, the number of installations in the user’s phone, and so on. This service is executing with com.google.firebase.MESSAGING_EVENT action. It means it will be recalled when a message is sent or received. The app collects the phone data such as the brand, the model, the package name of the phone, etc using this action and using this information to authenticate the users, notify the users, and display ads using Google play.
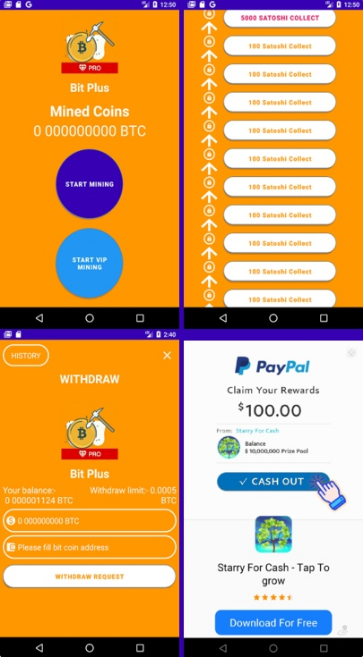
Bit Plus
The package name of this app is cryptominer.bitcoinminer introduces to the users with the aim of mining cryptocurrencies. This app forces the user to watch advertising videos to enhance the capacity of mining, while it does not mine any currency. This app is a FakeMinerAd because it contains fake advertising clicks.
The main activity of the app “cryptominer.bitcoinminer.ui.main.MainActivity” recalls the following method to calculate and display the mining counter that displays the number of bitcoins that are mining. In the app database, the BitPlusPreference variable is defined that is used for the value of the mined cryptocurrencies number counter. It controls the counter value in the app activity using the coroutine method.
public final void y() {
d.e(this, “context”);
d.e(“CounterKey”, “key”);
SharedPreferences sharedPreferences = getSharedPreferences(“BitPlusPreference”, 0);
d.d(sharedPreferences, “context.getSharedPrefere…me, Context.MODE_PRIVATE)”);
b.a = sharedPreferences.getInt(“CounterKey”, 0);
z();
if (this.u) {
b b2 = this.r;
if (b2 != null) {
Button button = b2.e;
d.d(button, “binding.startMiningButton”);
Object object = a.a;
button.setBackground(getDrawable(2131165324));
b b3 = this.r;
if (b3 != null) {
Button button1 = b3.e;
d.d(button1, “binding.startMiningButton”);
button1.setText(getResources().getString(2131624048));
this.s = b.a.f;
this.t = f.q(f.a(i0.b), null, null, new a(this, null), 3, null);
return;
}
d.i(“binding”);
throw null;
}
d.i(“binding”);
throw null;
}
b b1 = this.r;
if (b1 != null) {
Button button = b1.e;
d.d(button, “binding.startMiningButton”);
Object object = a.a;
button.setBackground(getDrawable(2131165323));
b b2 = this.r;
if (b2 != null) {
Button button1 = b2.e;
d.d(button1, “binding.startMiningButton”);
button1.setText(getResources().getString(2131624045));
a1 a11 = this.t;
if (a11 != null)
f.d(a11, null, 1, null);
this.s = b.a.e;
return;
}
d.i(“binding”);
throw null;
}
d.i(“binding”);
throw null;
{
cryptominer.bitcoinminer.ui.withdraw.WithdrawActivity
In this activity, the user must enter values that are fake and there will be no action by entering this specification:
The wallet address to withdraw seemingly mined Bitcoins
The desired value of the user for withdrawing the seemingly Bitcoins
cryptominer.bitcoinminer.ui.vip_mining.VipMiningActivity
The user clicks on the “100satoshi collect” buttons to receive more Bitcoins and after the countdown (this countdown is implemented by ir.samanjafari.easycountdowntimer library) advertising videos will be displayed using com.unity3d.services.ads.adunit library.
If the user watches the video completely, the user can return to the app and receive the “100satosh” reward value in his/her account and the user will redirect to the Google Play page to download the promoted app by clicking on the video.
public void f() {
z(false);
if (UnityAds.isReady(“Rewarded_Android”)) {
UnityAds.show(this, “Rewarded_Android”);
return;
}
int i = b.a;
d.e(this, “context”);
d.e(“CounterKey”, “key”);
SharedPreferences sharedPreferences = getSharedPreferences(“BitPlusPreference”, 0);
d.d(sharedPreferences, “context.getSharedPrefereme, Context.MODE_PRIVATE)”);
SharedPreferences.Editor editor = sharedPreferences.edit();
editor.putInt(“CounterKey”, i + 100);
editor.apply();
B();
{
Multiple methods in recognizing fake mining applications
Read all comments in the store. Note that most of the 5-star positive comments are fake. Then, read 1-star negative comments so you can know about the app problems before purchasing.
Falsely, enter your wallet address. Based on research, most of these apps do not check your address and take any and every character as correct.
When the app is mining, restart your phone; fake apps will show zero value after the restart.
Read the privacy policy of the app. One of these applications explained, it is for entertainment and has no commitment to pay the user.
How to deal with this malware and disinfect the system
- Padvish antivirus can detect this malware
- Keep your phone up to date, adjust it so it can update itself automatically
- Pay attention to permissions. If they seem more than app functionality, avoid installing the app.
- Only download from authenticated markets and avoid installing apps from Telegram channels, Instagram, or other unauthorized stores. Also, avoid clicking on suspicious links through SMS.