General Explanation
Type: Trojan
Degree of destruction: low
Prevalence: high
Used Vulnerability: CVE-2017-8570 and CVE-2017-11882
Names of the malware:
Trojan.Win32.AgentTesla.a(Padvish)
Trojan.Win32.AgentTesla.cG(Padvish)
Trojan:MSIL/AgentTesla.AL!MTB(Microsoft)
AgentTesla-FCYX!72D3FB6A5E15(McAfee)
What is a Trojan?
Trojans are malware types that introduced themselves as healthy and legal software and act similarly to practical and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching it to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is Agent Tesla malware?
Agent Tesla is a type of Trojan that generally distributes through malicious Office files attached to emails, and its main activities are collecting pressed keys, mouse movements, different login information, stored data in the clipboard, snapping the victim’s desktop, and sending all of this information to its server. Agent Tesla files contain a set of quantified variables that malware uses at the time of execution to embody which one of the malware features must be executed.
Technical Explanation
Signs of infection
One of the signs of infection to this malware is:
a screenshot in the %AppData% path; for example, in C:\Users\*\AppData\Roaming\ScreenShot\ScreenShot.jpg
a file with a name similar to a log. tmp that is updated by pressing a key on the keyboard or moving the mouse.
Registry key to automatically run malware which is generally in the %AppData% path.
Action
Removing the monitoring processes
Hence, this malware protects itself from any monitoring software that tries to detect and remove these kinds of software. Accordingly, it compares the name of system processes or the existing windows with the list of any monitoring software, and it will end the process if it can find any match in the list. The following list is one of the processes that Agent Tesla malware ends them.
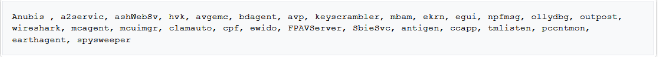
Collecting information
Agent Tesla can collect vast information from the victim’s system. The following items are repeated and every few seconds or minutes are collected and sent to the malware server.
taken picture from the victim’s webcam (if it exists)
Registered screen shito from the victim’s desktop
Existing data inside the clipboard
Pressed keys and the movements of the mouse
Malware strives to send the extracted registered username and password from different software in the victim’s system.
The following software is among the software that malware tries to steal their information.
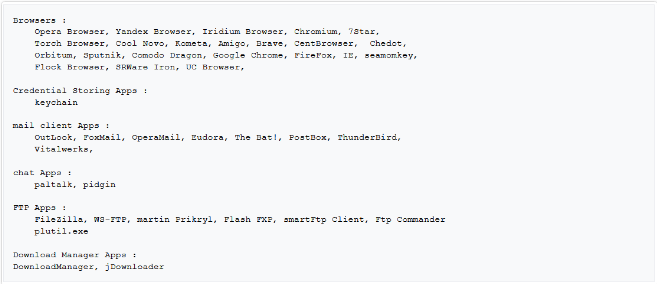
specifications of the victim’s system will send to the server as sending package:
current username
PC name
Operation System version
Processor specifications
RAM storage space
The IP address for the victim’s system
The malware connects to its server through the following methods:
HTTP protocol: the malware will send the desired data with the Triple-DES algorithm which is encrypted by the POST method.
SMTP protocol: collected information will be sent in the form of an HTML file to the embedded email in the malware file.
FTP protocol: the malware will upload the stolen data on its FTP server
Telegram channel: the malware will send the collected information to a telegram channel.
The other features of this malware
AgentTesla malware has other features upon the existing configuration variables which decide whether to run them. These features are:
upgrading the access level using the following registry keys:
“HKCU\software\classes\ms-settings\shell\open\command”
“HKCU\software\classes\mscfile\shell\open\command”
disabling some of the managing tools of Windows OS such as Task Manager, Folder Options, Run, Control Panel, cmd.exe, and regedit.exe
Distributing malware to Removable and CDRom drives: a version of the malware will place on these drives. The malware hides all files and directories and symmetrically creates a ‘.ink’ file for each file which will run the malware with a click.
Running the execution files: the malware extracts the existing files inside its Resource section and as the new process.
Downloading desired files, storing them inside the Temp folder, and also executing them.
Removing the malware from the victim’s system
Periodically, the malware sends the “uninstall” command to its server and it will remove itself if acceptable. Then we have the following patterns:
removing the malware file by moving it to the Temp folder
removing the adjusted registry keys for the malware
ending the malware processes
in some cases, it will shut the system down.
How to deal with this problem and disinfect the system
Padvish antivirus will detect and prevent this malware. It is recommended to prevent opening any suspicious emails, according to that one of the main ways to distribute this malware is through email attaches. Also, use updated Office software.