General explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
Names of the malware:
- Trojan.Win32.Powersing.lnk (Padvish)
- TrojanDropper:Win32/Zervbee.A!attk (Microsoft)
- LNK/TrojanDropper.Agent.K (ESET-NOD32)
- Powersing!D83F933B2A6C (McAfee)
What is a Trojan?
Trojans are malware types that introduced themselves as healthy and legal software and acted similarly to helpful and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, embedding HTML text, attaching to an email, etc. are ways that trojans use to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is Powersing malware?
DeathStalker group is a team of malware programmers who distribute their malware to collect important data from financial and law firms. This group created malware based on Powershell by the name of Powersing collects data such as computer name, antivirus name, and OS version and sends them to its server along with regular screenshots. Also, it will detect malware analysis and its environment when running, and if it was inside the VM environment, it will end its execution without infecting the system.
Technical explanation
Signs of infection
- There is a shortcut “Microsoft Windows Helper” in the following path:
AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
- There is a hidden folder named “~.tmpF291” in the C:\ProgramData path in the different samples of this malware, the amount after tmp has various names.
- powershell.exe process is in the running processes list, and after each system restart, cscript.exe and powershell.exe will run.
Explaining the action
This malware spreads through the system by phishing mail with an attached file including an infected shortcut (powersing). The file appearance is similar to a PDF file, but after running, it will execute cmd.exe and PowerShell and start its malicious operations. For confusing the user, at the same time, it will transfer a healthy pdf file to the system and run it.
Executing analysis tools and VM detection technique
The malware tries to detect, by researchers analyzing the network packages by running some techniques on whether a VM executes on the system or whether the system contains tools such as sniffing or Wireshark and Nmap that are used regularly. If the malware is executed on the VM or the system involves analysis tools, it will stop the main functions of the malware.
Decoding and executing malicious codes
The transferred malicious PowerShell by this malware is encrypted, and to decrypt them, the client needs keys. The malware programmer will save the stolen data and server address that received stolen data on web services such as youtube, Twitter, and other social networks. You can view the procedure in the following image:
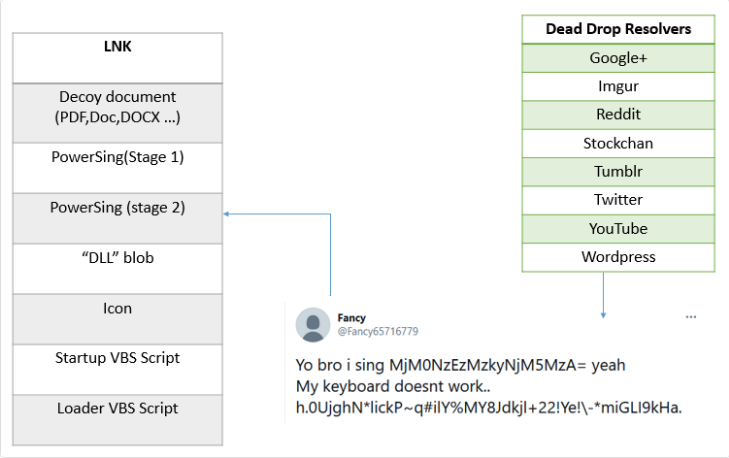
If the malware cannot connect to these web services and doesn’t obtain the key, the malware’s malicious codes will be coded in a file, and it’s not executable. If the malware connects to the network and web services, it will use the obtained key to decrypt a file. The malware uses an asymmetrical algorithm to encrypt and decrypt codes, and eventually, this file will be executable. After execution, the malware will collect information including computer name, antivirus name, and system version, and will take regular screenshots from the victim’s system and sends them to its server.
The permanence of the malware
It will create a shortcut file named “Microsoft Windows Helper” in the windows startup path that leads to the malware execution every time the system boot.
How to deal with it and disinfect the system
Padvish Antivirus will detect this malware and disinfect your system. The following items are for preventing this malware infect the system:
- Update the Windows and other installed software on the system
- Deactivating and restricting the execution of unnecessary scripts
Using WSF, VBS, JS, SCR, and PSI scripts is one of the increasing procedures in malware as the first level of infection. According to the restrictions of email service providers in sending execution files and for bypassing signature-based antiviruses, malware programmers use ambiguous scripts.
- Informing and training employees to avoid risky behaviors
Employees should have sufficient training to avoid risky behaviors, such as opening the email attached files, visiting unknown sites, or clicking on suspicious links, and avoid receiving files from unauthorized resources (downloading the cracked files of software and games, updating versions, etc. from unauthorized resources)