General explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is a Trojan?
Trojans are types of malware that introduced themselves as healthy and legal software and act similarly to useful and applicable software but cause many destructions to the system when executing. Trojans, normally, act as a Backdoor for hackers/attackers to access the system, after being installed on the user’s phone. For instance, the malware we are going to analyze seems to do a useful job but installs an unintentional application on the system.
What is the Basbanke malware?
This family of malware is actually banking Trojans which steal information such as card numbers, passwords, the date of the card, etc. but is not only limited to this capability it may do things such as recording the page, accessing SMS, accessing to user’s phone contact, etc.
Technical explanation
The name of the following application is ” Hamrah Bank Mellat” (an application from Mellat bank for online banking services) and it seems exactly like the original application but in the background, it steals banking information and other users’ secret data. Then, it sends all of this information to its infected Command and Control server, by connecting to it. 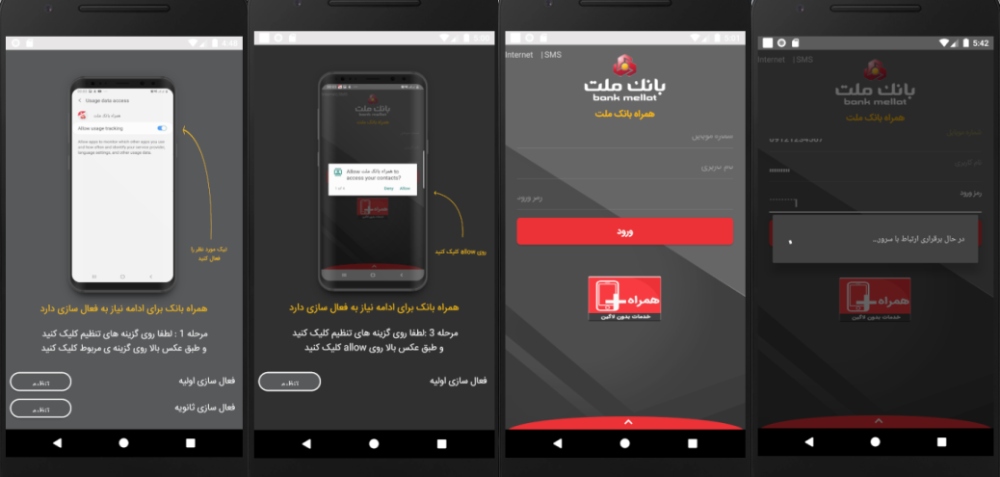
In the original application procedure
This application, at the initial time of installation, encourages the user to grant all permissions with the ” Accept all accesses for better performance” message which is the first step to performing its malicious actions.
The dangerous permissions that this malware receives are:
-
- “android.permission.READ_CONTACTS” (accessing all user’s phone contacts)
- “android.permission.READ_PHONE_STATE” (accessing to user’s phone information)
- “android.permission.RECEIVE_SMS” (receiving SMS)
- “android.permission.READ_SMS” (reading SMS)
- “android.permission.CALL_PHONE” (Making Calls)
- “android.permission.READ_EXTERNAL_STORAGE” (accessing to SD Card)
This malware, in the initial stages of its activity, receives important values such as phone number, username, password, card number, CVV2, the year and month of bank card expiration,
and after the user clicks on the enter button, it will save the information entered by the user in a variable and perform the following malicious actions:
- accessing to SIM card by GetSimSerialNumber()
- accessing to IMEI (device unique signature) by GetDeviceId()
- accessing to IMSI (15 digits unique signature of SIM card) by getSubscriberId()
- accessing to user’s phone number by getLine1Number()
- accessing to system settings by GetSettings()
- accessing to internet connection status by GetDataState()
- accessing to the current registered operator by GetNetworkOperation()
- accessing to the network connection type by GetNetworkType()
- receiving SIM card operator by GetSimOperator()
- accessing to device logs by “LogCat”:
It collects logs from the user’s phone in the “-logcatdata” file and the “system/bin/logcat/” path.
- By assigning a phone number and text message, send an SMS to any desired number by sendTextMessage()
- It can obtain information such as manufacturer, type, and details of the phone by these methods: getProduct, getManufacturer, and getModel
- It can obtain SdkVersion by getSdkVersion()
- The possibility of changing phone sound by SetRingerMode()
- Muting the phone by SetMute()
Also, according to the definition of “android.intent.action.BOOT_COMPLETED” and “android.provider.Telephony.SMS_RECEIVED” actions in the manifest files of the application for one of its application services, it will perform the following malicious actions as soon as it boots the phone or it receives the SMS:
- It will fetch the following values and store them in a variable:
- It obtains the IMEI signature by getDeviceID
- It obtains SIM card numbers by getLine1Number
- It obtains SIM card serial number by getSimSerialNumber
- It obtains an IMSI signature by getSubscriberId
- It activates the “Wakelock” service for its application which keeps the device screen on.
- It collects a list of information such as the number of calls to every client, the last time of conducting calls, the name of the user, number, star signed, user signature, and stored images.
- By analyzing the “android.provider.Telephony.SMS_RECEIVED”, it will fetch the message content (the text and the number), as soon as receiving the SMS.
In the end, it sends all of this collected information in the format of a JSON file to a page named “api.php” in its infected command and control server (hxxps[:]//f**k-Iranian-cyber******[.]xyz) by ready library named Retrofit (a library for HTTP requests in android that can upload files, analyze and requesting permissions, etc).
How to deal with it and disinfect the system
To ensure that the system is not infected, install the Padvish anti-virus database file, keep it up to date, and scan the anti-virus.
Method of preventing phone infection
- Avoid download and install the application from unauthorized resources.
- Note the desired permission, when installing the application.
- Constantly back up the stored files and data.
- Do not use unofficial versions of any applications. Applications such as Telegram and Instagram have many unofficial versions and most of them are released through the Telegram channel.
- Pay attention tath the page you want to buy from is not a Phishing type.