General Explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is Phishing?
Phishing is a social engineering technique that an attacker uses to mislead the user and steals personal information of the user such as username, password, bank card 16-digit number, second password, CVV2 code, etc. The common methods of Phishing are using decisive emails and attaching infected links to emails, social networks, and bank payment terminals. There are multiple ways for Phishing attacks, one of these ways is that the attacker designs a page similar to the bank payment terminal and replaces it with the original page. By adding the address of this fake page in the application which will be attached to social networks for download and by promoting tempting buying suggestions tries to make you enter the fake payment terminal page that they designed and transfer the money. Addresses whose only differences from the original address mean one or two words or used misleading subdomains to create them.
What is GameCo malware?
Users download and install applications “PES 2019 EVOLUTION SOCCER”, “Buying half-price Charge”, “ESET mobile security” and “Games with obscene names” which all have a packagename named “ir.game.co” from social networks. The process of infecting these types of malware is usually through ads of these applications on Telegram channels and Instagram pages. To access more features in installed applications, most attackers persuade users by using in-app purchases.
For instance, in this report, we will check “PES 2019 EVOLUTION SOCCER”. This application claims to give you the possibility of viewing and using the game features by paying the price. But in fact, its payment page is fake and attempts to steal users’ banking information. Also, this application contains an advertising package to show ads inside the application. The malware author has added the fake payment page on free hosts which are generally filtered, so to be able to keep the fake payment page open for the user, it necessitates the user to use an anti-filter to attain application features. For example, to reach this aim in this application, it pretends that “because some offline support servers are abroad, you need to use an anti-filter to execute the application without any problem”
Technical Explanation
After parsing JSON files and executing their codes in the applications, the following goals will be followed:
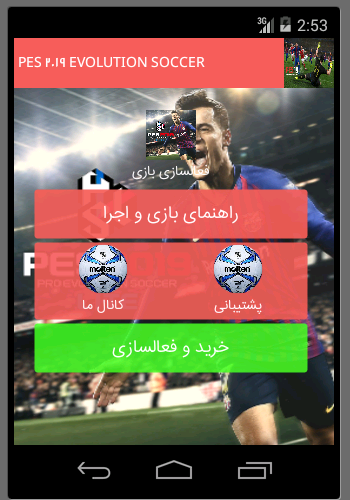
- By pressing the “our channel” and “support” keys, the intent will be sent to the browser by android to open “https://telegram.me/joinchat/AAAAAEFEG5G1Ym_DVHK-Vw” and “https://telegram.me/joinchat/AAAAAEHQb0xPRcm6t3_1qA” addresses.
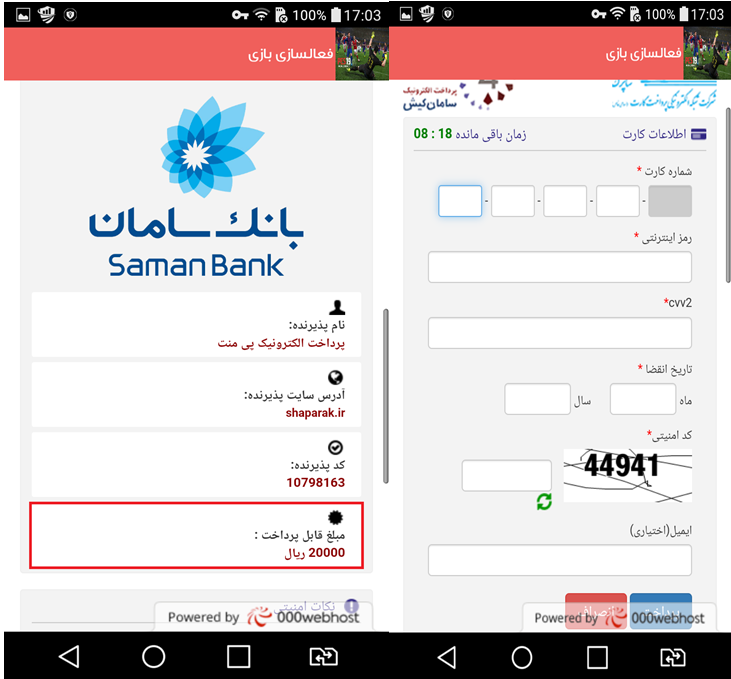
- By pressing the “activating game” key, the intent will be sent to the browser by android to open the “https://newhoster.000webhostapp.com/Source/Saman/payment=5698542365.php?amount=20000” address. This address is the fake payment page that the user refers to.
- If the user clicks on “run game and helps” the related activity is loaded according to JSON file data which is added to the assets/data/1.json path and will be shown to the user. In the provided explanation it is mentioned that: “because some offline support servers are abroad, you need to use an anti-filter to execute the application without any problem”
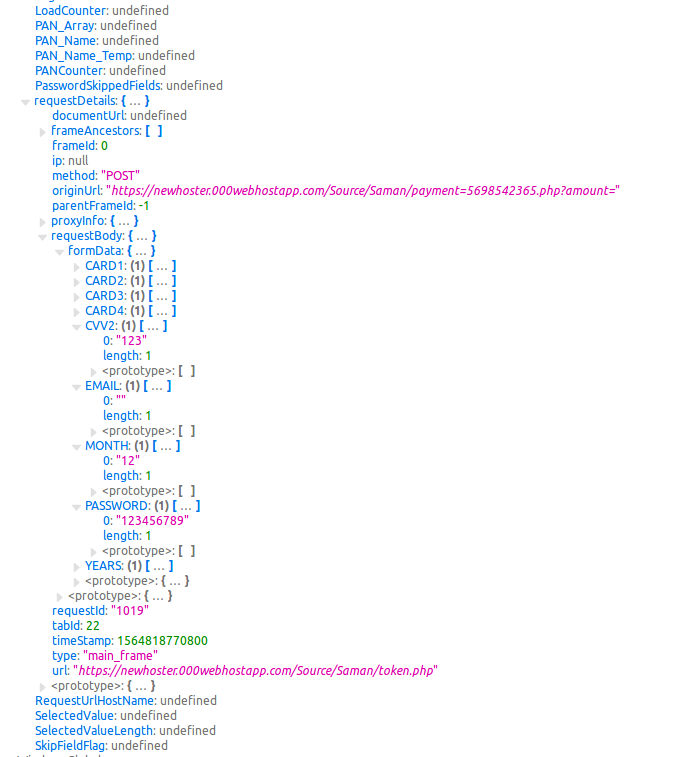
- There is a part named “use the below button to activate” that as soon as clicking on it, the user will directly refer to the fake page of the payment terminal: because some offline support servers are abroad, you need to use an anti-filter to execute the application without any problem “https://newhoster.000webhostapp.com/Source/Saman/payment=5698542365.php?amount=20000”. In this part, as soon as entering bank card information and pressing the “Pay” key, all bank card information of the user will be sent to the attacker server: “https://newhoster.000webhostapp.com/Source/Saman/token.php”. Thus, an attacker can easily steal from a user’s bank account.
Other infected examples and URLs:
You can view Other examples of this family in the following table. The MD5 hash of each one of these applications exists in the table and in front of them there are specified URLs which are fake bank payment terminals for each example. As soon as the user clicks to purchase in-application, will lead to an infected URL, and by entering bank card information, this information will be sent to the attacker server. Many of these servers are disabled but some of them such as the above example are still active.
| MD5 | URL |
| 65af54d4e7dc62e0f7ba954d48c9dea4 | http://fast-p-a-y.ga/Asan-Pardakht-12 |
| http://panel.kakopay.com/startpay/paylink/4A6560938F | 985558b2085182fe5bf9c1477953c779 |
| http://pay.warlord.it/reza-moqadam/payment=5698542365.php?amount=15000 | 9ed6fad40e6705e5d466cb2cec202e35 |
| http://dargah-sighehe.tk/eh/pay?random=8662239 | 728c7e6e5bc12f7ffa2411c32dc26012 |
| http://goo.gl/eAi4th | 581d0d936b410726e82ae1cae2e016e8 |
| http://panel.javadpay.com/startpay/paylink/8E412751CB | b5f0a7e66360bb162fd2648e4c6cd402 |
| http://shaparak.life/payment=11543459sh?amount=20000 | 4a63cf04a647d1b116582b94c1142758 |
| https://ranjbarpay.com/bmp-shaparak/payment=11543459sh?amount=20%2C000 | 26233c8989add48251454cf39399c0e5 |
| http://sep-shaparakea.ml/payx | 3b99a9c10eb8ec5b0cec385f7eea1c90 |
| http://asan.samanpay.info//payment=11543459sh?amount=10%2C000 | 89244a6d35a0c179a83896a43ede629f |
| http://panel.baranpall.com/startpay/paylink/9330CC0884 | 6a967f989b33189230850e925251b8b2 |
| http://goo.gl/KbYVJR | b99cadd8778f8bff3d4ca026dc1853f7 |
| http://fucku4.tk | 9fa5c2b39c987ced99c00e7addabdc0c |
| http://ertyyfjkhklkdthffxdhdcfhndctgnhdfhshtrdtfytj.xyz/payment.html | bbc59207bd1bb1e056f53ce010f50140 |
| http://panel.baranpall.com/startpay/paylink/47AD5E6698 | 1a15fdd7b3836c4a8fb422c778b5903e |
| http://media-tarfand-page.tk/Saman | a66cc4fe3524ddd700b5ef8e8e307afe |
| http://panel.baranpall.com/startpay/paylink/CE5C0358E2 | 8e9ede958eda088e1394bc66ec0b8e58 |
|
https://newhoster.000webhostapp.com/Source/Saman /payment=5698542365.php?amount=20000 |
78822db4d035d0e0da50fb63238fc6d3 |
|
https://newhoster.000webhostapp.com/Source/Saman /payment=5698542365.php?amount=20000 |
3bcca8307f6e8a5ad71cf7711d6450cc |
| http://online-pardakht.com/i | b06c9738ccf3b8e30f85a6ffdad49a42 |
| http://prdakht.website/y | ba2f5a9cbf3fdf9a1262f0ae309286a5 |
| http://185.183.97.102/s/pna/index.php | cbe44a0d5cf6f5c3132fedc01444a570 |
| http://aplsam.cf/meleet/?price=20,000 | bf2826e76faa311d908457904b93dbbf |
| http://1o2.ir/P4game | f9a84cf6f3b1a0a1433aba6d593c4e20 |
| http://panel.baranpall.com/startpay/paylink/75D1A3F8EC | 47af6c2b3b471b38c1cf015f714fc274 |
| http://mamad.samanpay.info//payment=11543459sh?amount=20000 | 93d6ab738d20a434d832a40de6925eb2 |
|
http://www.rsarayan.legendaryhost.ir/suorse%20ha/%40UlteraAddBot /data/catch/final/payment=11543459sh?amount=20%2C000 |
de8d95f5e75a8e3b65dcaf15cd834dc0 |
| http://asnpy.website/y | 70e2bcb897c8320b4b8e100fe5c0552a |
| http://soltahnhost.cpanelserver.ir | 30c372b3e71b29482f6007a41b0845a0 |
| http://samanshap.cf/payment.php | d50bc0b2d9a671781aacc05d8494ea85 |
| http://asay.vip/saman.ir | 6f175982641a8a1f86845c5f0a16cb63 |
| http://shahprc.tk/G/payment=5698542365.php?amount=20000 | 3d1ac8a778938fdf881278a353ea12ac |
| https://ahesmaeilzadeh.ir/bmp-shaparak/payment=11543459sh?amount=20%2C000 | 7647618215232ea1d7c16e4cd4fd96c4 |
| http://asanplpla.website/y | 4a0218018b5a1a4ab48dad61d6f6dce4 |
| http://asanpardakhet.com | b71964f27e676caddd13a34e7367e9ee |
| http://mutluyillar.xyz/lib/payment=11543459sh.php?amount=20000 | a20c0359ed41bb601a9a66a241d114f3 |
| https://bit.ly/2RuuZom | ec6011a9766a58575bf6ff7bbe054d5f |
| http://best98.ga | cf24f835f56a1d634dd8e352d50403f1 |
| https://worldsource.yoozhosting.ir/asan-shaparak/payment=11543459sh?amount=20%2C000 | b9efb4321e5eb8e40b8415d90e910edb |
| http://panel.baranpall.com/startpay/paylink/5D730A4A03 | 0d9de8ab47819f43a037086e812c55bf |
| http://shaparak.bid/payment=11543459sh?amount=10,000 | a56916d02fd79e19ec8c0d75bf25e4f5 |
| https://www.asaplmir.sevenserver.eu/cgi/new/sqq/payment | ace3f6f9541a7d880cbf46786cafd25c |
| https://whimsey.xyz/Sara-khodadaddi/payment=5698542365.php?amount=10%2C000 | db4fdf215300f4fc75c29eff5ed47431 |
| https://shargestar.com/p | 5430a08f2f8e5deb6659a33890569a79 |
| http://yon.ir/QhYer | e6669155a551d8deffd184bddd440190 |
| https://dante.speed-host.ir/asan-shaparak/payment=11543459sh?amount=50%2C000 | 8626f418dc822fb5a491e20763d19544 |
| http://irshahparak.website | c85e2689b7f061ea7c04392c86f99c1f |
How to deal with it and disinfect the system
To ensure that the system is not infected, install the Padvish Antivirus database file, keep it up to date, and scan the anti-virus.
Method of preventing phone infection:
- Avoid downloading and installing the application from unauthorized resources.
- Note the desired permission, when installing the application.
- Constantly back up the stored files and data.
- Do not use unofficial versions of any applications. Applications such as Telegram and Instagram have many unofficial versions and most of them are released through the Telegram channel.
- Pay attention tath the page you want to buy from is not a Phishing type.