General Explanation
Type: Worm
Degree of destruction: average
Prevalence: High
What is the Worm?
Computer worms such as Bitminer are types of malware that are capable of reproduction. For permanence, worms set ways to maintain the infection in each system boot. The prominent feature of worms is in their distribution which is generally performed through portable drives and shared directories in the network.
What is Bitminer malware?
Bitminer first appeared in 2014. The common aspect of all types of malware is the use of their NSIS compiler. It is a secure tool to create worms and Trojans, due to the substantive disguise script of NSIS, the existence of ready functions to manipulate in the registry, the auto-predefined variables for finding special folders in an OS with high flexibility, convenience in programming, and compressing code and playloads and the NSIS scripts.
There are different models, for classifying this family. The classification here is based on the type of miner. According to this, this family, at least, will divide into 4 generations:
- Generation 1: Trojan in the format of Graphic card installation software such as GPU_Miner
- Generation 2: Trojan dropper and miner, Trojan will only drop a file and the dropper does the rest; the independent versions with miner also exists.
- Generation 3: Worm with the ability to infect portable memories. The type of miner is NsCpuCNMiner.
- Generation 4: The worm is spreading through the local network in addition to having previous version capabilities.
Right now, the 4th generation of this malware is spread in our country which we will introduce later.
This worm by using the NsCpuCNMiner tool attempts to produce cryptocurrency and copy itself into the system drives and infect the connected computers by the local network. Bitminer by using a default list of usernames and passwords tries to connect to the users on the network by the infected system. The procedure of maintenance in the victim’s system is to create a startup folder in the $C path of the network system. In this way, the malware will create folders in this path with random names and creates the following path by folders that were created in $C:
C$\[RandomFolderName]\ Microsoft\Windows\Start Menu\Programs\Startup
Technical Explanation
Signs of infection
- Slowing system due to miner malware execution
- Being running NsCpuCNMiner32.exe or NsCpuCNMiner64.exe or tskmgr processes
- Existence of the file of the above processes in the TempoR %AppData%\ path.
- Existence a file named DOC001.exe in the same path (this file has the folder Icon despite it having exe contents)
- In the path of Windows startup (SMSTARTUP$) a shortcut is an explorer.ink will be created which will point to the execution file of the installation
- Sending the ping packet continuously.
Explaining the function of the malware:
The method of the action is that the two files: NsCpuCNMiner32.exe and NsCpuCNMiner64.exe (32bit and 64bit miners) create in the victim’s system by a file named DOC001.exe.
In the newer versions, the two files: NsCpuCNMiner32.exe and NsCpuCNMiner64.exe are removed from the malware procedure and the file DOC001.exe contains all malicious functions of the system itself.
In the older versions of malware, the list of malware pools will be embedded inside the main file contents. In today’s versions, the pools list can be viewed in a file named pools.txt in the same path. In the following image, you can view a list of mining pools.
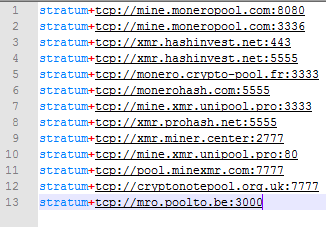
The method of releasing this malware is that for all network systems which have opened the file sharing, it will copy its execution file in all computers with the copy. To detect the name of the computer which is normally like <Computer_Name>-PC, and to be compatible with the constant variable of %COMPUTERNAME%, the <PC-> section needs to be compared. (for Russian users ПК equals to PC: Персональный Компьютер is Personal Computer)
How to deal with it and disinfect the system
Padvish Antivirus attempts to monitor such malware and disinfect them, by real-time scanning the drives and shared folders. Also, having UMP capability, which is a part of behavioral protection, prevents the system from being infected by portable drives. So, to prevent being infected by other malware that is transferred this way such as Bitminer malware, it is recommended to prevent this malware from entering your system by installing Padvish antivirus.