Overview
Type: Ransomware
Destruction Level: High
Prevalence: Moderate
Malware Name(s)
- Ransomware.Linux.Trigona (Padvish)
- HEUR:Trojan-Ransom.Linux.Agent.gen (Kaspersky)
- Trojan.Linux.Ransom.AD (Bitdefender)
- LINUX/Ransom.tzrgv (Avira)
- Ransom.Linux.TRIGONA.THEAFBC (TrendMicro)
What is ransomware?
Ransomware is a form of malware that encrypts the user’s vital data and demands ransom for decryption. Ransomware poses a grave threat, inflicting substantial financial harm. Typically, there is no feasible method to decrypt the encrypted data, and one prevalent means of paying the demanded ransom is through cryptocurrency due to its untraceable nature. With most ransomware, retrieving files becomes near-impossible, leaving the user with no choice but to transfer funds to the hacker’s account.
What is TRIGONA ransomware?
TRIGONA, a relatively new family of ransomware, emerged in 2022. Deploying the AES encryption method, Trigona encrypts files. Furthermore, it alters the filenames, appending a randomized string, and affixes the extension “(locked_)” at the end. The sample that will be described in this report is a variant tailored to target ESXi server and its purpose is to encrypt files related to virtual machines created on these servers.
Technical Review
Indicators of Compromise (IoC)
– Presence of ‘how_to_decrypt.txt’ file in all directories
– Encryption of files associated with virtual machines created on ESXi servers
– Encryption of all log files
Performance Description
The overall functionality of this malware varies based on parameters provided during execution. This ransomware is applied on vm and log files and does not make any changes on other types of files. To execute the ransomware specifying the desired path for file encryption is imperative done by assigning the path value to the ‘p/’ or ‘path/’ parameter. In the image below, you can observe the outcome of executing the file with the /” path as an example. Once executed, the ransomware file displays information about its execution progress on the server, including the number of encrypted files: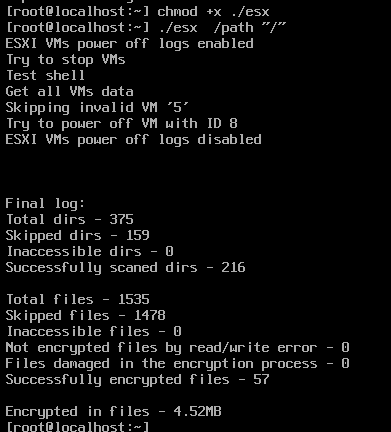
? If we consider the selected path to be the “/” path of the ESXi system, the files in the following directories will be subject to encryption:
| Infected paths |
| /vmfs/volumes/<UUID>/ |
| /scratch/log/ |
| /var/lib/vmware/osdata/log/ |
| /var/log/ |
| /var/run/log/ |
Based on the code snippet depicted in the image below, the script identifies the file types associated with ESXi server machines targeted for encryption.

In the image provided, two system commands are evident within the ransomware code. The initial command is responsible for retrieving information regarding virtual machines (VMs), while the subsequent command shuts down the available VMs. Following this, then the file encryption steps begin.


After encryption files are stored with random name and extension locked_. :

The ransomware also places its payload file, named “how_to_decrypt.txt,” in all directories along the target path.
In the provided image, the overall process of file encryption is illustrated, assuming the ransomware is executed with only its essential parameter, which is a specific path. Next, each step will be described separately:

1. The file targeted for encryption is initially opened with write access, and its contents are loaded into memory.
2. Subsequently, a range of 815 to 840 bytes from the end of the file is filled with the value “0”
3. Following this step, the initial 512 KB of the file content is replaced with encrypted values.
4. The previously inserted “0” values at the end of the file are then substituted with the specified value shown in the image above.
5. In this stage, the altered file is read.
6. Subsequently, the original file name is substituted with a new name. Verification is conducted to ensure the accuracy of the name change.
As an example, in the following images, the clean and then encrypted state of one of the log files is given:


?The ransomware file’s input parameters:
| Command line arguments | Function |
| path/ or p/ | This parameter is used to determine the desired path for encrypting files on the ESXi server. |
| full/ | The ransomware encrypts the entire content of the file. If omitted, only the first 512 KB of the file will undergo encryption. |
| erase/ | Deletes files within the specified path. |
| do_not_poweroff/ | When activated, this parameter prevents the malware from shutting down the virtual machines (VMs). Consequently, the portion of the code executing the command “vim-cmd vmsvc/power.off” will not be triggered.Encryption will start only when the VMs are operational. Once the user shuts down the VMs, the files become encrypted and the VMs become inaccessible. |
| stealth/ | This parameter initiates encryption of files while preserving their original name and extensionAlso, the Payment file is not created in the paths where the files are encrypted. These Changes can only be detected by examining the contents of the files. |
| fast/ | This parameter accelerates the file encryption process. Combining it with the “full/” parameter noticeably enhances the speed of file encryption. |
| sleep/ | The program pauses execution for a specified duration of n seconds before proceeding |
| shdwn/ | Once files are encrypted, the ESXi server shuts down. |
| delete/ | Following the completion of the file encryption operation, the ransomware deletes its own file. |
| detach/ | In this case, the malware operates in the background without displaying any logs regarding file encryption or Payment file creation in the terminal. Instead, a file named “nohup.out” is created in the directory of the ransomware file execution, documenting the names of the disregarded VMs. |
| detached/ | In this case, the malware operates in the background without displaying any logs regarding file encryption or Payment file creation in the terminal. Only the list of ignored vms is displayed in the terminal, and no separate file is created. |
| short_log/ و log/ |
These commands print the output of every function called in the ransomware code in the terminal. |
| allow_system/ | In this case, the ransomware also encrypts files with its desired extension in the extension in the system directory path of the ESXi server. |
?Ransomware Execution with the ‘full/’ Parameter:
As depicted in the image below, the volume of encrypted content in this mode significantly exceeds that of the normal mode.

? Ransomware Execution with the ‘do_not_poweroff/’ Parameter:

? Ransomware execution with the ‘short_log/’ parameter:

As illustrated in the image below, when deploying this parameter, details of every activity conducted by the ransomware are printed.

How to deal with and clean the system?
✔️ Padvish antivirus identifies Trigona ransomware and removes it from the system.
✔️ To prevent potential infection with this ransomware, it is advisable to refrain from downloading files from untrustworthy sources that could compromise the system’s security.