General Explanation
Type: RiskTool
Degree of destruction: average
Prevalence: average
What is RiskTool?
In general, this type of application is not designed for malicious purposes and is not malware. However, it may use your system resources in an undesirable or annoying way and perform some actions for malicious purposes. RiskTools are types of adware applications that are one of the most popular attacking tools for attackers.
What is the Dnotua malware family?
This type of application is released with different names such as pornographic applications, and popular applications such as Instagram, golden telegram, my Irancell, etc. which persuade a user to install them on their phone. But for using them, the user must be a member of the value-added service which has no relation to the name of the application and it will cost daily for the user or it has in-app advertising without the user’s notice or permission.

Technical Explanation
The name of this application is “the complete Hack tutorial” which is built by an application builder named “skrsoft”; this application builder has multiple detected malware many of them are contents such as free account balance and hacking techniques or other applicable apps like Instagram
Also, it uses in-app advertising to earn money, without the user’s permission and notice. Showing ads in this application perform by Adad advertising service which is the official advertising agent in most released applications. To reach the purpose of showing advertising, it must have access to the phone and SIM card information, so it can send related advertisements to earn money.
In this application and due to advertising, the application builder adds a section with this message: “there is no possibility of using this section for free. By purchasing the original version at a very low price, in addition to completely deleting advertising, you can use the full features of the program”. Users can only by paying some money delete the advertising and use these features.
In this application the in-app purchase technique has been used and also the application checks its update status from the Café Bazar application. In case there is no Café Bazar on the phone, the app will show “the Café Bazar is not installed on your phone” and if you want to continue using the app you must download and install it. Also if you have Café Bazar and this app cannot connect with café Bazar, then will suspicious an application name patcher, and declare “ you have patcher on your phone, please delete it first”, the lucky patcher is an application that gains root access and deletes all in-app advertising.
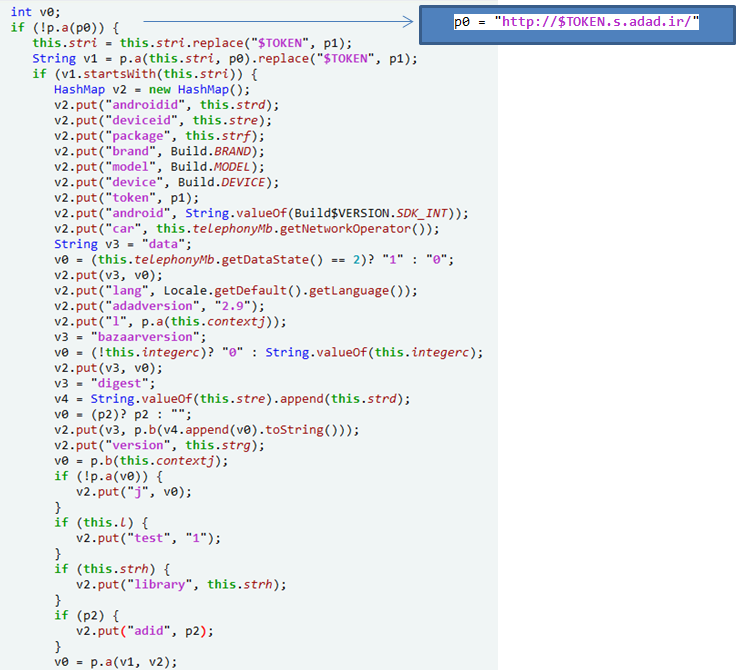
Checking whether the lucky patcher is installed on your phone or not, is to maintain in-app advertising and purchasing. This application also collects important information such as IMEI, AndroidID, deviceID, network operator, device model, device brand, data connectivity status, etc., and sends them to the advertising server http://$TOKEN.s.adad.ir.
How to deal with it and disinfect the system
To make sure that the system is safe, install Padvish antivirus and keep its database file and scan it.
Methods of preventing phone infection:
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use the unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.