Overview
Type: Trojan (backdoor)
Destruction Level: High
Prevalence: Medium
Malware Name(s)
- Backdoor.Win32.Tofsee (Padvish)
- A Variant Of Win32/Tofsee.AJ (ESET)
- Backdoor:Win32/Hostil.gen!A (Microsoft)
- HEUR:Trojan.Win32.Generic (Kaspersky)
What is Backdoor Malware?
Backdoors are applications designed to allow hackers to bypass the system security mechanism, granting unauthorized access to various system resources. Hackers can enter the system, with no concern for altered usernames or passwords, bypass authentication protocols. These applications come in various forms and hackers use them upon their needs to breach a system resource.
What is Tofsee Malware?
Tofsee is a type of malware used primarily to send spam emails via SMTP messages. The content of these emails is determined by the malware server and is commonly used for promotional spam. Another significant feature of Tofsee is its ability to download and execute executable file from the server. This malware variant is often packaged with several different crypters and ultimately injects the original malware into a svchost.exe process.
Technical Description
Indicators of Compromise:
❌ Changes the HKU\*\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\shell key, usually set to explorer.exe by default, and adds the unpacked malware path at its end.
❌ Creates a key in SOFTWARE\Microsoft\DeviceControl\DevData in `HKLM` or `HKU` with encrypted content.
❌ Presence of the following files:
%WINDIR%\Temp:temp
UserProfile%\Application Data\desktop.ini:init%
❌ If the above files cannot be created, the malware creates a file in this path:
UserProfile%\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.tmp%
Performance Description
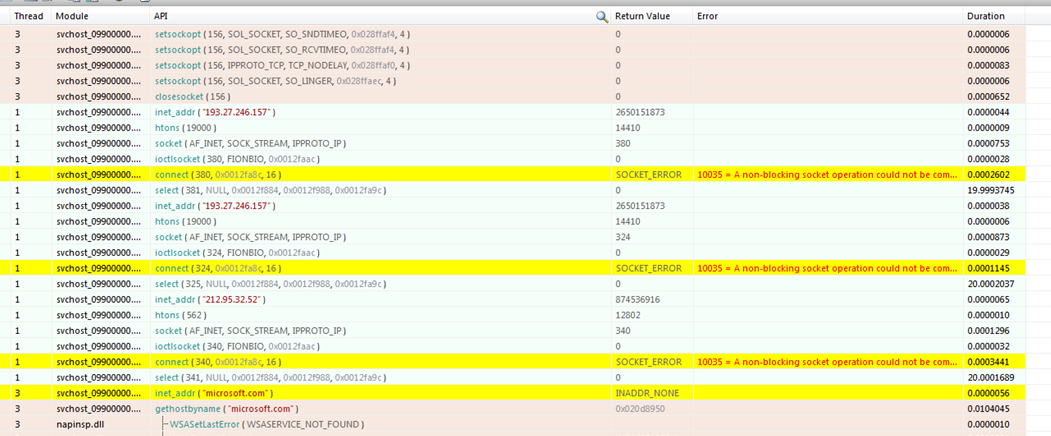
The malware consists of two main modules. The first module identifies the mail server addresses:

The purpose of another module is to communicate with the Command and Control (C&C) server to receive commands and settings, including creating a list of email addresses for spamming, email contents, and more. It can also send and execute applications on the victim’s server.
This version of the malware uses the following addresses to connect to the C&C server:
193[.]27[.]246[.]157
212[.]95[.]32[.]52
Rgtryhbgddtyh[.]biz
wertdghbyrukl[.]ch
In the image below, the main functions of the malware is provided:
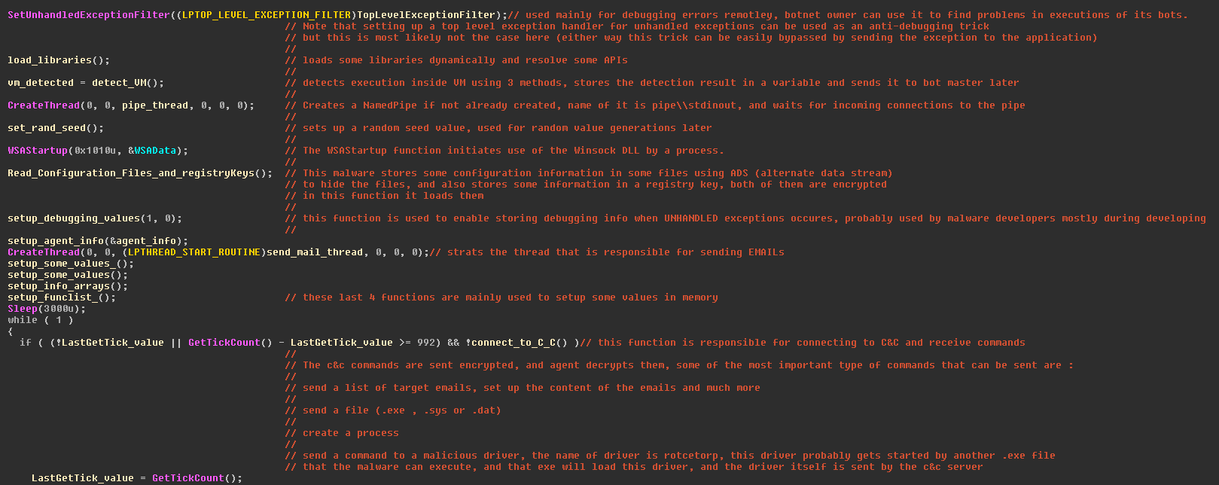
Network Connection
The malware initially attempts to find the IP addresses of mail servers such as those of Microsoft, Yahoo, etc. In another thread, it connects to its C&C server using the TCP protocol to receive and decrypt encrypted information. If the connection to the first address fails, the malware attempts to connect to other C&C addresses after 5 minutes.
How to deal with and clean the system
Padvish Antivirus detects and removes this malware. To prevent infection:
✔️ Keep your antivirus software up to date.
✔️ Obtain files from reliable sources.
✔️ Avoid clicking on suspicious links and scan email attachments with antivirus.