Overview
Type: Trojan
Destruction Level: High
Prevalence: Low
Malware names
Bot.Win32.Torzhok (Padvish)
Gen:Variant.Adware.Symmi.87092 (bitdefender)
What is Trojan?
Trojan is a type of malware that disguises itself as clean and legitimate software and behaves totally like a useful and functional software, but when executed, it causes a lot of damage to the computer system. There are different ways in which trojans could enter the system, some are: Entering through a software downloaded from the Internet, embedding in HTML text, attaching to an email, etc.
What is the Bot.Win32.Torzhok Malware?
The Bot.Win32.Torzhok malware operates with commands supported by a malicious bot. Notable actions of this malware include:
• Uploading the victim’s files to the malware’s server
• Deleting and renaming files
• Downloading and executing files on the victim’s system
• Creating a terminal on the victim’s system to execute command-line commands issued by the server
The malware server is a public service that makes the victim’s uploaded files accessible to intruders and allows its website audience to communicate with the infected systems and send them command-line commands.
Technical Review
Indicators of Compromise (IoCs)
❌ Presence of a file named .gu1d in the path %Temp%
❌ Network connections with this the address: hxxps://185[.]239[.]71[.]105
Performance Description
Upon execution, the malware creates a GUID by invoking the Windows API CoCreateGuid and saves it in a file named .gu1d in the %Temp% directory. This data is used as a cookie in the malware’s communications with a remote server.
Malware Server Address: hxxps://185[.]239[.]71[.]105
The malware then communicates with its command and control server over port 443 in the observed sample. It uses REST API functions to execute its operations.
| Function | Aim |
| api/v1/greeting/ | Introducing the victim’s system to the server by sending initial contact information. |
| api/v1/register/ | Sending the victim’s system specifications to the server, including the full operating system details, system username, computer name, etc. |
| api/v1/heartbeat/ | Receiving an identifier from the server corresponding to the victim’s host (the malware uses this identifier to receive tasks from the server). |
| api/v1/psnapshot/ | Sending a list of the victim’s system processes to the server. |
| api/v1/todo/ | Retrieving new tasks from the server |
| api/v1/task/ | Notifying about the status of the incoming task. |
| api/v1/fetch/ | Downloading files from the malware server. |
| api/v1/explorer/ | Sending a list of the contents of a specific directory to the server. |
| api/v1/mq/ | Receiving and executing command-line commands from the server on the victim’s system. A terminal is created on the victim’s system for this purpose, executing the received commands and sending the results back through the established pipe between the server and the infected system. |
| api/v1/files/ | Uploading the contents of one or more files to the malware server. |
| api/v1/goodbye/ | Terminating the connection with the server. |
Table 1- Functions used by the malware to communicate with the server
According to the descriptions mentioned in the table above, the malware requests a task from the server after introducing its system to the server and receiving the corresponding ID associated with its host. The task received from the server can include one of the following commands (payload value):
| payload | Aim |
| @download | Downloading one or more files from the malware server and creating them on the victim’s system by calling the api/v1/fetch function. |
| @upload | Uploading one or more existing files from the victim’s system as determined by the malware server. These files are sent by calling the api/v1/files/ function. |
| @cd | Extracting a list of contents in a specified directory by calling the api/v1/explorer/ function. |
| @psnapshot | Extracting the list of system processes by calling the api/v1/psnapshot/ function. |
| @fetch | Downloading the file |
| @execute | Executing commands received from the server on the victim’s system. |
| @rm | Deleting the file or files specified by the malware server from the victim’s system. |
| @rename | Renaming one or more of the victim’s system files to the new names specified by the malware server. |
Table 2- List of Malware Tasks Received from the Server
While executing the received tasks and establishing the necessary communications, the malware reports the result of its task by calling the “api/v1/task/” function, then requests a new task again.
For example, in the received sample task presented below, in the payload content, the server has sent the @cd “C:\\” command to the malware to execute. The {Qzpc} expression in the following image is the encoded equivalent of the “C:\\” directory:
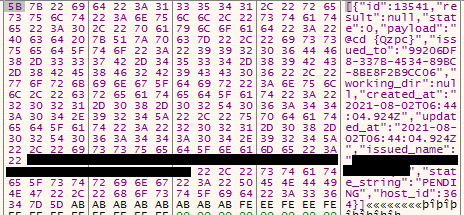
Figure 1 – A Sample Task Received from the Server
In the figure above:
- Payload: A command that the malware must execute on the victim’s system.
- ID: The corresponding identifier for this task.
- Issued_to: The value corresponding to the GUID created for the user.
- Host_ID: The ID received from the malware by executing the `api/v1/heartbeat/` function.
- Issued_name: Corresponds to `username@computer_name`.
How to Deal with and Clean the System
Padvish Antivirus detects and removes this malware from the system. It is recommended to keep your operating system and antivirus up to date.
To enhance security against the significant increase in cyberattacks, including advanced persistent threats, follow security recommendations and use Padvish Managed Detection and Response (MDR) services.