Overview
Type: WebShell
Destruction Level: High
Prevalence: Moderate
Malware names
- Backdoor.PHP.WebShell.Indosec (Padvish)
- PHP / Webshell.NHE (ESET-NOD32)
- HEUR:Backdoor.PHP.WebShell.gen (Kaspersky)
What is WebShell?
WebShell is a malicious script written in scripting languages such as ASP, Python, PHP, or JSP. When injected onto the victim’s web server, these webshells grant the attacker complete control over the website. These attacks typically exploit security vulnerabilities in vulnerable web servers.
Attackers easily discover and target servers accessible on the Internet. By injecting the web shell into the web server, organizations face serious and sometimes irreparable risks. Therefore, organizations must prioritize these warnings and implement robust security measures.
What is Backdoor.PHP.WebShell.Indosec?
This report discusses a sample from the Indosec family of web shells. Using this webshell, intruders can execute a range of malicious actions on the victim’s server.
The capabilities of this malware:
- Uploading files to specific paths
- Encrypting files and demanding ransom
- Defacing the victim’s website
- Creating files and folders, and modifying them
Technical Review
Performance Description
To access the Webshell admin panel, the attacker creates a login page with the username admin, as depicted in the image below the login page.

Figure 1- login Page
Upon successful login, the following page is displayed. As illustrated, the IndoSec Shell equips attackers with various capabilities.

Figure 2 – A view of home tab
- Within the terminal section, as shown in the subsequent figures, this webshell can execute Windows and Linux commands based on the victim’s server’s operating system.
In the following two figures, you can observe a command executed under the Windows terminal while the web shell operates in the Windows environment, and a command executed under the Linux terminal while the web shell operates in the Linux environment:
▫️Result of executing ipconfig in a Windows environment:

Figure 3 – Executing a Windows command in the terminal
▫️Result of executing uname -a command in a Linux environment:

Figure 4: Executing a Linux command in the terminal
- The informasi section displays details about the current system.

Figure 5 – System Information
- In the subsequent section, the outcomes of each action are displayed. For instance, in the initial login mode, details such as files in the current directory, access types, and actions on the files are displayed, or after running commands in the terminal, the outputs are shown in this field.

Figure 6 – Displaying the current directory
The various capabilities of the malware are outlined in the table below:
| Feature Name | Feature Description |
| upload | Enables file uploads to desired paths. |
| Bautfile | Enables creating new files and adding content to it. |
| Bautfolder | Enables creating new folders in desired paths. |
| Mass deface | Enables the attacker to batch changes index files, resulting in defaced websites on the victim’s server. This section enables simultaneous content changes to multiple files, so that the target path and file name determined by the attacker. As a result, the content of all files with the specified name (by default index.php ) located in the corresponding path will be changed. |
| Mass delete | Deletes multiple files simultaneously. |
| jumping | Checks for the existence of host management control panels in the system and displays files in associated paths. |
| config |
Put path configuration files of various content management systems (CMS) into a file named ‘$user_con-$nama_config.txt,’ providing critical information to the attacker including database name and password. Reviewed CMS platforms: Hostbills, Zencart, BoxBilling, WHMCS, Joomla, WordPress, IPB, OsCommerce, MyBB, Vbulletin, Ellislab, OpenCart, Magento, PrestaShop, Drupal, phpBB, Lokomedia, cPanel. |
| adminer | Opens the database management page if an ‘adminer’ file is present, allowing viewing and modification of databases using the username and password. |
| symlink | In this part of the code, the contents of the file named.conf or named.txt name are displayed as a table consisting of Domains, Users, and symlink columns, and three different links are created, each of which is for a specific application that will be mentioned in Further Details. |
| Auto reset cPanel | Resets the password for cPanel in the case that it is used in managing the targeted website. |
| ransomware | This module encrypts files in desired directories, appending ‘.indsc’ extension to file names and adding a payment-related ‘index.php’ file next to the files. Encryption currently inactive due to the unavailability of the encryption address: http://encrypt.indsc.me/api.php?type=encrypt. |
| smtpgrabber | Displays SMTP information such as SMTP Host, Port, User, Pass, Auth, Secure. |
| Bypass cloud flare | If the website is equipped with cdn cloudflare, different parts of this could be bypassed and the actual IP of each of the webmail, ftp, cpanel and other servers can be obtained. |
| keluar | Exit the program and returns to the login page. |
Further Details
? Mass deface
Upon selection of this option, the replacement content intended for the original file will be written in the respective directory files. Subsequently, the contents of all files with the specified name in the NamaFile section within the directory will be altered.

Figure 7 – Contents of Mass Deface page

Figure 8 – List of files changed by Mass deface

Figure 9 – The defaced page
? Jumping
In the Jumping section, the presence of host management control panels in the system is checked, and the associated path files are displayed. This section operates as follows:
• If an H-sphere control panel exists on the system, a jump link will be established for the following path based on system user numbers and existing URLs:
hsphere/local/home/$user/$url
• If H-sphere is not present on the system, it will navigate to the vhosts directory and create a jump link for different URLs for the following path:
/var/www/vhosts/$url/httpdocs
• Lastly, a jump link is created for each user for home/$user_pro_jump/public_html/. The executed sample displayed below, highlighted in green, has read-only access type.

Figure 10 – Jump Output
? Adminer
Adminer is a database management tool. The malware checks for its presence on the system and, if present, it displays the database login page. In this section, the attacker gains easy access to the database if login credentials are obtained:

Figure 11 – Displaying the Adminer Page
? Symlink
Symlinks are files that act as pointers to other files, containing no content of their own but pointing to the original files. Deleting the original file renders the symlink unusable.

Figure 12: Malware Symlink Module
According to the above figure the Symlink module of this malware includes:
1️⃣ Bypass Read: Selecting this option displays named.conf file contents with read access in the output. Pressing save key, saves this content in named.txt in the path to execute the original file.
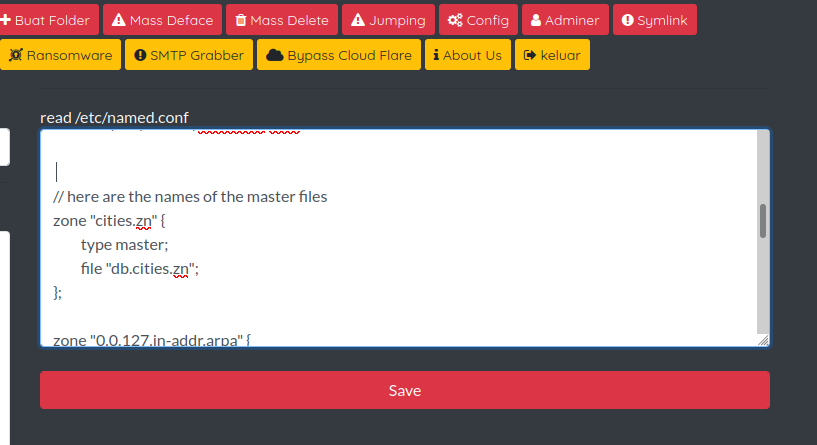
Figure 13: Bypass Read in the Symlink module
2️⃣ Symlink404: A symlink file can be created from the target file in the indosec_sym404 directory with the desired name. To Test the path one of the WordPress files entered as the Target file and txt.12 as the symlink file name and is displayed upon clicking on the link >>Sukses<<.

Figure 14- Symlink404 Section

Figure 15 – Ability to display the contents of the Target file
3️⃣ Symlink Bypass: This displays etc/passwd file contents, containing system account information. Choosing Symlink saves its content as passwd.txt in the current path.
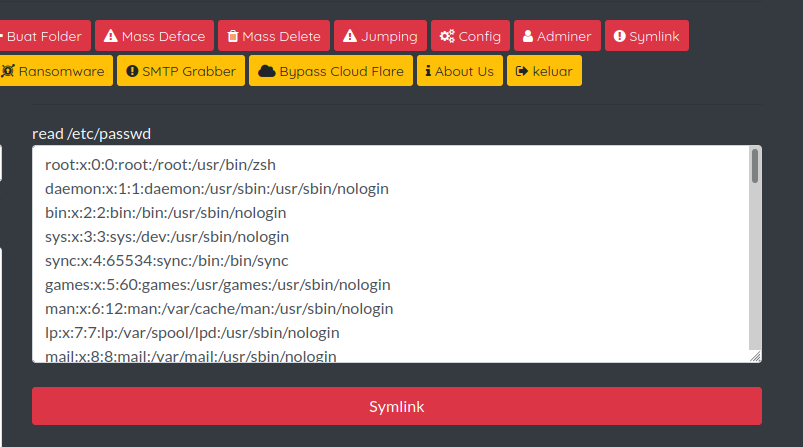
Figure 16 – Symlink Bypass
? Ransomware:
This refers to the ability to execute ransomware. for this section, as depicted in the red box 1 below, the target file is read from the chosen path, encoded with the base64 algorithm, and sent to the attacker’s server. The returned packet includes an encrypted file, decoded and placed in $_ENC variable.
Following this step, the INDSC. extension is added to the file name, and a SUCCESS message appears in the output. However, actual encryption and extension changes were not performed during malware analysis due to server unavailability.
In box 2, the operation related to displaying the PAYMENT page is preformed, and an INDEX.HTML file is created as PAYMENT, with the content displayed below.


Figure 17: The HTML content of the payment page

Figure 18 – The payment page
How to deal with and clean the system?
Padvish Antivirus detects this malware. To avoid infection by such malware, it is recommended to:
✅ Fully and securely configure your web server.
✅ Block unused ports and services.
✅ Use complex passwords and change them regularly.
✅ Consistently apply security updates.
✅ Considering the escalating cyber threats, for network and system security against advanced persistent threats and cyber-attacks, alongside adhering to security recommendations, use Padvish Managed Detection and Response (Padvish MDR).