Overview
Type: Trojan
Destruction Level: High
Prevalence: Moderate
Malware Name(s)
- Trojan.Win32.NJrat (Padvish)
- A Variant Of MSIL/Bladabindi.AS (ESET-NOD32)
- Backdoor.MSIL.Bladabindi.AJ (Kaspersky)
What is trojan?
Trojan is a type of malware that disguises itself as clean and legitimate software and behaves totally like a useful and functional software, but when executed, it causes a lot of damage to the computer system.
There are different ways in which trojans could enter the system, some are: Entering through a software downloaded from the Internet, embedding in HTML text, attaching to an email, etc.
What is NJRat Malware?
NJRat, also known as a Remote Access Trojan (RAT), is a malware designed to infiltrate systems to steal sensitive information and spy on victims. Its capabilities are accessing the victim’s webcam, microphone, system files, and capturing keystrokes (keylogging).
Technical Review
Indicators of Compromise (IoC)
NJRat malware manifests in various versions, each with distinctive indicators of compromise (IoCs). Common signs (IoCs) include:
✅Creation of specific registry keys upon execution, such as:
HKU\[SID]\Environment\SEE_MASK_NOZONECHECKS: “1”
..”HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\[RandomNumber]: “”PathToExe
HKLM\SYSTEM\CurrentControlSet\services\SharedAccess\Parameters\FirewallPolicy\FirewallRules\[RandomValueName]\”v2.10|Action=Allow|Active=TRUE|Dir=In|Protocol=6|Profile=Public|App=PathToExe
“|Name=ExeName.exe|
“@” :HKU\[SID]\Software\ExeName\US
?In these instances, PathToExe denotes the new location where the malware replicates itself (e.g., %tmp%), while “ExeName” represents an arbitrary name chosen by the attacker during file Building.
Performance Description
NJRat’s primary objectives encompass stealing information, and spying on the system. The malware capabilities are:
– Accessing the victim’s webcam and microphone
– Real-time monitoring of victim’s desktop
– Logging keystrokes
– Stealing system files
– Uploading files to the system
– Executing files, commands, etc.
Furthermore, NJRat’s capabilities, such as file placement and obfuscation, are adjustable during its construction, depending upon the utilized version.
Following execution, the malware duplicates itself in the specified path, generating a random name, and ensures persistence within the victim’s system by creating a registry key at \HKU\[SID]\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
appdata%\Microsoft\Windows\Start Menu\Programs\Startup%
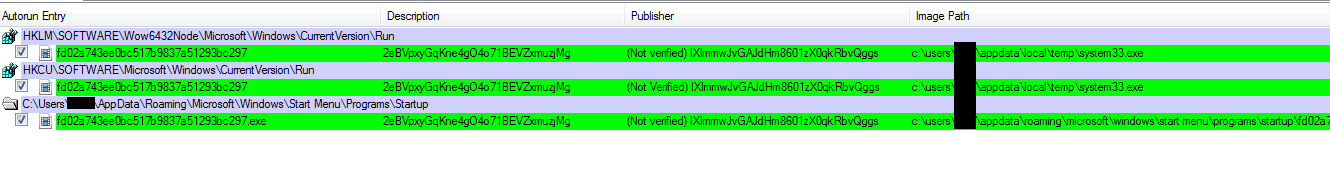
Network Operation
The process of this malware involves establishing a TCP connection with a arbitrary destination port. It’s worth mentioning that certain packets sent by the malware are encoded using the Base64 algorithm. Furthermore, within the stream of data sent from the compromised system, a pipe symbol “|” is consistently present, as illustrated in the figure below.
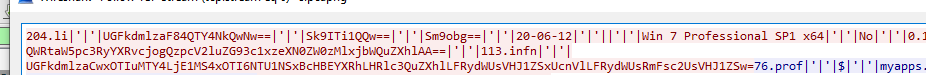
The information shown in the above image represents the initial packets transmitted from the victim’s system to the attacker, maintaining a consistent format across various iterations of the NJrat malware. Each data packet contains various system information, including usernames and OS versions, with some data encrypted by the malware.
How to deal with and clean the system
Padvish antivirus software effectively detects and removes NJRat from infected systems. To reduce the risk of NJRat infiltration:
✅ Avoid clicking on suspicious links and run antivirus scans on email attachments.
✅ Be cautious when executing files of uncertain or unknown sources.