Overview
Type: Trojan
Destruction Level: High
Prevalence: Moderate
Malware Name(s)
- Backdoor.Win32.JackalControl.ap (Padvish)
- HEUR:Trojan.MSIL.Agent.gen (Kaspersky)
- A Variant Of MSIL/Small.DF (Eset)
What is Backdoor Malware?
Backdoors are applications designed to allow hackers to bypass the system security mechanism, granting unauthorized access to various system resources. Hackers can enter the system, with no concern for altered usernames or passwords, bypass authentication protocols. These applications come in various forms and hackers use them upon their needs to breach a system resource.
What is JackalControl Malware?
Golden Jackal is the name of a hacker group renowned for creating multiple malwares in the .NET language, leveraging them to target select organizations across the Middle East and South Asia.. The scope of their target is inferred based on the content inside an infected Microsoft Office Word file (as one of the methods of spreading this malware family). This group has developed five malware named JackalControl, JackalSteal, JackalScreenWatcher, JackalPerInfo and JackalWorm. The following report describes the performance of the JackalControl malware from this family.
Technical Review
Indicators of Compromise (IoC)
Upon receiving arguments, the system may exhibit one of the following signs:
1. Creation of an in-system task to execute a copy of the malware in either the %ALLUSERSPROFILE% or %Temp% paths.
2. Establishment of a registry key in the path HKEY_Current_User\Software\Microsoft\Windows\CurrentVersion\Run.
3. Generation of a service using the sc.exe tool within the Windows OS.
Performance Description
Depending on the arguments provided from the command line, the malware executes one of the following operations on the system:
/h0: Creates a task to execute the malware’s survival file.
/h1: Creates a value to the RUN registry key to execute the malware’s survival file.
/h2: Creates a service to execute the malware.
/r0: Executes as a standard process via a scheduled task.
/r1: Executes as a standard process via the RUN registry key.
/r2: Executes as a service.
The malware then extracts the following three values from the system to create an ID:
- UUID
- Machine GUID
- Serial Number for PHYSICALDRIVE0
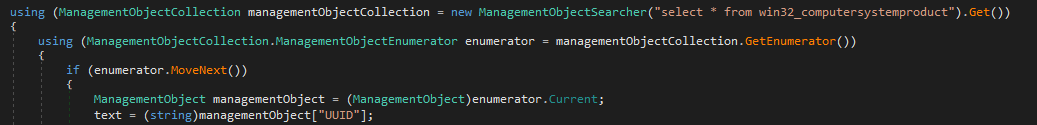
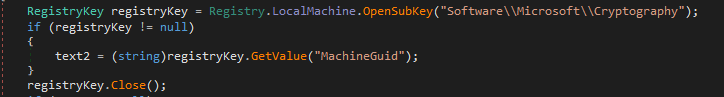
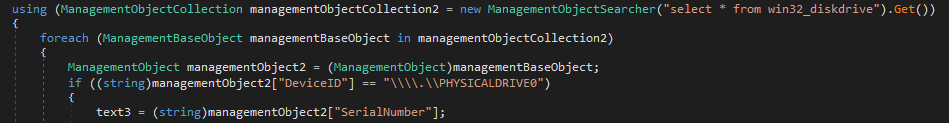
An identifier is generated using the parameters provided and through the algorithm depicted in the image below. This identifier will then be utilized in the encryption algorithm.
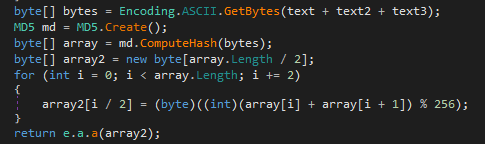
The encryption algorithm used for one of the data encryption steps before sending it to the malware server is DES in CBC mode.
If the malware is executed without input arguments in the system, the ID creation procedure is reiterated. After sending the data to the server, the malware’s survival process in the system proceeds as follows:
1️⃣ The malware extracts the folders within the %ALLUSERSPROFILE% path on the current system and selects a random folder from the list to place a copy of itself inside. The naming pattern for the malware survival file follows this pattern:
Launcher.exe + a randomly chosen folder name from the path + %ALLUSERSPROFILE%
For instance: MicrosoftLauncher.exe
In previous versions of the malware, the fixed character string Update.exe was used instead of Launcher.exe in the mentioned naming pattern.
2️⃣ If the copying process described above fails, the malware proceeds to search the following folders and attempts to copy itself into one of them:
- Viber
- AdGuard
- WinZip
- WinRAR
- Adobe
- CyberLink
- Intel
3️⃣ If the above-mentioned procedure also fails, the malware will be copied into one of the following paths:
- %ALLUSERSPROFILE%
- %LOCALAPPDATA%
- %Temp%
4️⃣ After the copying process is completed, a task will be periodically created to execute the malware survival file. This task file will be generated alongside the malware survival file. Once the task is successfully created, the initial file will be deleted.

How the malware communicates with it’s C&C?
Before establishing the initial connection to its command and control (C&C) server, the malware gathers the victim’s system ID along with the following information:
- Computer name
- OS version
- Domain
- User
- Local time
- Interfaces(DESC, TYPE, MAC, IP, GW, DNS, DHCP, DOMAIN)
- Remote IP
- Current directory
- Drives
- Applications
- Processes
All information is then encrypted and sent to the malware server in the following format:
base64 + base64 + DES + GZip
The final example of the package sent to the malware server is as follows:

Communication with the server is conducted via HTTPS. The following are two examples of communication addresses utilized by this version of the malware:
hxxps://nassiraq.iq/wp-includes/class-wp-header-styles.php ?
hxxps://sokerpower.com/wp-includes/class-wp-header-styles.php ?
Upon establishing communication with the attacker’s server, the malware gains the capability to execute programs, download files onto the victim’s system, and upload files from it.
| Command Codes | Function |
| 00 | Execute the attacker’s desired program on the victim’s system. |
| 01 | Download file |
| 02 | Upload file |
In this report, one version of the Golden Jackal malware family is discussed. However, as previously mentioned, the Golden Jackal hacker group possesses various types of malware with distinct objectives. Consequently, attackers can deploy a combination of these malware variants to achieve their goals effectively.
How to deal with and clean the system?
Padvish antivirus detects and blocks the network communications used by Golden Jackal malware. Additionally, it detects various versions of this malware and effectively removes them from the system.
✅ To prevent the risk of potential infection by this malware, refrain from opening emails from unknown sources and ensure regular updates of your OS.
It is recommended to download software exclusively from reliable websites and trusted sources.