Overview
Type: Worm
Destruction Level: Moderate
Prevalence: High
Malware Name(s)
- Worm.Win32.Renamer (Padvish)
- Virus:Win32/Grenam.B (Microsoft )
- Win32/AutoRun.Delf.LV (ESET-NOD32)
What is a worm?
A worm is a type of malware characterized by its ability to self-replicate and spread within computer systems. Worms, like the Renamer malware, establish mechanisms for persistence, ensuring they remain active during each system boot. These malicious programs often spread through portable drives and shared directories within a network.
What is the Renamer malware?
The Renamer malware, in particular, operates by generating its own files with deceptive names, closely resembling those of legitimate system files. After some alterations, the malware disguises itself among clean files, allowing it to execute alongside genuine components without raising immediate suspicion.
Technical Review
Indicators of Compromise (IoC)
- Adding a prefix (randomly) to the beginning of clean file names (in new versions letter (v) and in old versions letter (g)) and hiding them from the user
- Existance of the paint.exe file, in the path Users%\AppData\Roaming\Paint.exe% (in the old version of Ground.exe)
- Existence of the file systemroot%\paint%
- Existence of Paint.lnk file to guarantee survival:
%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\Paint.lnk
Target: %AppData%\Paint.exe
Malware Intent
One of the goals of this malware is to occupy hard disk space and overuse CPU.
Performance Description
✔️ Malware adds a random prefix (letter “v” in this version of the file ) to the beginning of the names of clean and system files in the following paths. Then it hides them and creates its own files with fake names, similar to the names of those files. In that way, the malware copies itself into folders.
%systemroot%:\*.exe
%systemroot%:\ProgramFiles\…\*.exe
:%Users%\Desktop\*.exe
✔️ The system user runs the malware assuming the file is clean, but without realizing that first the malware and then the clean file is running. An example of how the malware works, can be seen in the following image:
Malware file: C:\Program Files\Google\Chrome\Application\chrome.exe
Clean file : C:\Program Files\Google\Chrome\Application\vchrome.exe

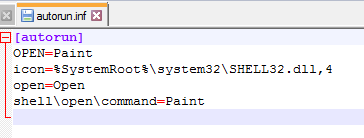
✔️ The malware places an autorun file with the following contents on all system drives (%systemroot%: autorun.inf) :
 ✔️ Then, for Survival, the Malware creates a shortcut that points to the original malware file:
✔️ Then, for Survival, the Malware creates a shortcut that points to the original malware file:
%Users%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Paint.lnk
Target: %Users%\AppData\Roaming\Paint.exe”

How to deal with and clean the system?
✔️ By employing UMP technology as a part of its behavior-based protection, Padvish antivirus prevents the system from becoming infected through portable drives.
So, it is recommended to install Padvish antivirus to prevent malware infections (such as Renamer) that are transferred through portable drives.