Overview
Type: Trojan
Potential Damage: Medium
Prevalence: Medium
Malware name(s)
- Trojan.Android.Fakecalls.Banker
What is a Trojan?
Trojan is a type of malware that disguises itself as a trusted and legitimate software and behaves totally like a useful and functional software. But once it is executed, it causes a lot of damages to the computer system.
There are different ways in which trojans could enter the system, some are: Entering through a software downloaded from the Internet, embedding in HTML text, attaching to an email, etc. Unlike viruses and worms, trojans cannot replicate themselves.
What is Fake call malware family?
“fake call” is a malware family of Trojans. This banking Trojan acts as a banking software. The infecting method of this type of malware is voice phishing (vishing). The process of voice phishing in this malware family is that, the hacker calls the target victims with the fake title of “banker” and tries to deceive them. The potential victim is deceived by false and attractive offers of loans with low interest rates. The fake conversation takes place while the phone number belonging to the malware operators is replaced with a real bank number. Therefore, the victim thinks that he had the conversation with a real banker. Once trust is established, the victims are tricked to confirm their credit card information.
Technical Review
Indicators of Compromise (IoC)
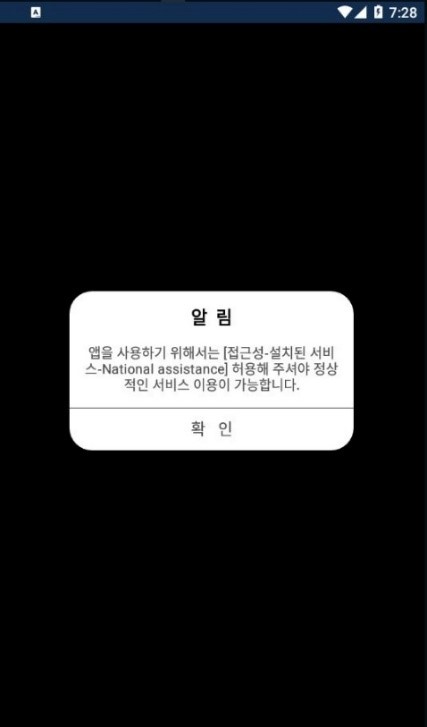
Dangerous permissions request
Request permission to use Accessibility feature
Once the app is installed, despite its successful installation, the app icon is not visible.
The application page is like this:
First, the user is asked to enable the “run in background” option for the application.
Then the user is asked (in Korean) to enable accessibility service in application setting, like this:
(The English equivalent: “In order to use the app, you must allow to use the normal service”)
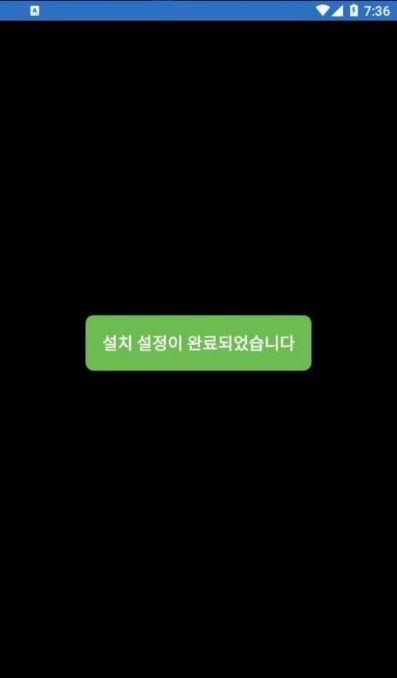
After activating the application, the following page will be displayed.
“Installation setup is complete” is written on the green button.
After enabling the accessibility feature of runtime permissions, the user is requested to set the malware as the default calling app.
Performance Description
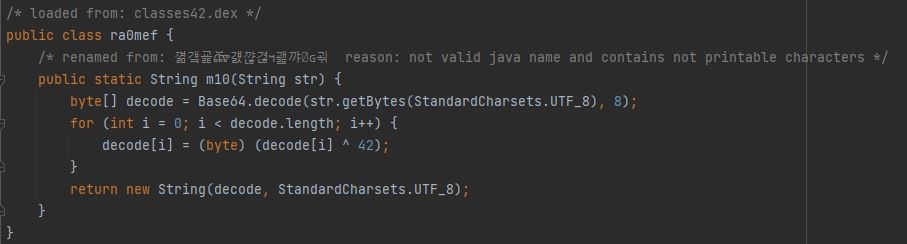
A cursory look at the application code reveals that the important application items,
including the names of some methods and strings, have been encoded.
The m10 method in the sairwpw3.k7ngwog.ra0mef class acts as a decoder, with this method, encoded items are decoded.
By dynamic analysis of this method and observing its inputs and outputs, we reach the following address:
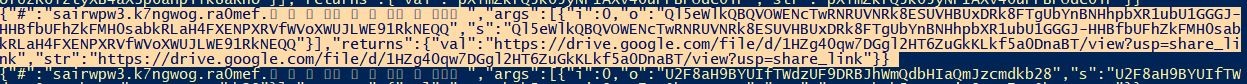
At the above address, there is a file which it’s name consists of a long string.
The application generates malware by reading the name of this file and concentrates it with another string and finally with C&C addresses.
SERVER39_sn2c4hg6fprb8.com
SERVER40_sn3isv3hf36ef.com
SERVER41_sn4yitf01o3pk.com
SERVER42_sn5us1iw4h9rv.com
SERVER43_sn1lwm3e04gwf.com
SERVER44_sn6xs1hfa6x2o.com
This malware gets sensitive accesses like list of installed apps, mobile phone operator, serial number, sim card number, contacts, text messages, location, camera, call recordings and call history.
In addition, by setting itself as the default calling app, it has the ability to answer the call or reject it, delete contacts, text messages and call history. This application makes use of the very sensitive accessibility service to do some of these things.
In this service, the functionality of dialer application is checked in real time.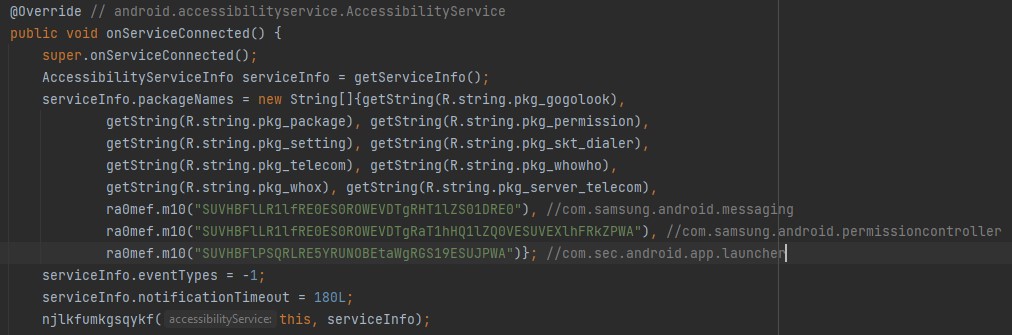
Malware techniques
If the application apk file is converted to a zip file, and then unzipped, the application will encounter the next volume required error.
This means that the malware is manipulated in a way that it is recognized by compression softwares as a multi-part zip file.
Of course, by binary file checks, and making changes in the software signature, the problem of decompressing the software file is solved.
How to deal with and clean the system?
To ensure that the device is not infected, install Padvish antivirus, keep its database file up-to-date and run an antivirus scan.
How to protect your mobile device from infection?
- Make sure you download/purchase your applications from trusted sources/app stores and do not download
them from unknown sources. - When installing mobile applications, pay attention to app permissions.
If an application asks for irrelevant access permissions, especially the accessibility service permission, be careful in using it.