Overview
Type: Trojan
Destruction Level: Medium
Prevalence: Medium
Malware name(s)
- Trojan.Win32. RisePro.a (Padvish)
- A Variant Of Win32/TrojanDownloader.Agent.GNV (ESET)
- HEUR:Trojan-PSW.Win32.RisePro (Kaspersky)
What is a Trojan?
Trojans are a type of malware that masqurades themselves as legitimate and lawful software, behaving very similarly to useful and practical applications.
However, when executed, they create numerous disruptions for the system. In Some ways trojans enter a system including downloading software from the internet, embedding in HTML text, attaching to emails, and more.
Unlike computer viruses and worms, trojans cannot replicate themselves.
What is RisePro malware?
The RisePro malware is a Trojan that collects system specs, browser logs, crypto wallet passwords, and screenshots of the victim and sends them to its command and control (C&C) server.
According to the image published on the Telegram channel of this malware, this information is sold in full details. In addition, RisePro malware can receive malicious executable files from its C&C server, including ransomwares and other malwares, to run on the victim’s system.
Technical Review
Indicators of Compromise (IoC)
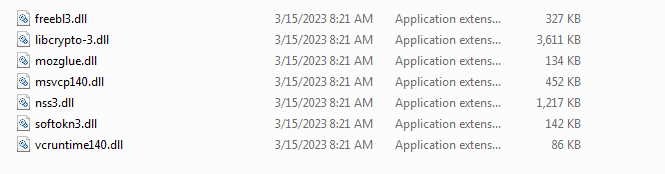
Non-infected libraries used by the malware, located in a randomly named folder in the %Temp%path.
Files like, Information.txt, passwords.txt, and other gathered information stored in a pseudorandomly-named folder in the %Temp%path (One of the two names has to be at least one character different from the othe).
Internet connections in specified paths in the sent/received commands table to C&C servers.”
Performance Description
RisePro malware utilizes several un-infected libraries for its operations. To do so, it creates them in a folder within the %Temp%path upon execution.”
Remote Server Connection
After collecting initial victim information, such as IP address and system specs, RisePro malware establishes communication with its C&C server.
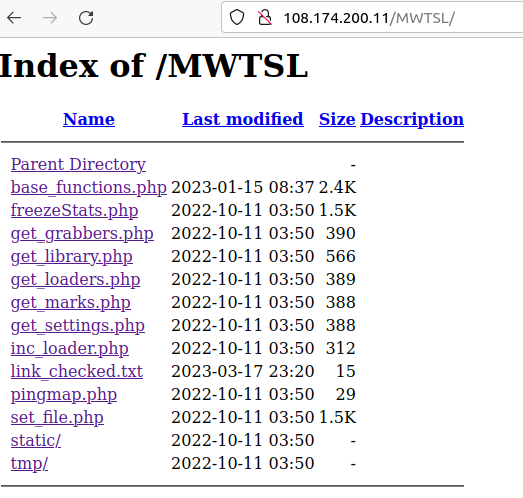
Some command and control servers of this malware have the following structure:
Risepro malware commands include the followings:
/get_marks.php:
List of the available services of the malware
for presentation to its clients.
Examples of responses received from the server:
{“success”:true,”result”:
{“marks”:[{ “_id”:”xxxx”, “user”:”xxxx”, “name”:”BankiCA”, “domains”:”bmo.com,cwbank.com,royalbank.com,vancity.com,servus.ca,coastcapitalsavings.com,alterna.ca,interiorsavings.com,synergycu.ca,mainstreetcu.ca”, “color”:”orange”, “checkCookie”:true, “checkPasswords”:true, “checkHistory”:false, “createdAt”:”2023-01-26T08:49:30.239Z”,”__v”:0},
{“_id”:”xxxx”,
“user”:”xxxx”, “name”:”SetiXyeti”, “domains”:”/vpn/index.html,portal/webclient,remote/login,/vpn/tmindex.html,/LogonPoint/tmindex.html,XenApp1/auth/login.aspx,auth/silentDetection.aspx,/citrix/,/RDWeb/,/+CSCOE+/,/global-protect/,sslvpn.,/dana-na/,/my.policy”, “color”:”purple”, “checkCookie”:true, “checkPasswords”:true, “checkHistory”:true, “createdAt”:”2023-01-26T08:48:59.868Z”,”__v”:0},{“_id”:”xxxx”, “user”:”xxxx”, “name”:”kajabi.com”, “domains”:”kajabi.com,newkajabi.com”, “color”:”red”, “checkCookie”:false, “checkPasswords”:true, “checkHistory”:false, “createdAt”:”2022-12-04T17:23:31.450Z”,”__v”:0},
{“_id”:”xxxx”,
“user”:”xxxx”, “name”:”steampowered.com”, “domains”:”steampowered.com”, “color”:”blue”, “checkCookie”:false, “checkPasswords”:true, “checkHistory”:false, “createdAt”:”2022-12-04T14:57:23.380Z”,”__v”:0},
{“_id”:”xxxx”,
“user”:”xxxx”, “name”:”humblebundle”, “domains”:”humblebundle.com”, “color”:”green”, “checkCookie”:true, “checkPasswords”:true, “checkHistory”:false, “createdAt”:”2022-11-23T15:58:09.126Z”,”__v”:0}]}}
◊ /get_settings.php:
Get settings from the server
In this command the list of information that needs to be collected from the victim system is specified.
Examples of responses received from the server:
{“success”:true,”result”:
{“settings”:{ “_id”:”xxxx”, “HWIDduplicatesDay”:true, “HWIDduplicates”:false, “IPduplicates”:false, “telegram”:true, “discord”:true, “screenshot”:true, “cryptoWallets”:true, “netHistory”:true,
“staticMarks”:””, “telegramIds”:[], “createdAt”:”2022-06-20T23:57:13.984Z”,”__v”:0}}}
◊ /get_loader.php:
According to the malware’s code, this function is related to receiving the executable file and executing it with the ShellExecute function.
◊ /get_library.php:
Get the non-infected libraries needed to run the malware’s features, if they are not statically present in the file.
◊ /set_file.php:
Send the file from the victim’s system to the server.
Information Gathering
Once the type of information to be collected from the victim’s system is determined ( response to the ‘/get_settings’ query), RisePro gathers the information. The observed samples contain the following items:
1. Hardware and software specs of the victim’s system.
2. Victim system specs, including the operating system, language, system time, hardware specs, list of processes, and a list of system softwares.
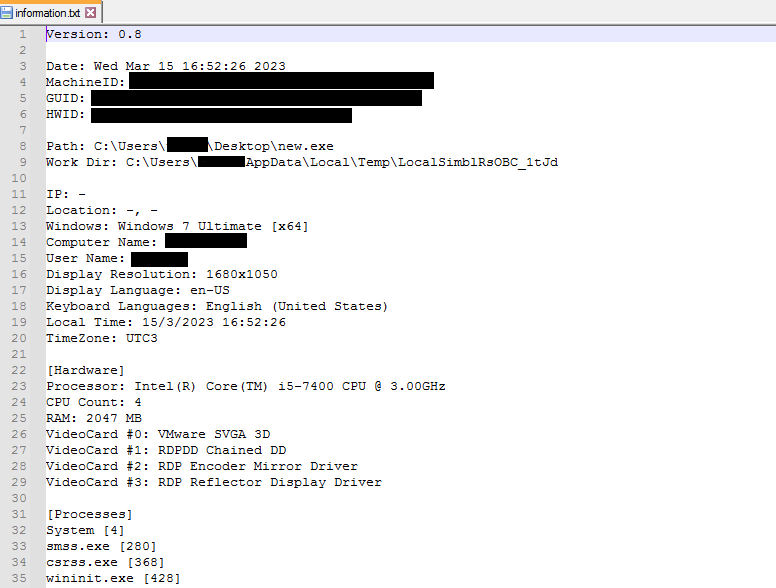
After collection, this information is stored in a text file named Information.txt.
The malware obtains the victim’s IP address using the following addresses:”
https://ipinfo.io
https://db-ip.com
https://www.maxmind.com/en/locate-my-ip-address
The following image presents an example of information gathered by this malware:
Victim’s Screenshot
Browsers’ information, password stored in crypto wallets, and some other softwares: In the observed examples, the targeted softwares of the malware included the following items:
Browsers:
Brave-Browser, CryptoTab Browser, Yandex, Atom, BlackHaw, Pale Moon, IceDragon,7Star, ChromePlus, Chromium, ChromiumViewer, Amigo, Chedot, Iridium, CentBrowser,Vivaldi, Elements Browser, Epic Privacy Browser, Citrio, Coowon, QIP Surf, Dragon, Orbitum,Torch, Comodo, 360Browser, Maxthon3, K-Melon, K-Meleon, Sputnik, Nichrome,CocCoc browser, NetboxBrowser, Firefox, Waterfox, Cyberfox, liebao, Kometa
Crypto wallets:
Terra, SaturnWallet, EQUALWallet, NiftyWallet, BitAppWallet, PaliWallet, NiftyWallet
LiqualityWallet, Iwallet, MewCx, ForboleX, Metamask , Coinbase, RoninWallet, CloverWallet
CloverWallet
Other Softwares:
Battle.net, NVIDIA GeForce Experience,
Thunderbird, uCozMedia, Authenticator, Wombat, KardiaChain
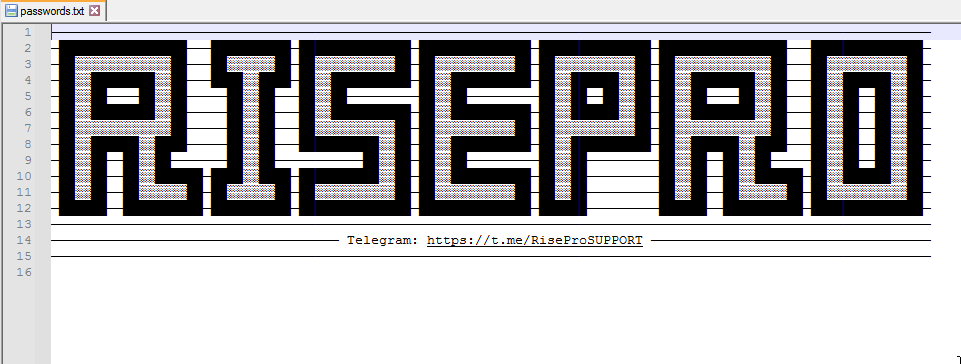
The information is stored in a file named passwords.txt, in which the name of the malware and its telegram address are included at the beginning.
How to deal with and clean the system?
Padvish antivirus detects and removes this malware from the system.
To prevent potential infection caused by this malware, it is recommended to avoid downloading files from unreliable sources that could lead to system infection.