Overview
Type: Trojan
Degree of destruction: Moderate
Prevalence: High
What is a Trojan?
Trojans are malware types that introduce themselves as healthy and legal software and act similarly to practical and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching it to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible
What is Trojan.VBS.Neoreklami malware?
Trojan.VBS.Neoreklami is a Trojan downloader that starts downloading all types of Trojans and adds them to the Windows Defender whitelist as soon as entering the system.
Technical explanation
Sign of infection
There are several signs of infection as follows:
- A “.exe” file with a random name inside a folder with a random name in the \C:\ Windows\Temp
- Wsf files with random name inside a folder with random name in the \C:\ ProgramData
- Dll files with random names inside a folder with random names in the \C:\Program Files (x86) for 64 bits OS and \C:\Program Files for 32 bits OS.
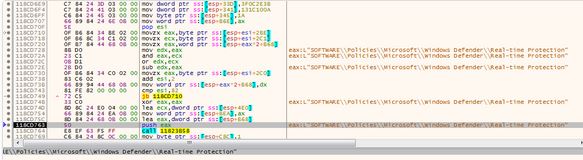
- Deactivating Windows Defender continuous protection by creating the following key:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection
And adding value 1 to DisableRealtimeMonitoring
- Excluding created files for Windows Defender by creating the following keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows Defender\ Exclusions\Paths
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\ Exclusions\Paths
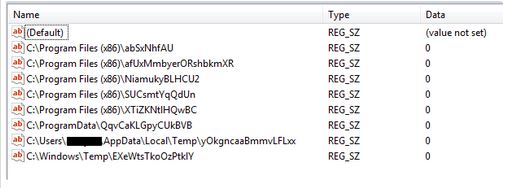
- Changing default performance for some specific malware by creating the following keys
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsDefender\Threats\ThreatIdDefaultAction
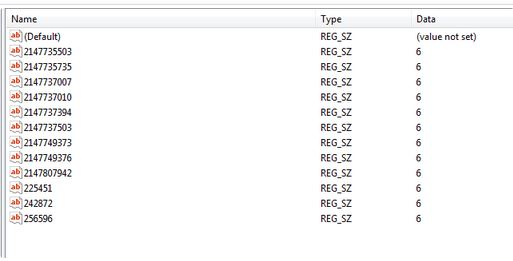
These values are some threat identification that is detected by Windows Defender and each shows a sign of different malware.
For instance: 2147735503 identification relates to the Trojan:Script/Wacatac.B!ml threat or 2147735735 identification relates to Trojan: Win32/Casur.A!cl.
It set the default performance value for each one of these threats on 6 which means it lets the detected threats perform.
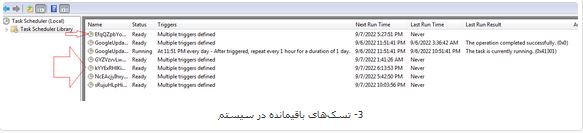
Multiple tasks with random names in the C:\Windows\System32\Tasks that each has to run dll and wsf files by the malware. Their running times are after the user’s log-on time at specific hours during the day.
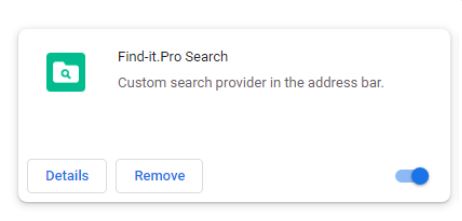
Creating new extensions on Chrome, Opera, Firefox, and Microsoft Edge through Find-it.Pro name. The malware changes the browser’s home page to the following link:
https://find-it.pro/?utm_source=distr_m
Performance
The malware creates a wsf formatted downloader file with obscured code.
Then it will extract 2 addresses from these files that http://www[.]testupdate[.]info/updates/ya/wrtzr_ytab_a_1/win/version.txt contains the version value of the malware.
The malware uses the second address to download an audio file that contains the embedded malicious code.
http://www[.]testupdate[.]info/updates/ya/wrtzr_ytab_a_1/win/upgdate_e.jpg
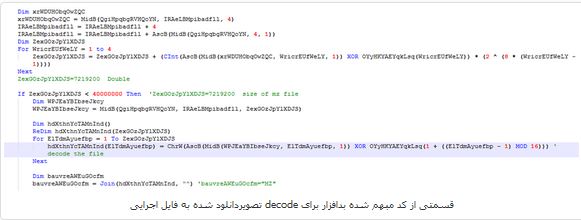
After running the exe code and decoding its contents inside the memory, the deactivating of Windows Defender continuous protection will begin. View the path of decoded contents in the memory in the following figure.
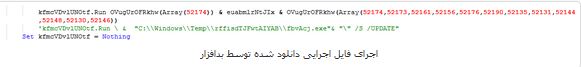
Then it extracts a code that is encoded with the base64 algorithm.
Now, the malware creates a registry settings file “Registry. pol” in \C:\Windows\System32\GroupPolicy\Machine and adds the abovementioned extracted key content, then extracts a base64 code with the software contents.
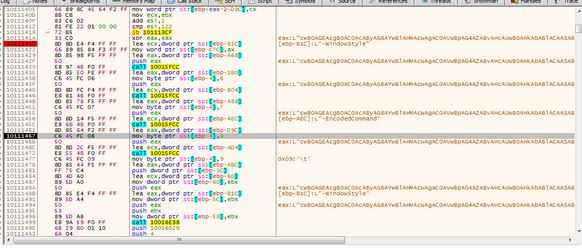
Then, it will run the first task with the following commands:
schtasks /CREATE /TN “groomer” /SC once /ST 00:08:28 /F /RU “analysis” /TR “powershell -WindowStyle Hidden -EncodedCommand cwB0AGEAcgB0AC0AcAByAG8AYwBlAHMAcwAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIABnAHAAdQBwAGQAYQB0AGUALgBlAHgAZQAgAC8AZgBvAHIAYwBlAA==”
The mentioned task runs with “schtasks /run /I /tn “grxOaQmer command.
Also, the decoding result will be the task contents of the following command:
Start-process -Window Style Hidden gpupdate.exe /force
Then, the created dll exclusion path codes will be added again to the Registry.pol file and creates a new task with the same above PowerShell contents and will be wiped off the system finally.
Then, all related codes to these keys will be obscured and added to a wsf file, then the malware adds the find-it.pro extension to all four browsers on the system.
Also, it extracts dll file contents and adds them to the mentioned paths. After that, it creates the related tasks to the mentioned dlls.
Actually, in every “log on” attempt, each one of the dlls runs at a specific time to make the detection impossible for Windows Defender.
How to encounter and disinfect the system
Padvish Antivirus can detect and remove Neoreklami malware from your system. To prevent any system infection by these types of malware it is recommended to avoid clicking on suspicious links and scan all files before execution. Keep your antivirus and OS updated all the time.