General Explanation
Type: Trojan
Degree of destruction: average
Prevalence: average
What is a Trojan?
Trojans are malware types that introduced themselves as healthy and legal software and act similarly to practical and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching it to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is SmsPay.Caco333 malware family?
There is a bunch of infected applications on authorized android markets such as Café Bazaar, Myket, ect, in addition to other websites and unauthorized markets, Telegram channels, or SMSs containing infected links that are made to steal users’ financial accounts and phishing. This malware looks like a useful and legal application but in action, not only it represents no positive services but also it steals users’ data using phishing.
A family of this malware has the “Caco333.ca” package name. The procedure of this kind of malware is that they claim to represent multiple services such as accessing official notices, free internet traffic, ect. In return and on a shoestring, it transfers the user to the fake bank gateway. As soon as the user enters financial account information and clicks on the payment button, all user’s bank card data will be sent to the attacker’s server along with receiving the demanded price, thus it steals all banking pieces of information of its victims.
These applications are designed both as an internet gateway and as an application.
- Internet gateway
The procedure of this malware is that it will send a “To follow up with the official notice you must refer to the link attached in the text of the SMS” message. As soon as the user clicks on the link, the displayed contents require the user to pay very little money, and for this matter, the user must enter a mobile number and ID number that will direct the user to the fake gateway.
Users must consider that the sent SMSs from the judiciary contain no links, and it’s just a method that attackers use to transfer the user to their fake gateway.
A sample of real messages from the judiciary:
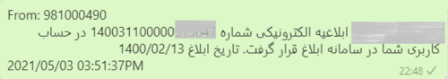
The main link of “following up complaints” from the judiciary is:
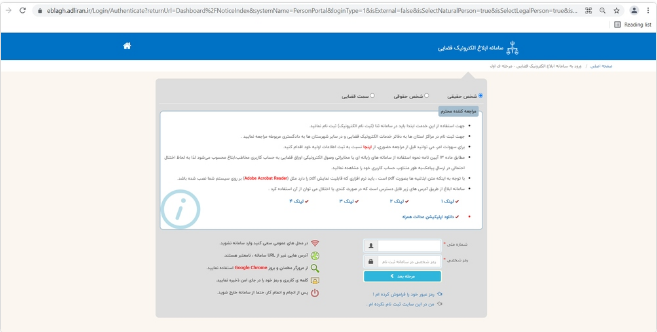
The fake link of “following up complaints” is “hxxps[:]//eblagh-app[.]gq”. Then after the user enters information related to mobile and ID number, the malware will send this information to its infected server. There will be no errors even if you enter the wrong mobile number.
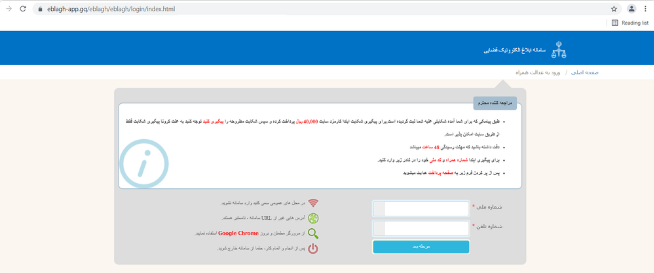
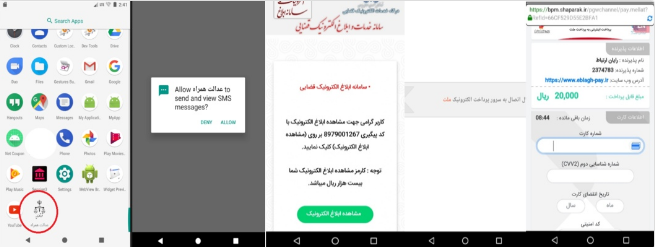
Sample of application
Here we will analyze the fake “Edalat-e-Hamrah” application.
Technical Explanation
This application downloads the displayed pages along with receiving the user’s data through an online connection with its infected server (hxxps[:]//eblagh-app[.]gq). It uses the “httputils” library to connect with its server, and in the end, it collects data with the PostString method in the form of a PHP file and sends them to its infected server.
Caco333.ca.main the main activity
The application will fetch two url.txt and Lmain.bal files from the application asset path as soon as it is executed.
url.txt: the file contains “hxxp[:]//eblagh-iranian[.]cf/winston/pay/mellat/index.html” link. Application activities are all web-view-based. Immediately, after launching the application, it receives access permissions such as “android.permission.READ_SMS”, “android.permission.RECEIVE_SMS” and “android.permission.WRITE_SMS”. Then, it shows the user a message that the fee for viewing the official notice is twenty thousand IRR, and the user will immediately refer to the fake gateway of Mellat bank “hxxp[:]//eblagh-iranian[.]cf/winston/pay/mellat/payment.mellat/index.php” by clicking on “view electronic notice” button. Therefore, the page address which displays to the user inside the activity is “https://bpm.shaparak.ir/pgwchannel/pay.mellat?RefId=66CF529D55E2BFA1” which is a set image from the malware server to display inside the activity. The attacker opens the URL inside the webview instead of opening it directly in the browser which is hidden from the sight of the user.
If the user enters bank card information, the malware will transfer this data along with a disposable password received from the bank to its infected server. As such, the user will give the total data of the bank account to the attacker along with paying the demanded fee. An attacker with total access to a user’s data can easily access any messages if the dynamic password is being sent to the user. In this method, the attacker will seduce the user’s bank account without notice.
Lmain.bal: the information related to layout, and it’s the method the existing widgets inside the activity are placed. Then, the following services will be executed:
Caco333.ca.install_caco333 service
Immediately after uploading the layout related to the activity, the install_caco333 service will run inside the activity to download and display page information. The malware checks if the application is installed correctly to perform the rest of the destruction activities correctly. It goes to the application install path (data/data/caco333.ca/files) and searches for the “29209 dj20d392j3dk0jirjf0i3jf203” file. If this file exists, the application will proceed, else it creates the “29209dj20d392j3dk0jirjf0i3jf203” file inside the installation path (data/data/caco333.ca/files) with the “29209dj20d392j3dk0jirjf0i3jf203” value.
The malware downloads its desired PHP file, and after that (JobDone), it will then use the GetString function and places all sources inside an ‘install_caco333._vvvvvvvv4’ string variable. Now by having source codes, the malware can easily use the GetElement function on any value with WebViewExtras. First, it will check the “open” string value that collects critical data from the user’s phone, and it will send this data as a string variable to its server using the postString method.
Firebasemessaging service
This service acts as a connection bridge between the malware and the phone. The malware receives notifications from Google firebase by the fm_messagearrived() method and executes the following commands:
If “cmd=clipboard” and “time=text+android_id” then it will collect all copied contents into a clipboard and send this information along with the exact time of the phone.
If “cmd=vibrate” then it checks how long the phone will be set on vibrate.
If “cmd=hide”, and “time=apk+android_id then the malware icon will be hidden and it will run its services in the background. Also, it sends the secretion message of the application icon to the malware server along with the “android_id” command which is the user’s phone specifications.
If “time=phone” and “cmd=mute” then it will silence the phone (without vibration)
If “time=phone” and “cmd=vibr” then it will silence the phone (with vibration)
If “cmd=app” and “time=get” then it will collect a complete list of all installed applications on the user’s phone (-versioncode, -versionname, and –packageName) and will send them to its server.
If “cmd=List” then it collects the model of the phone, the device signature, and the network operator.
If “cmd=crash” and “time=app” then automatically exits the application.
If “cmd=sendmessage” then the attacker can send long SMS (SMS_SEND) and receive its delivery report (SMS_DELIVERED) using PNSMS class and send() method. Also, it can check the status of SMSs for when there’s no possibility to send any messages such as when the phone is in “No Service” status, “NullPDU” when the text of the message is long, or “Radio off” when there is no possibility to send any messages. The attacker also can send an SMS to a specific phone number. When the malware receives the “target address” command for its server, the attacker can send an SMS to a certain number and receive the report to know whether the message was sent.
Sending long messages along with receiving the sending report is the result of the PNSMS function
Sending short or long SMS
Receiving the error message related to SMS delivery (like airplane mode, losing frequency, lack of enough battery charge, ect.)
Receiving the report of SMS delivery status
Receiving all results independently for each stage related to long SMSs
Sending SMS to a specific number and receiving the delivery status:
True: it will send the “success=sms send Now Form&” message along with the user’s phone model to the malware server if the SMS is sent correctly.
False: it will send the “success=sms cannot send From&” message along with the user’s phone model to the malware server if the SMS failed to be sent.
Caco333.ca.sms_caco333 service
According to “android.provider.Telephony.SMS_RECEIVE” which is defined as “sms_caco333$sms_caco333_BR” for the receiver, the malware runs its services and collects the following data related to received SMSs as soon as it receives the SMS:
The contents of receiving SMSs are the sender’s phone number, the user’s phone model, the network operator, and phone settings.
In the end, the malware runs the Fullsms_caco333 to gain full access to all sent/received SMSs in the victim’s phone.
Fullsms_caco333 service
According to the “android.intent.action.BOOT_COMPLETED” action that is defined as “fullsms_caco333$fullsms_caco333_BR” for the receiver, the malware runs its service, collects the following information from sent/received SMSs, and upload them all as a file in its Telegram Bot as soon as the android OS is boot:
According to the value of “anywheresoftware.b4a.phone.SmsWrapper” class:
If “personID!= 1″, then it will completely access the text of the user’s SMSs instead of “Sent” and “Receive” strings, creating a list of their information (e.g. the type of the message, the text of the message, phone number, the date of send/receive) and store them inside the file installation path (data/data/caco333.ca/files) along with the same date as a “txt” file extension. It uses the “PNUploadFile” library to update photos and files inside the host with no limits. The attacker will upload its desired text file in addition to other complementary information such as the date, time, phone model, and device ID) in its Telegram Bot using the POST method and “android” specifications.
Telegram API Bot: it has different methods to exchange information such as:
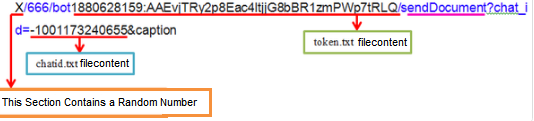
SendDocument: malware uses this method to send files (gif-zip-pdf) to its Telegram bot that has different parameters such as ‘chatid’ which sets unique specifications of the user or the username of the desired channel.
getUpdate: a method for updating Telegram Bot. It specifies its Telegram Bot address using “Token”, SendDocument” and “Chatid” methods which have already been written inside “chatid.txt” and “token.txt” files:
How to deal with this malware and disinfect the system
Install and update the Padvish Antivirus database file, and scan your device to assure your device is not infected by malware.
How to prevent the device from infection:
- Avoid downloading and installing the application from unauthorized sources and stores
- Pay attention to the access permissions when installing an application
- Continuously back up files and stored data
- Do not use unofficial versions of the application. There are many unofficial versions of applications such as Instagram and Telegram that are distributed through telegram channels.