General Explanation
Type: Miner
Degree of destruction: average
Prevalence: average
What is a Miner?
Miners are individuals or software that extracts cryptocurrencies or mine them. Bitcoin is a type of cryptocurrency. Extract bitcoin is a kind of data confirmation that performs in two difficult stages of the SHA256 hash. Bitcoin network rewards extractors with bitcoin for their attempts to calculate complex calculations. Malware writers write malware to use the victim’s system to mine bitcoin and pay no price for these calculations. Calculating these calculations will involve the CPU of the victim’s system and slow down the system.
What is CLRMiner malware?
CLRMiner malware is one of the new malware in extracting cryptocurrencies. This malware uses sqlserver.exe of Microsoft SQL Server to download and execute Miner malware. Access to the SQL Server through the network and running Queries are the reasons for infecting malware.
Technical Explanation
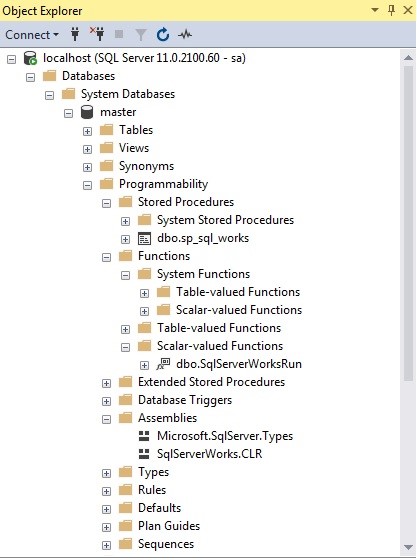
This malware executes the harmful file by creating a Procedure in SQL Server. Then sqlservr.exe will run downloaded miner files by executing these harmful files.
Signs of infection
- Files such as sqlconn.exe, SqlBase.exe, data.mdf, and ver.txt in the following path:
%programfiles%\Microsoft SQL Server\MSSQL[11].MSSQLSERVER\MSSQL\DATA\SQLBASE
- Executing SqlBase.exe and sqlconn.exe under the dominance of sqlservr.exe
- A file named SqlServerWorks.CLR in Asseblies folder
- A function named SqlServerWorksRun in Scalar-Valued Functions folder
- A Procedure named sp_sql_works in the Stored Procedures folder.
Malware uses the following URL to download SqlBase.exe file:
hxxp://dl[.]love-network[.]cc
Explaining the action
- The created Procedure executes SqlServerWorksRun every two minutes.
- SqlServerWorksRun function leads to execute the Run function of SqlServerWorks.CLR in the Assemblies folder.
In the following image, you can see the contents of the created file in the Assemblies folder:
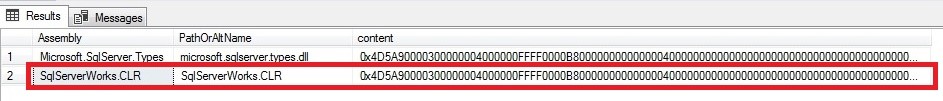
Finally, executing SqlServerWorks.CLR file results in download and running the SqlBase.exe file. The sequence of SqlServerWorks.CLR functionality is:
- First, if among all executing processes, the Taskmgr or SqlBase is running, the malware will stop its execution otherwise the malware will create the following directory:
%programfiles%\Microsoft SQL Server\MSSQL[11].MSSQLSERVER\MSSQL\DATA\SQLBASE
- It will download and execute SqlBase.exe file
- sqlcmd.exe will execute SqlServerWorkRun function
How to deal with it and disinfect the system
Padvish antivirus IPS prevents these kinds of network attacks and blocks its connection with the server. Also, it detects the downloaded files by this malware. It is recommended to install Padvish to prevent the infection of this malware.