General Explanation
Type: Trojan
Degree of destruction: high
Prevalence in Iran: high
What is Trojan?
Trojans are malware types that introduced themselves as healthy and legal software and act similar to useful and applicable software but cause many destructions to the system when executing. The downloaded software from the internet, placing HTML text, attaching to an email, etc. are ways that Trojans are using to enter the system. Contrary to viruses and computer worms, Trojans are not reproducible.
What is BreakWin malware?
Trojan.Win32.BreakWin is a Trojan that is designed for Windows and does not reproduce itself, but disables clients in the Microsoft active directory-based networks and removes their data. This malware needs auxiliary tools or manual distribution.
Technical Explanation
Signs of infection
- Disability of network card
- Removing the system from the active directory
- Changing the system password
- Changing the desktop background and displays suspicious message instead of boot
- Destructing the boot (boot.ini and BCD)
- Wiping the Hard Disk information
This malware contains multiple modules and different parts such as executive applications, scripts, and configuration files. Also, there are some unharmed tools such as WinRAR and SysInternals of Microsoft is in this malware package.
Describing the action
Modules and sequences of the malware actions:

The malware starts its actions by adding a file in the domain server named “setup.bat” and creates and schedules a task to execute this file by Group Policy.
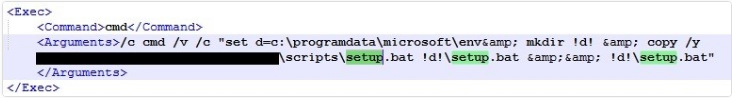
Describing the action of the setup.bat file
This file removes the AnalyzeAll task from the following path:
\Microsoft\Windows\Power Efficiency Diagnostics\
Then the malware copies and opens the enc.cab file from the previous path into the c:\programdata\microsoft\env path. The env.cab file can have other names in different versions of this malware with different paths. This file will be as Private.cab in another type of this malware. The env folder (Private) contains three files: programs.rar, update.bat, and Rar.exe.
Then it executes the update.bat file which is in the env folder with the following entry arguments:
Start /b "" %dirPath%\update.bat hackemall %dirPath% %dirPath%\env.exe
%dirPath%: c:\programdata\microsoft\env
The entries of update.bat file are:
- hackemail: password of all compressed files
%dirPath%: theC:\Programdata\Microsoft\env%dirPath%\env.exe
Explaining the action of the update.bat file
This file checks the C:\Windows\Temp\ for _lock6423900.dat file and will end its execution if this file exists. Otherwise, it will open the programs.rar file which has three files: ms.rar, bcd.rar, and cache.bat. Then it will execute the cache.bat file.
Explaining the action of cache.bat file
This file disables the network cards of the current system. Then it will search for Kaspersky antivirus on the system. If the system has Kaspersky antivirus the malware will end its scripts.
Explaining the action of the bcd.bat file
After executing the cache.bat file, the malware opens the bcd.rar file with its files: Bcd.bat and sync.exe. Then the updat.bat file executes the Bcd.bat file. It creates a new boot.ini file to replace the original boot.ini (this file existed in the Windows version before Vista) file in the Windows drive to prevent the system from a reboot. Then, it interrupts the reboot of the system and then removes the system events by deleting the identifiers of the BCD file in the BOOT folder of the Windows drive (this file is related to system boot settings). Finally, it writes the contents of the memory cache in the hard disk by executing the sync.exe file which is one of the tools of Sysinternals.
After executing the bcd.bat file, the update.bat file will open the ms.rar file which contains:
- mscap.bmp
- mscap.jpg
- msconf.conf
- msrun.bat
- mssetup.exe
- msuser.reg
- msmachine.reg
Then update.bat file moves the Msapp.exe file from “C:\programdata\microsoft\env” to the ms folder. Then it will execute the msrun.bat file.
Explaining the action of the msrun.bat file
This file transfer all aforementioned files to “C:\temp“. It creates a ScheduledTask named mstask for msapp.exe file as follows:

In other types of this Malware the ScheduledTask (mstask) have the following contents:
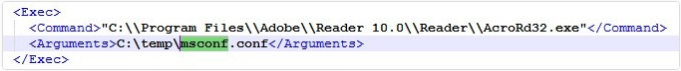
As you can see in the above figure, it used the AcroRd32.exe instead of the msapp.exe file.
Explaining the action of the msapp.exe file
Executing this file will lock the system and changing the password. To execute, this file takes the msconf.conf as the entry argument. In the following, you can see the decoded commands of msconf.conf file:

This file changes the system password to a random set of numbers, then if the Windows version is older than the Vista version, it will destroy the boot.ini file. If the Windows version is newer than the Vista version, it will destroy the bcdedit values which disables the loading of the OS. Also, it disconnects the system from the domain by running the following command:
C:\Windows\System32\cmd.exe /c wmic computersystem where name="%computername%" call unjoindomainorworkgroup
Also, it wipes the hard disk by paths it specified as a hardcode for itself in the “conf” file. This file after executing these actions will close the current session and logs out to force to change the password and prevent the user from re-entering the system. Whenever the user restarts the system, even if the user enters the correct password, the system will display the boot error message. In the following figure you can see a scheme of the BCD file after restarting the infected system:

Explaining the action of mssetup.exe
This file only locks the screen and disable the entry tools so to:
- Disable the possibility of sending commands through mouse and keyboard.
- Show a black Window that covers the whole screen and has the malware image in between.
Explaining the action of nti.exe
In some types of this malware, the update.bat file in addition to all mentioned activities will also execute the nit.exe file. Executing this file will infect the MBR and its next 17 sectors. Also, in sector 34th, it will XOR “7” with the main MBR value and writes it down.
The contents of infected sectors (in fact, they are the written sectors by NoPetya malware) in this malware, and the only message that will display to the user will change by the current malware, and other codes are intact.
At last, it will disable the boot possibility by encoding MFT to destroy the disk.


MBR content is clean

MBR content after infection
How to deal with it and disinfect the system
Padvish Antivirus will detect and disinfect this malware. Also, MBR protection of Padvish will prevent any harm or destruction and will notify the user by showing the proper message if any malware attempts to change the MBR contents.
If there are any signs of infection to this malware you need to do as follows:
- Check all administrator-level accesses to the active directory and change all passwords immediately. Also, pay close attention to login scripts and startups.
- Limit the remote access to the network other than typical working hours and use VPN (based on software private key or Token) instead of connecting directly to the server.
- Check all incident record systems of the network along with all security incidents and system configurations.
- Back up regularly on trusted, offline systems.