General explanation
Type: Vulnerability
Vulnerability platform: Oracle WebLogic Server
Vulnerability versions: 10.3.6.0.0- 14.1.1.0.0
The date of representing of the patch by Microsoft: October 2020
Vulnerability module: Console Component
Vulnerability type: Unauthenticated Remote Code Execution
Degree of destruction: high
Used Malware:
- Miner.Win64.CoinMiner.a
- Trojan.Win32.DarkIRC.Ss1
What is Vulnerability?
In computer security, Vulnerability is a defect inside a platform that can be seduced by an intruder or malware and provide unauthorized access to the computer system. Vulnerabilities allow the intruders to execute instructions, access system memory, install malware and steal information, destruct and change important information of organizations and individuals.
What is CVE-2020-14882 vulnerability?
This vulnerability has a very high degree of danger (CVSS 9.8) and it is inside the component of the Oracle Weblogic Server software console. The intruder can use this vulnerability to have remote code access to this server by HTTP protocol and port 7001 which belongs to Weblogic Server and run its desired instructions.
The intruder performs its malicious actions and only sends an HTTP request to this server which consists of malicious codes and needs no authentication in the Weblogic Server. The destructive codes for accessing an infected server can consist of executing a process such as cmd.exe with a high level of access or any other kinds of instructions.
Technical Explanation
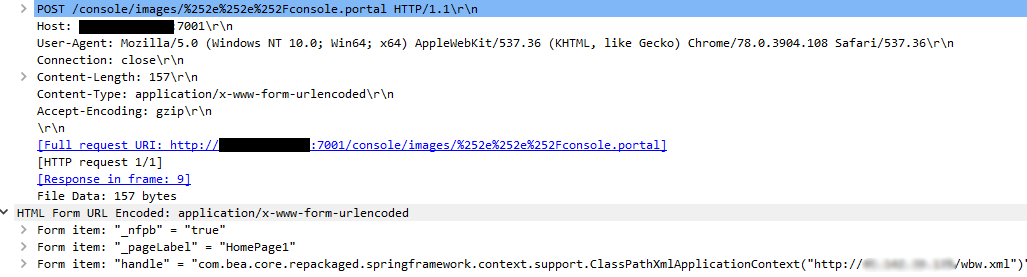
A sample of miner malware that used this vulnerability for its distribution, instructs its desired Weblogic Server to execute XML codes which leads to downloading a Powershell file and eventually results in a system infection. In the following image you can see how the malware uses this vulnerability:
Security recommendation
For being safe, restrict the access of the Weblogic Server admin portal to the local network and also make sure that it is updated with the last version of the provided patch.
How to deal with it
Padvish antivirus IPS (Intrusion Prevention System) detects all attempts to infect the system by these types of vulnerabilities and prevents them from entering the system.