General explanation
Type: Backdoor
Degree of destruction: average
Prevalence: average
Names of the malware:
- Backdoor.Win32.SunBurst (Padvish)
- BackDoor.SiggenNET (Padvish)
- Trojan.MSIL/Solorigate (padvish)
- Trojan:MSIL/Solorigate.BR!dha (Microsoft)
- HEUR:Backdoor.MSIL.SunBurst.gen (Kaspersky)
- Trojan.Sunburst.A (BitDefender)
- A Variant Of MSIL/SunBurst.A (Eset)
- TR/Sunburst.AO (Avira)
What is a backdoor?
Backdoors are applications that can make hackers able to bypass the system security mechanism and provide the intruders with different system resources. Hackers can enter the system and have no worries about usernames or passwords being changed by this method and without any authentication. Backdoor applications have different forms and hackers use them upon their needs to breach a system resource.
What is a backdoor infection of SolarWinds?
On December 20, 2020, SolarWinds company (software developer) revealed they are a victim of a cyberattack that led SolarWinds Orion version which was released between march 2020 and august 2020 to have a backdoor code. This backdoor allows the intruders to execute any commands on the Victim’s system and eventually on the network remotely if it can connect to the internet.
Estimates revealed that at least 18000 customers of official customers of this company installed the infected version. FireEye, many security and governmental organization in the USA, and at least 7 other countries were involved.
The following versions are SolarWinds Orion infected versions:
- 2019.4 HF 5
- 2020.2
- 2020.2 HF 1
If any versions of SolarWinds Orion – which we called- are installed on your system, it is necessary to analyze the network for any infection or breaches with high precision.
The high degree of danger of this backdoor makes encountering and analyzing the remote total control of the victim’s system, accessing all equipment and important network servers on the system that have the Orion installed, and the skill rate and complexity of the intruders hard. It is recommended to use expert forensic teams.
Technical explanation
The used scenario in the attack is that intruders use a supply-chain attack to reach their goals. In the supply-chain attacks, the intruder will detect used tools in its target network to make these tools his target without direct breach into the main target system. Since there is no exact control over software and equipment that use trusted sources, this type of attack can be dangerous.
SolarWinds Orion software is an NMS (Network Management System) that has been a target due to its installation in the network and is available to all network equipment and servers in many small and large networks globally.
As a result, everything that an intruder needed to do was to wait for enterprises to install this infected software on their system. The existing backdoor in this software is activated after 12-14 days after the vulnerable version has been installed and has contacted the intruder command and control server to receive its necessary instructions. The intruder easily chooses their victim by obtaining the name and complete information, then proceeds with his intrusion.
Note that all infected versions of this malware were released in the relevant time period and have SolarWind’s digital signature.
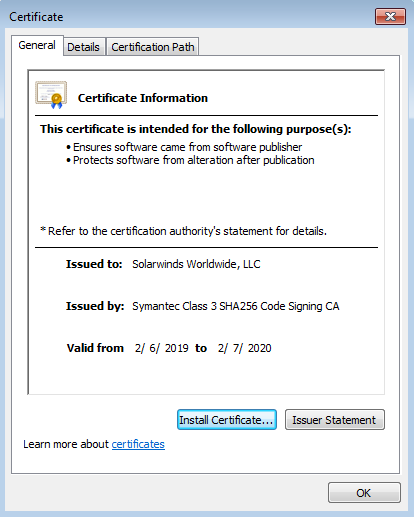
Figure 1- SolarWinds digital signature certificate
Infection specifications
- Updating Orion tool between March 2020 and December 2020 (this incident alone is the system infection specification and needs forensic analysis)
- Viewing connection with each one of the following addresses:
-
- avsvmcloud.com
- digitalcollege.org
- freescanonline.com
- deftsecurity.com
- thedoccloud.com
- …
3 Viewing connection to each one of the following IPs:
-
- 13.59.205.66
- 54.193.127.66
- 54.215.192.52
- 34.203.203.23
- 139.99.115.204
- …
How to deal with it and disinfect the system
Your network (not just the system that has the relevant tool installed) is susceptible to breach if you have updated any kinds of SolarWinds products during the mentioned period (March until December 2020), and removing or updating this software will not result in disinfection. Hence, it is necessary to seek help from relevant experts and perform a complete forensic of your network to detect and neutralize all probable infections and block all intrusion ways into your network as soon as possible.
- Create a Snapshot of the previous status of all systems on your network that are connected to SolarWinds company and contact an expert forensic team.
- Disconnect all management and monitoring software of the network from the internet and place them in a separate VLAN that has no connection with the internet (whether you use SolarWinds or any other products)
- Isolate the network includes affected systems
- Change all user passwords on the network level (this act must perform after isolation and at any cost, do not connect to infected systems with this new identity and data )
- Update the infected versions to the new version (December 15, 2020).
**If you use other SolarWinds products except for Orion, it is better to check all connections and update them to the latest released version as soon as possible.
Padvish Antivirus detected the infected versions of this software with the name Backdoor.Win32.SunBurst and the feature of IPS in Padvish prevent any connection from the network to this malware C&C.
Meanwhile, the Padvish forensic analysis team is ready to respond to all users and enterprises that need forensic analysis on their networks.