General Explanation
Type: PUA (Potentially Unwanted Application)
Degree of destruction: average
Prevalence: average
What is PUA?
These are malware that often includes adware or install toolbars or such aims but is not like other malicious malware. This category of malware maybe perform some actions which are not approved or expected by the user and are malicious but some users believe that the advantages of using these kinds of applications are more than their defects and consider the arbitrary use of them has no problem.
What is the Dnotua malware family?
This malware family includes famous applications such as Instagram, Golden Telegram, My Irancell, etc., and also applications related to useful objectives of the day such as teaching forex, forex oscillator, forex analyzers, Forex, Forex: beginner to advanced, etc. that are accessible to users for download on different android markets. Nominating applications is intriguing for the user to install the application, but mostly, the user must register in added-value services to use the application which has no relation to the nomination and will charge you a daily fee from your SIM card or they have in-app ads without the users notice.
Technical explanation
This application is distributed as “Teaching Forex”. according to the current situation of Forex, the download statistics of these kinds of applications from android markets are flourishing. Such these applications are applications related to forex, forex oscillator, forex analyzers, Forex, forex: beginning to advance, etc.
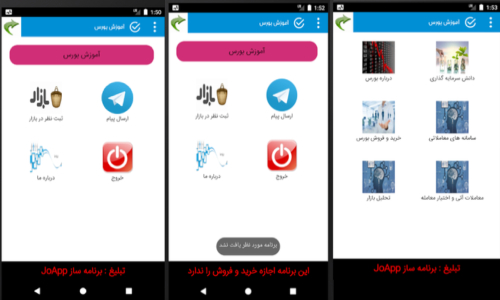
After executing the application and in its main action, all icons placed by the programmer and it was related to “sending the message” and “commenting on the market” will be disabled, and clicking the user “The application could not be found” will be appeared. This application is a simple software that loads and reads almost easily all of its data and information from the assets file of the application and the only thing is using the advertising package. The appeared advertising banner is related to “JoAPP application builder” which by clicking from the user, the advertising banner will be transferred to “bejo[.]ir”. Also, to show advertising it uses the connection to the “hxxp[:]//gamejoo[.]com/tabligh[.]html” address.
RssAvticity
To access the information of the day of this website in the application, RSS feeds have been used. Each site can have one or multiple RSS feeds with diverse topics. This tool is an abstract of site content in the format of understandable data for the user, however, its structure is based on XML language that is easily readable and understandable for different applications.
BookmarksActivity
Another goal of this malware is bookmarking URLs that the user connects with his/her cell phone.
How to deal with it and disinfect the system
To make sure that the system is safe, install Padvish Antivirus and keep its database file and scan it.
Methods of preventing phone infection
- Avoid downloading and installing any application from unauthorized resources/markets.
- Note the requested permissions, when installing the mobile application.
- Continuously back up your saved data and files.
- Do not use an unofficial version of applications. Applications such as Telegram, and Instagram have many unofficial versions and most of them release through Telegram channels.