General Explanation
Type: Ransomware
Degree of destruction: high
Prevalence: average
What is Ransomware?
Ransomware is a type of malware that attempts to encrypt important information of the user and blackmail to return the data to the users. Generally, the encrypting method could not be decrypted and is a common way to pay the ransom by using cryptocurrency, and the reason for it is being hidden and not recognizing the parties. In most ransomware, there is no way to return the file and users have no choice but to pay the price to have his/her files. Ransomware is one of the most malicious malware that causes heavy financial loss.
What is Filecoder malware?
Filecoder is a kind of Ransomware that encrypts the user’s phone by using the AES encrypting algorithm. The feature of this Ransomware is that it will add a “seven” extension to all encrypted files. Also, the user for returning its files to the early state, must pay “0.01” bitcoin to the attacker as hardcode in the specified code by the general encrypted address “16KQjht4ePZxxGPr3es24VQyMYgR9UEkFy” and have the payment. In the following, for payment, the private key to decrypt files from the infected server.
After installing the infected application in the user’s phone, the malware author releases the malware and infects more users, sending an SMS to all user’s contacts. The message text, according to phone settings will be sent in 42 different languages, one of which is Persian. The content of the message is: ” How can they put your photo in this app, I think I need to tell you”. In the following message, the link (http://wevx.xyz/sexSimulator.apk) for downloading the application is added. According to this topic, it can be recognized that one of the attacker’s aim countries is Iran.
Malware author performs maliciously to establish a C&C connection with its infected server and execute received instructions. But right now, due to the detection of the malware file, its servers have been disabled and as a result, the files of the user will not be encrypted one of the main signs of infection is that the background image of the phone will be changed which can be restored by the user and the phone will be disinfected by removing the application.
Technical Explanation
All existent data from “URL: https://pastebin.com/raw/LQwGQ0RQ” will be recalled by executing the main activity of the application and it will be stored in the string variable “C2Content” in the application database. The reason that the attacker uses the Pastebin service is to store the desired textual data for some time and whenever he/she desires to change it to dynamic. All addresses which are added to this server, are coded with the base64 algorithm. Malware author writes the application code in a way that if cannot receives addresses dynamically from the server, he/she will use the same hardcoded addresses which exist in the application codes.
The application service named MyService executed in the background with the following aims:
- By using an asynchronous encrypting algorithm, two private and general keys which are each other pairs will be created.
- General key: it is hardcoded in the application code and is existed in the string variable “hackPubKey”
- Private key: private and general keys (which are converted from hex2byte state) are encrypted by the RSA algorithm and the produced output will again encrypt with the base64 algorithm. The produced string value will be added to the application database.
- The malware author collects a full list of information about the phone’s contacts. This information will recall from the relevant file of the phone’s contact database and store in a JSON file. Eventually, it will send the JSON file to its server (=http://wevx.xyz/post.php?uid). By using C&C instructions will communicate with its infected server and according to the sent information, it will receive a series of operations in the user’s phone.
- An SMS will be sent to each user, who has a phone number.
It can detect a language from the phone settings. If the phone language setting is on the language list, the sent message text will be written accordingly, and if it does not exist on the list, the text “how can they put your photo in this app, I think I need to tell you” will be added by default. eventually, the infected link to download the application file:http://wevx[.]xyz/sexSimulator.apk will be added.
The process of encryption
The malware author creates an AES key. He/She will encrypt this key by using the public key and RSA algorithm and by having access permissions (WRITE_EXTERNAL_STORAGE , READ_EXTERNAL_STORAGE) and considering the following terms, he/she will collect a full list of phone files:
- The files should not be in a folder with “.cache” and “.temp” strings.
- The file extensions should not be “.rar” or “.zip” and should not exceed 51.200KB or 50 MB
- The file extensions should not be “.png”, “.jpg” or “.jpeg” and should not exceed 150 KB.
- The extensions of the collected files are as follows:
. “doc”, “.docx”, “.xls”, “.xlsx”, “.ppt”, “.pptx”, “.pst”, “.ost”, “.msg”, “.eml”, “.vsd”, “.vsdx”, “.txt”, “.csv”, “.rtf”, “.123”, “.wks”, “.wk1”, “.pdf”, “.dwg”, “.onetoc2”, “.snt”, “.jpeg”, “.jpg”, “.docb”, “.docm”, “.dot”, “.dotm”, “.dotx”, “.xlsm”, “.xlsb”, “.xlw”, “.xlt”, “.xlm”, “.xlc”, “.xltx”, “.xltm”, “.pptm”, “.pot”, “.pps”, “.ppsm”, “.ppsx”, “.ppam”, “.potx”, “.potm”, “.edb”, “.hwp”, “.602”, “.sxi”, “.sti”, “.sldx”, “.sldm”, “.sldm”, “.vdi”, “.vmdk”, “.vmx”, “.gpg”, “.aes”, “.ARC”, “.PAQ”, “.bz2”, “.tbk”, “.bak”, “.tar”, “.tgz”, “.gz”, “.7z”, “.rar”, “.zip”, “.backup”, “.iso”, “.vcd”, “.bmp”, “.png”, “.gif”, “.raw”, “.cgm”, “.tif”, “.tiff”, “.nef”, “.psd”, “.ai”, “.svg”, “.djvu”, “.m4u”, “.m3u”, “.mid”, “.wma”, “.flv”, “.3g2”, “.mkv”, “.3gp”, “.mp4”, “.mov”, “.avi”, “.asf”, “.mpeg”, “.vob”, “.mpg”, “.wmv”, “.fla”, “.swf”, “.wav”, “.mp3”, “.sh”, “.class”, “.jar”, “.java”, “.rb”, “.asp”, “.php”, “.jsp”, “.brd”, “.sch”, “.dch”, “.dip”, “.pl”, “.vb”, “.vbs”, “.ps1”, “.bat”, “.cmd”, “.js”, “.asm”, “.h”, “.pas”, “.cpp”, “.c”, “.cs”, “.suo”, “.sln”, “.ldf”, “.mdf”, “.ibd”, “.myi”, “.myd”, “.frm”, “.odb”, “.dbf”, “.db”, “.mdb”, “.accdb”, “.sql”, “.sqlitedb”, “.sqlite3”, “.asc”, “.lay6”, “.lay”, “.mml”, “.sxm”, “.otg”, “.odg”, “.uop”, “.std”, “.sxd”, “.otp”, “.odp”, “.wb2”, “.slk”, “.dif”, “.stc”, “.sxc”, “.ots”, “.ods”, “.3dm”, “.max”, “.3ds”, “.uot”, “.stw”, “.sxw”, “.ott”, “.odt”, “.pem”, “.p12”, “.csr”, “.crt”, “.key”, “.pfx”, “.der”
For all collected files in the list, each one of them will be encrypted separately as follows:
[(RSA { (AES)(Public key) } + (AES)(File)] + (.seven)
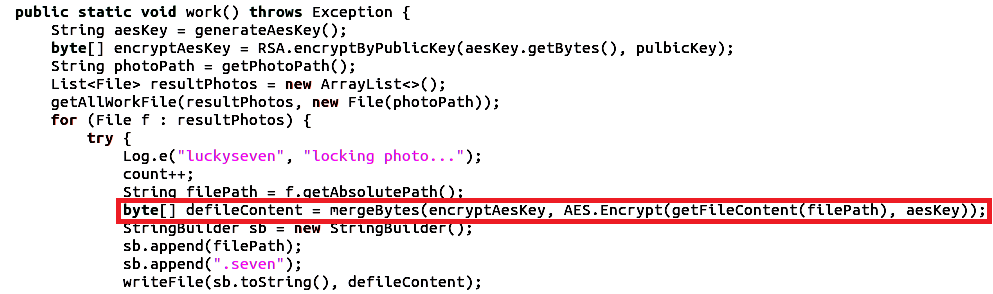
After encrypting the files, the “MainActivity” activity will be shown, we have two parts to this activity:
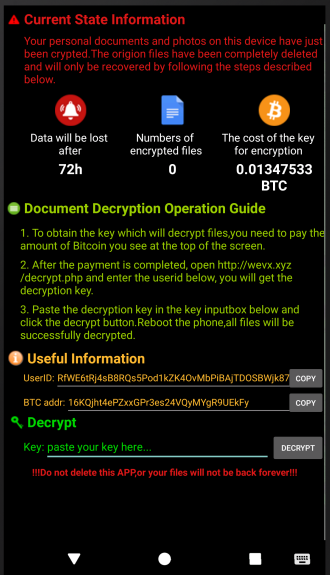
- UserID is the information of every individual which will be added to this field code.
- BTC addr: is the wallet address hashed and determined by the attacker, and if the user wants to take his/her files back should pay the ransom based on the determined price as bitcoin. The general encrypted address is “16KQjht4ePZxxGPr3es24VQyMYgR9UEkFy” which is coded and exists in the application. Malware author can attain this address as dynamic from the stored data in its “https://pastebin.com/raw/LQwGQ0RQ” server.
The attacker attains the UID of the application. To some extent, the requested ransom is dynamic. This section consists of two parts:
The first part will be the amount of the desired bitcoin from the user, which is 0.01. While the remaining numbers after the requested bitcoin amount are UID. This unique action is for creating an encrypted separate bitcoin wallet for each infected phone.
The process of decryption:
If the user wants to pay bitcoin at the mentioned address to recover the encrypted files, the getDecryptUrl function will be recalled after clicking on the Decrypt button.
As described above, also in this function malware author can dynamically use stored data in its “https://pastebin.com/raw/LQwGQ0RQ” server to access its desired address. But again, such as other addresses if the dynamic does not access the address, the user will refer to the hardcoded address (“https://pastebin.com/raw/LQwGQ0RQ”). As soon as the bitcoin has been paid, the UID of the user will be sent and in return, the private key related to phone file decryption will be sent to the user.
How to deal with it and disinfect the system
- This malware will be detected by Padvish Antivirus.
- Keep your phone up to date; ideally, set them to update automatically.
- Focus on access permissions of the phone. If it seems that they are too much for the application functionality, avoid installing the application.
- Pay attention to buying or downloading your applications from validated markets and do not download them from Telegram channels, Instagram pages, or invalid websites. Also, do not click on suspicious links that you have received via SMS.