General Explanation
Type: Worm
Degree of destruction: high
Prevalence: average
Names of the malware:
- Worm.Win32.Brontok.a
- Worm.Win32.Brontok.AP
- Worm.Win32.Brontok.fn
- Worm.Win32.Brontok.Qq
- Worm.Win32.Brontok.jlVB
- Worm.Win32.Brontok.proc
- Worm.Win32.Brontok.mm
What is the Worm?
Computer worms such as Brontok are types of malware that are capable of reproduction. For permanence, worms set ways to maintain the infection in each system boot. The prominent feature of worms is in their distribution which is generally performed through portable drives and shared directories in the network.
What is Brontok malware?
This malware which enters in victim’s system aim to perform DDoS attacks, in its first execution will execute copies of itself in different place of the system and creates registry keys for its maintenance.
This worm was released by email, share folder, and portable drivers. Also, it can disable antiviruses and other security programs in the victim’s system.
Technical Explanation
Signs of infection
This malware creates its files with fake names similar to the names of systematic tools in the %appdata% path.
“%appdata%\smss.exe”“%appdata%\services.exe”“%appdata%\lsass.exe”“%appdata%\inetinfo.exe”“%appdata%\csrss.exe”“%appdata%\winlogon.exe”
Also attempts to create the following files:
“%windir%\ShellNew\sempalong.exe”“%windir%\eksplorasi.exe”“%userprofile%\Start Menu\Programs\Startup\Empty.pif”“%userprofile%\Templates\Brengkolang.com”“[system32]\<username>’s Setting.scr”“[system32]\drivers\etc\hosts-Denied By-<username>.com”
This malware also creates its maintenance by correcting the Windows shell and registry RUN key:
“HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Bron-Spizaetus”Data:”%windir%\ShellNew\sempalong.exe”“HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell”Data: Explorer.exe “%windir%\eksplorasi.exe”“HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Tok-Cirrhatus”Data: “%appdata%\smss.exe”“HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System\DisableCMD”
Explaining the function of malware files:
This malware enters the victim’s system and aims to perform a DDoS attack.
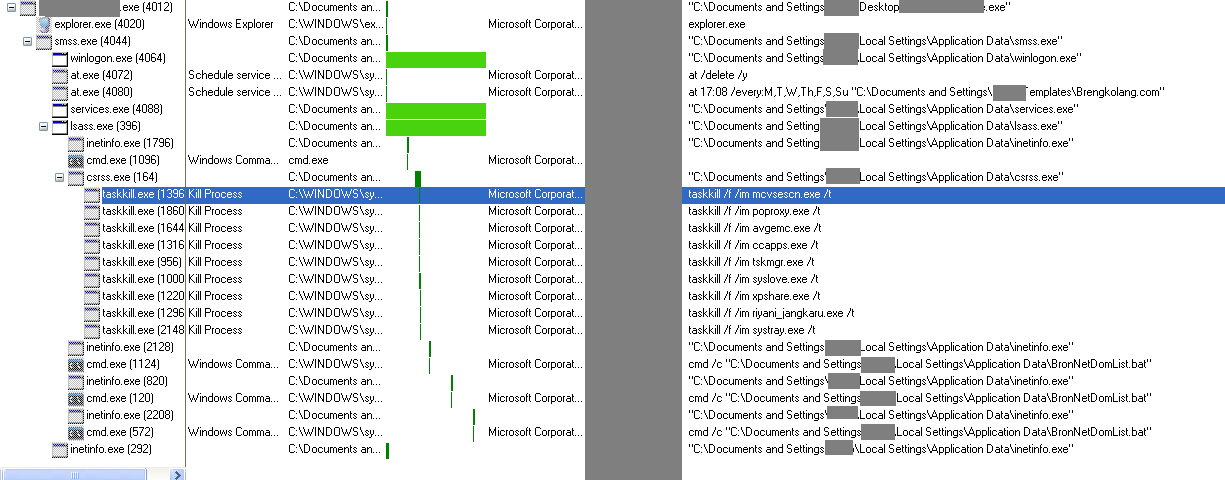
After creating maintenance for itself, the fake smss.exe file will be executed this process will execute other copies of the main process and in between, will remove all tasks which the system has built and then create a task aimed to execute one of its copies named Brengkolang.com; this task will execute the malware in every day of the week and on a certain time.
In the following, a process name csrss (which is a copy of the main malware) will kill the following processes.
- mcvsescn.exe
- poproxy.exe
- avgemc.exe
- ccapps.exe
- tskmgr.exe
- syslove.exe
- xpshare.exe
- riyani_jangkaru.exe
- systray.exe
In the above list, you can see the names of all processes which belong to antiviruses. For example, mcvsescn.exe belongs to McAfee VirusScan E-mail and also poproxy.exe file belongs to Norton Antivirus protection suite.
Also do not send emails to addresses that involve the following strings.
SECURE – SUPPORT – MASTER – MICROSOFT – VIRUS – HACK – CRACK – LINUX – AVG – GRISOFT – CILLIN – SECURITY – SYMANTEC – ASSOCIATE – VAKSIN – NORTON – NORMAN – PANDA – SOFT – SPAM – BLAH – YOUR – SOME – ASDF – @. – .@ – WWW – VAKSIN – DEVELOP – PROGRAM – SOURCE – NETWORK – UPDATE – TEST – .. – XXX – SMTP – EXAMPLE – CONTOH – INFO@ – BILLING@ –.ASP – .PHP – .HTM – .EXE – .JS – .VBS – DOMAIN – HIDDEN – DEMO – DEVELOP – FOO@ – KOMPUTER – SENIOR – DARK – BLACK – BLEEP – FEEDBACK – IBM. – INTEL. – MACRO – ADOBE – RECIPIENT – SERVER – PROXY – ZEND – ZDNET – CNET – DOWNLOAD – HP. – XEROX – CANON – SERVICE – ARCHIVE – NETSCAPE – MOZILLA – OPERA – NOVELL – NEWS – UPDATE – RESPONSE – OVERTURE – GROUP – GATEWAY – RELAY – ALERT – SEKUR – CISCO – LOTUS – MICRO – TREND – SIEMENS – FUJITSU – NOKIA – W3. – NVIDIA – APACHE – MYSQL – POSTGRE – SUN. – GOOGLE – SPERSKY – ZOMBIE – ADMIN – AVIRA – AVAST – TRUST – ESAVE – ESAFE – PROTECT – ALADDIN – ALERT – BUILDER – DATABASE – AHNLAB – ROLAND – ESCAN – HAURI – NOD32 – SYBARI – ANTIGEN – ROBOT – ALWIL – YAHOO – COMPOSE – COMPUTE – SECUN – SPYW – REGIST – FREE – BUG – MATH – LAB – IEEE – KDE – TRACK – INFORMA – FUJI – @MAC – SLACK – REDHA – SUSE – BUNTU – XANDROS – @ABC – @123 – LOOKSMART – SYNDICAT – ELEKTRO – ELECTRO – NASA – LUCENT – TELECOM – STUDIO – SIERRA – USERNAME – IPTEK – CLICK – SALES – PROMO
Malware will monitor the title of the opened windows in the system. Each window that contains the following title results in a system reboot.
- REGISTRY
- SYSTEM CONFIGURATION
- COMMAND PROMPT
- .EXE
- SHUT DOWN
- SCRIPT HOST
- LOG OFF WINDOWS
- KILLBOX
- TASKKILL
- TASK KILL
- HIJACK
- BLEEPING
As said before, malware enters the system aiming for a DDoS attack and the attack of this malware was the “ping of death” which by sending ICMP packets to the desired server with a 747-byte buffer will interfere in server servicing.
The malware will release in three ways:
- By portable drives
As you can see in the following image, malware will create a copy of itself in every folder with the name of the user’s information (for example data+username).
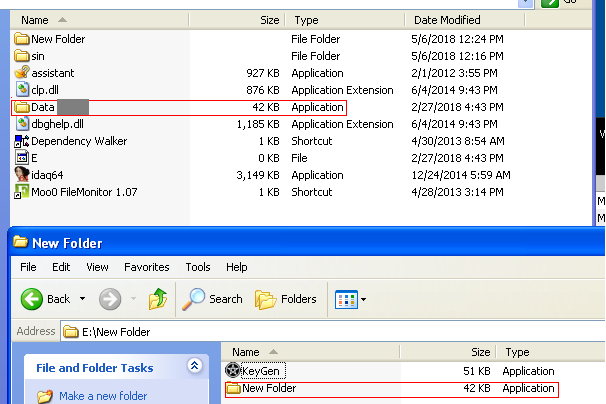
- It will attach itself to emails and will send them.
- It will copy itself into the shared folders of the system.
How to deal with it and disinfect the system
Padvish Antivirus by using a real-time scanner of shared drives and folders in the network will monitor the examples of this malware and disinfect them. Also having UMP capability which is a part of behavioral protection, will prevent the system from being infected by a portable driver. So to prevent infection from this method of transferring such as this malware, it is recommended to install Padvish.